TryHackMe: Capture
Published in 05-08, 2023

LINK : Capture room
- Let’s scan our target.
# nmap -sC -sV -T4 10.10.78.63
Starting Nmap 7.92 ( https://nmap.org ) at 2023-05-06 16:33
Nmap scan report for 10.10.78.63
Host is up (0.10s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Werkzeug/2.2.2 Python/3.8.10
We have one open port which is HTTP server running on port 80.
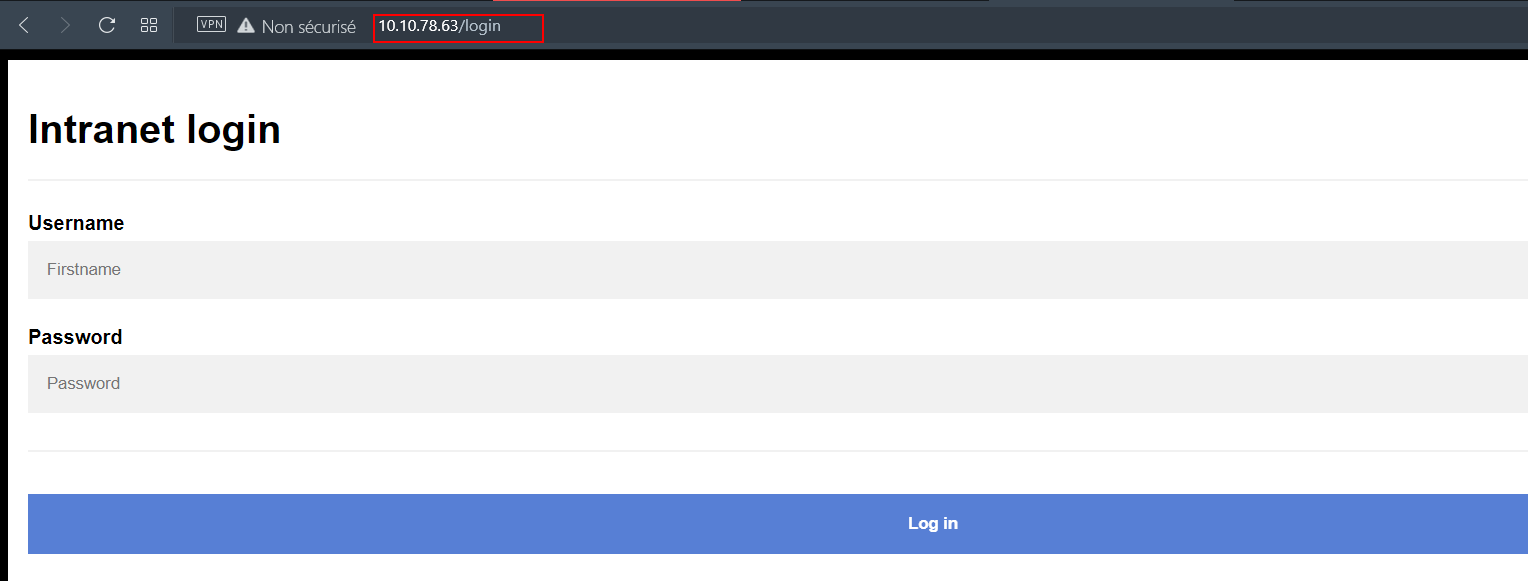
After you navigate to the web page you will be redirected to a login page http://10.10.X.X/login
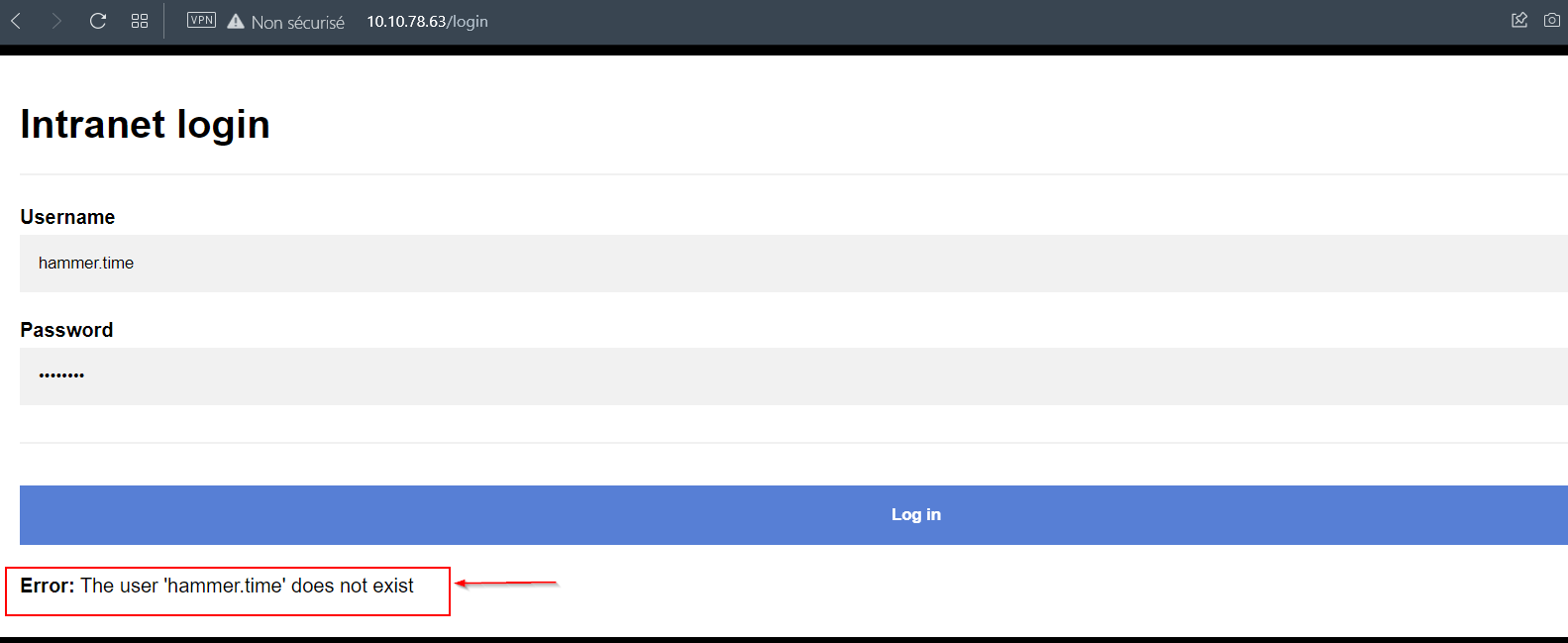
