Basic Static Analysis
Published in 02-14, 2023

Link: Basic static Analysis
Description:
Learn basic malware analysis techniques without running the malware.
FLARE VM is attached to this room for performing practical tasks.
TASK3: String search :
- Malware authors use several techniques to obfuscate the key parts of their code. These techniques often render a string search ineffective
- FLOSS uses several techniques to deobfuscate and extract strings that would not be otherwise found using a string search
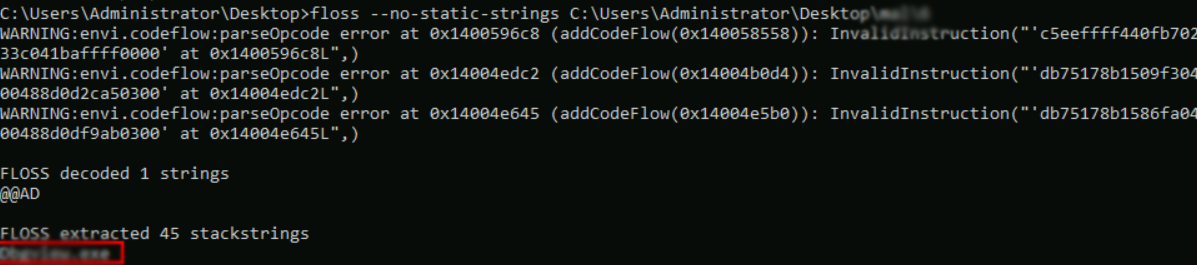
there is a directory named ‘mal’ with malware samples 1 to 6. Use floss to identify obfuscated strings found in the samples named 2, 5, and 6. Which of these samples contains the string ‘DbgView.exe’?
C:\Users\Administrator\Desktop>floss --no-static-strings C:\Users\Administrator\Desktop\mal\6
TASK4: Fingerprinting malware :
- The imphash is a hash of the function calls/libraries that a malware sample imports and the order in which these libraries are present in the sample
We can use PEstudio to calculate the Imphash of a sample.
- A Fuzzy Hash is calculated by dividing a file into pieces and calculating the hashes of the different pieces
- We can use SSDEEP to calculate the fuzzy hash.
which of the samples has the same imphash as file 3?
mal3 imphash: 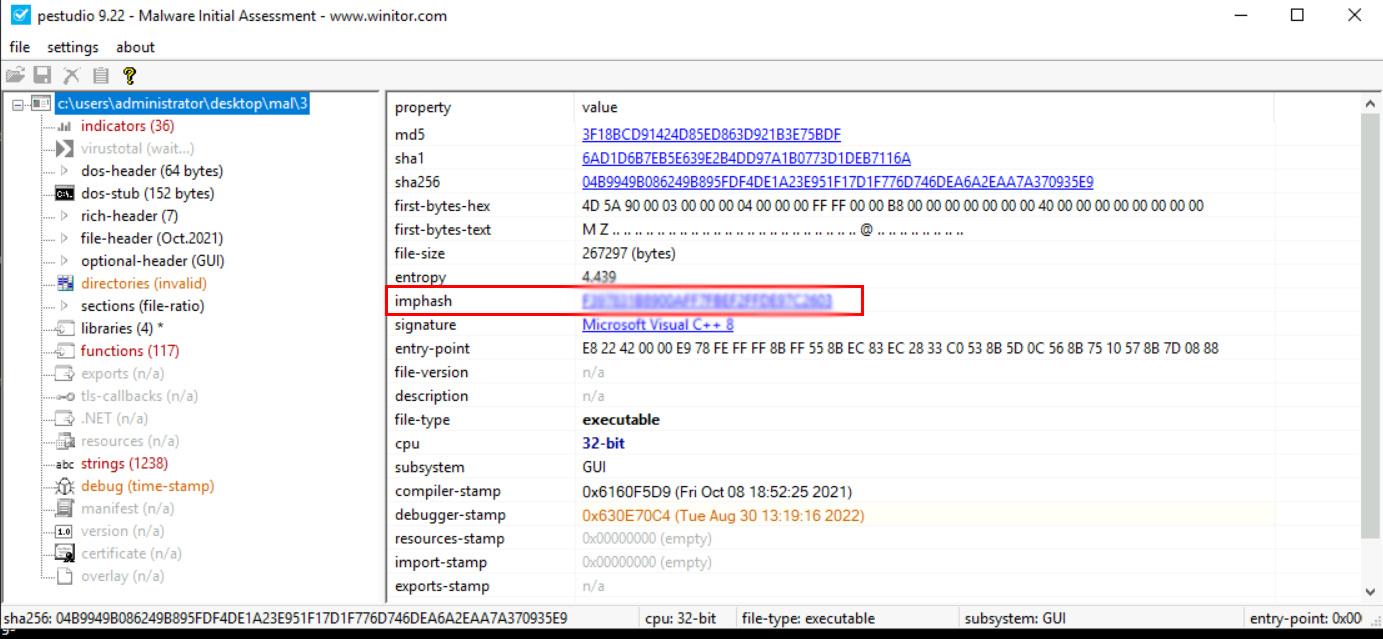 mal1 imphash:
mal1 imphash: 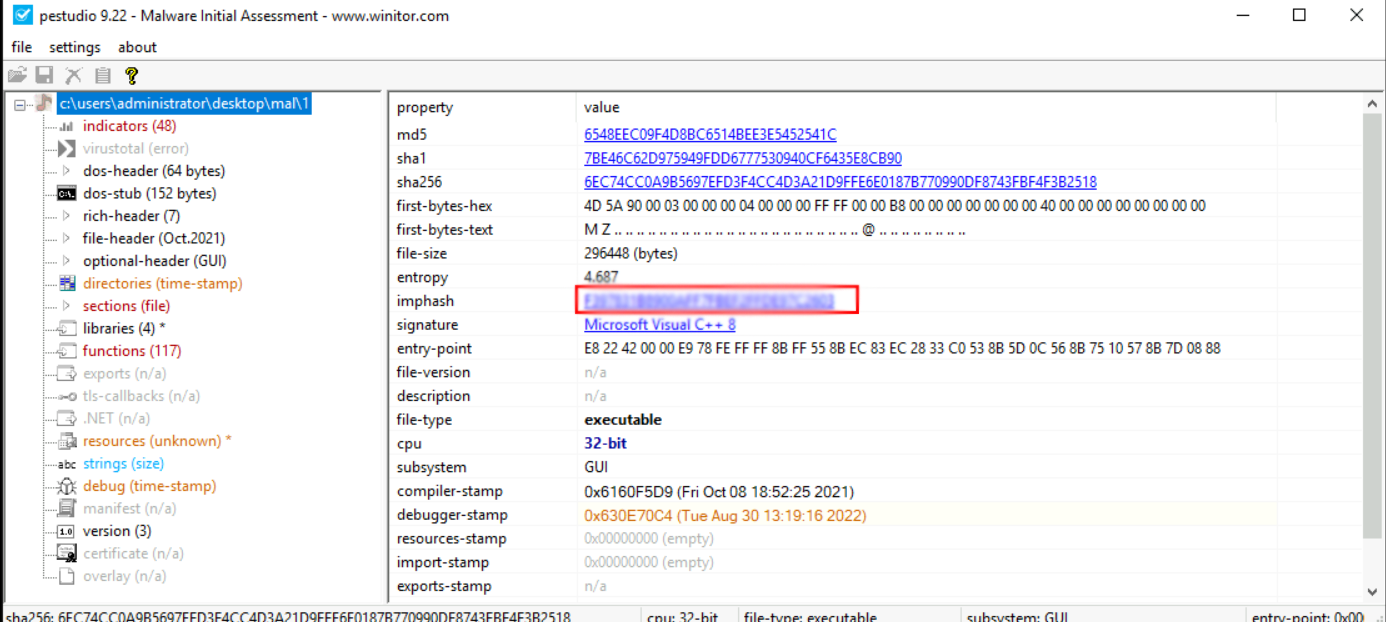
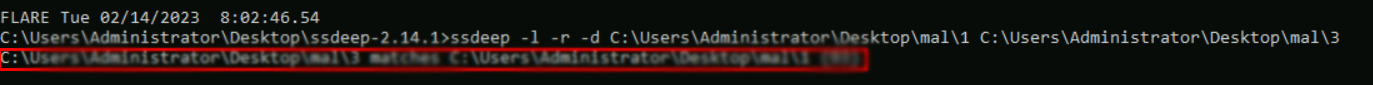
Using the ssdeep utility, what is the percentage match of the above-mentioned files?