- After you try to login using a random username, you will see an error message “The user ‘X’ does not exist”, so the applicaton is vulnerable to username enumeration.
Since the the room comes with two attached files that contains usernames list and passwords list, we will use them to find a valid username then we will start brute forcing the password with that valid username.
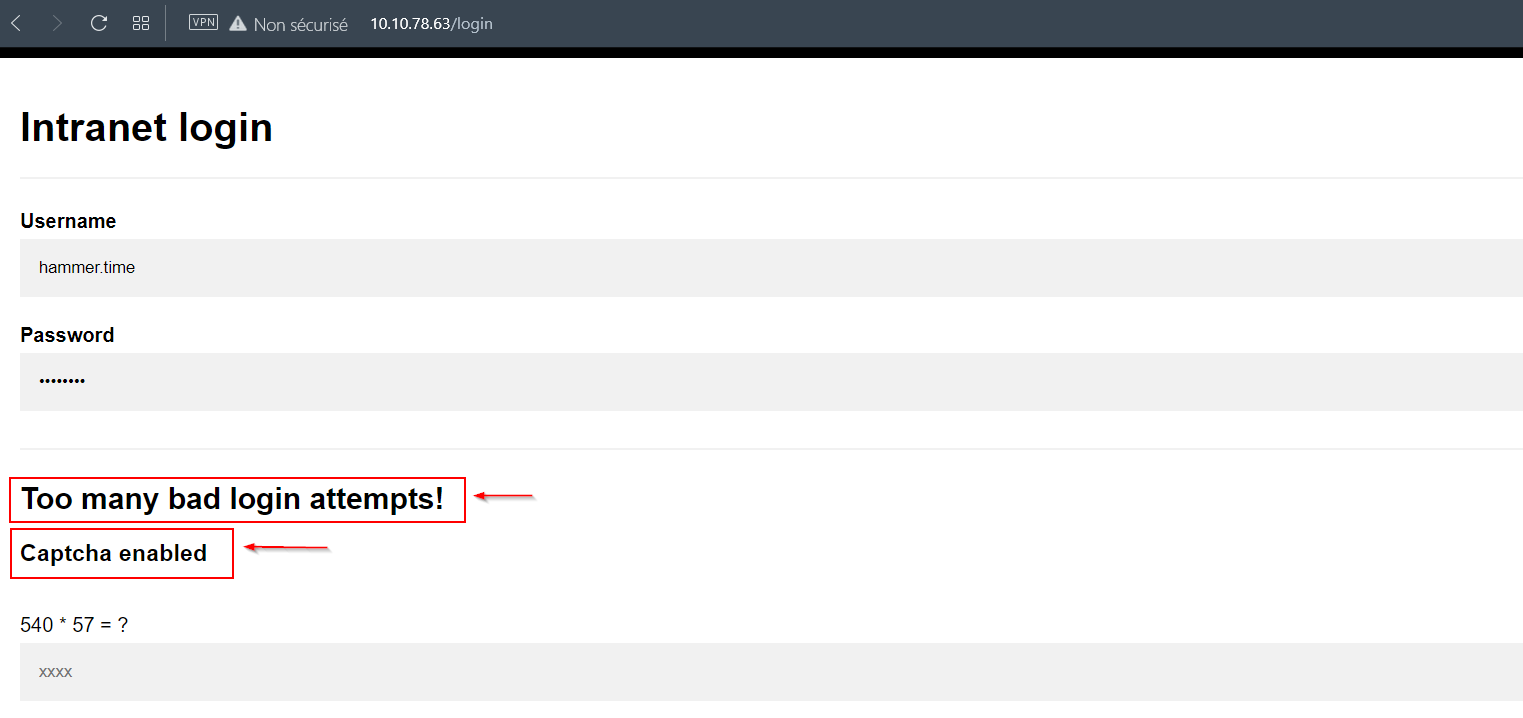
After 10 unsuccessful login attempts, a captcha will be enabled.
I created a python script to automate the process of username enumeration, password brute forcing and solving mathematical-based captcha.
You can find the script here Python script