ssdeep -l -r -d C:\Users\Administrator\Desktop\mal\1 C:\Users\Administrator\Desktop\mal\3
TASK5: Signature based Detection :
Signatures are a way to identify if a particular file has a particular type of content.
Capa is a tool used to identify the behavior of the file based on signatures such as imports, strings, mutexes, and other artifacts present in the file.
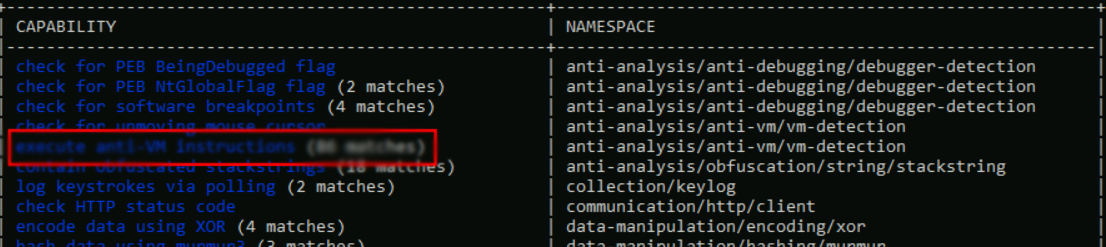
How many matches for anti-VM execution techniques were identified in the sample?
C:\Users\Administrator\Desktop>capa mal\4
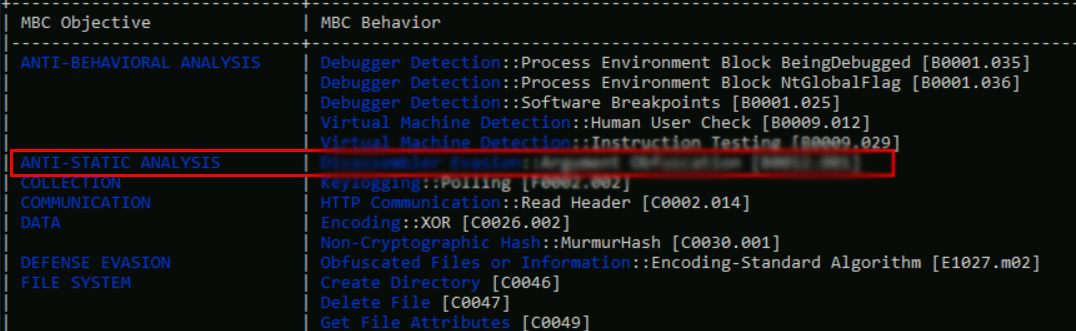
What MBC behavior is observed against the MBC Objective ‘Anti-Static Analysis’?
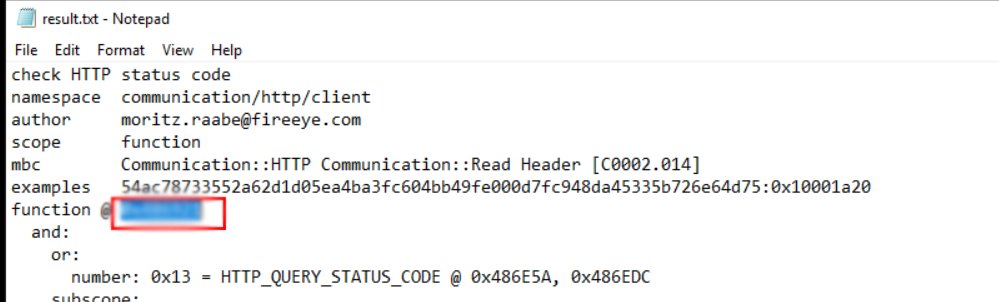
At what address is the function that has the capability ‘Check HTTP Status Code’?
C:\Users\Administrator\Desktop>capa -vv mal\4 > result.txt
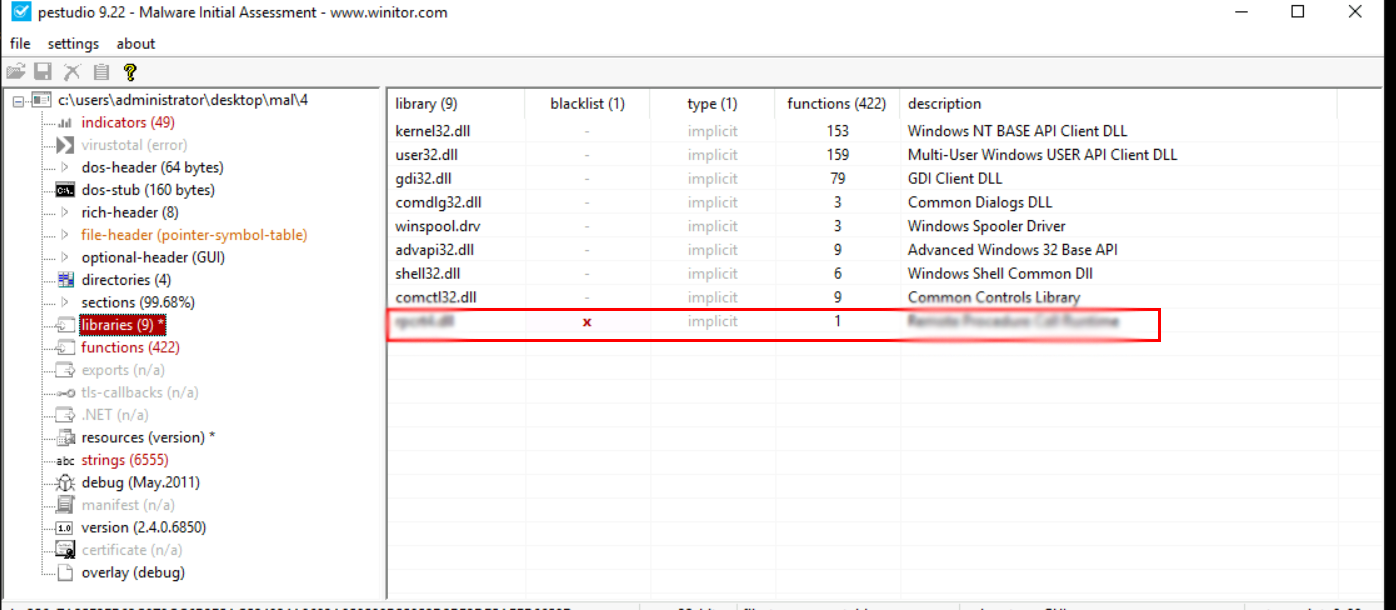
TASK5: Leveraging the PE header :
- The PE header contains information about the libraries that a PE file uses and the functions it imports from those libraries.
Open the sample Desktop\mal\4 in PEstudio. Which library is blacklisted?