So basically this python script automates the process of enumerating the username, if the response contains “Captcha enabled”, the eval() method will answer the mathematical operation.
The eval() method parses the expression passed to this method and runs python expression (code) within the program.
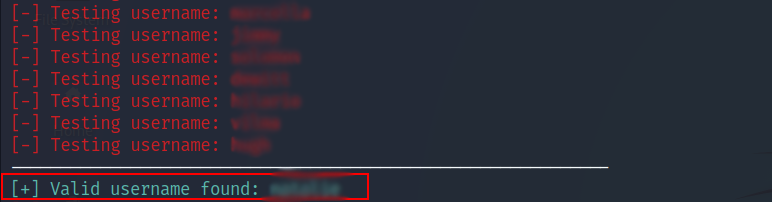
- After successfully identifying a valid username, the script will initiate a brute force attack to find the password associated with that username.
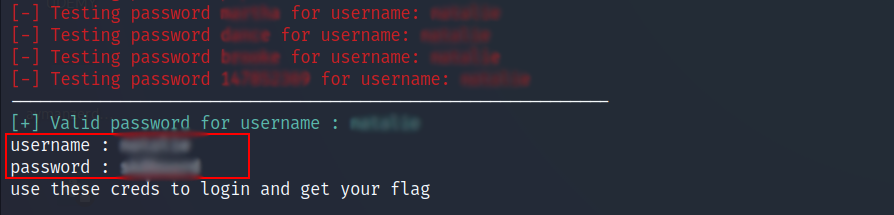
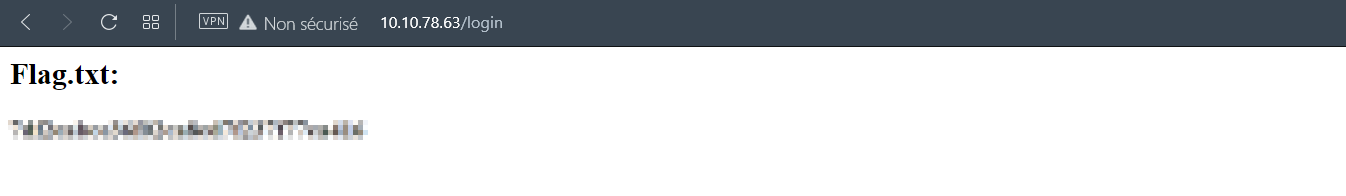
- Use these credentials to login and get your flag